Cloud technology has revolutionized the way healthcare organizations do business. From electronic health records (EHRs) to telemedicine platforms, providers now rely on the cloud to provide faster, more accessible, and more innovative patient care. The benefits are clear: scalability, operating efficiency, and infrastructure cost reduction.
But those advantages come at a great cost. Cloud security in healthcare is no longer just an IT concern. It’s about keeping sensitive patient data safe, complying with regulatory requirements, and offering seamless care. The result can be a catastrophe for patients, multimillion-dollar fines, and permanent harm to trust. The problem for healthcare organizations is not if, but how to go to the cloud. How to secure it with a balance between compliance, risk, and return on investment (ROI).
Why Cloud Security in Healthcare Matters More Than Ever
According to a report, healthcare has the most expensive cost per breach – $10.93 million per occurrence – among all industries. Unlike other industries, data is not the only thing that gets lost in these breaches. They affect lives. There is a lot of data to lose, with research data sometimes incurred with penalties, but if data is compromised or PHI is exposed, the effects of treatment delays can go well past the IT department.
The use of multi-cloud and hybrid environments has gained speed after the pandemic. Yet without strong cloud security in healthcare, risks expand rapidly.
- 20% of cloud misconfiguration breaches are against healthcare organizations.
- In large enterprises, 30-40% of IT spend is linked to shadow IT, which leaves blind spots that attackers can exploit.
- The healthcare cloud computing market is expected to expand at a CAGR of 17.6% to grow from USD 63.55 billion in 2025 to USD 197.45 billion by 2032.
Together, these trends prove that improving cloud security in healthcare is not optional. It’s a strategic imperative for reliability, compliance, and continuity of operations.
Security Challenges in Healthcare Cloud Computing
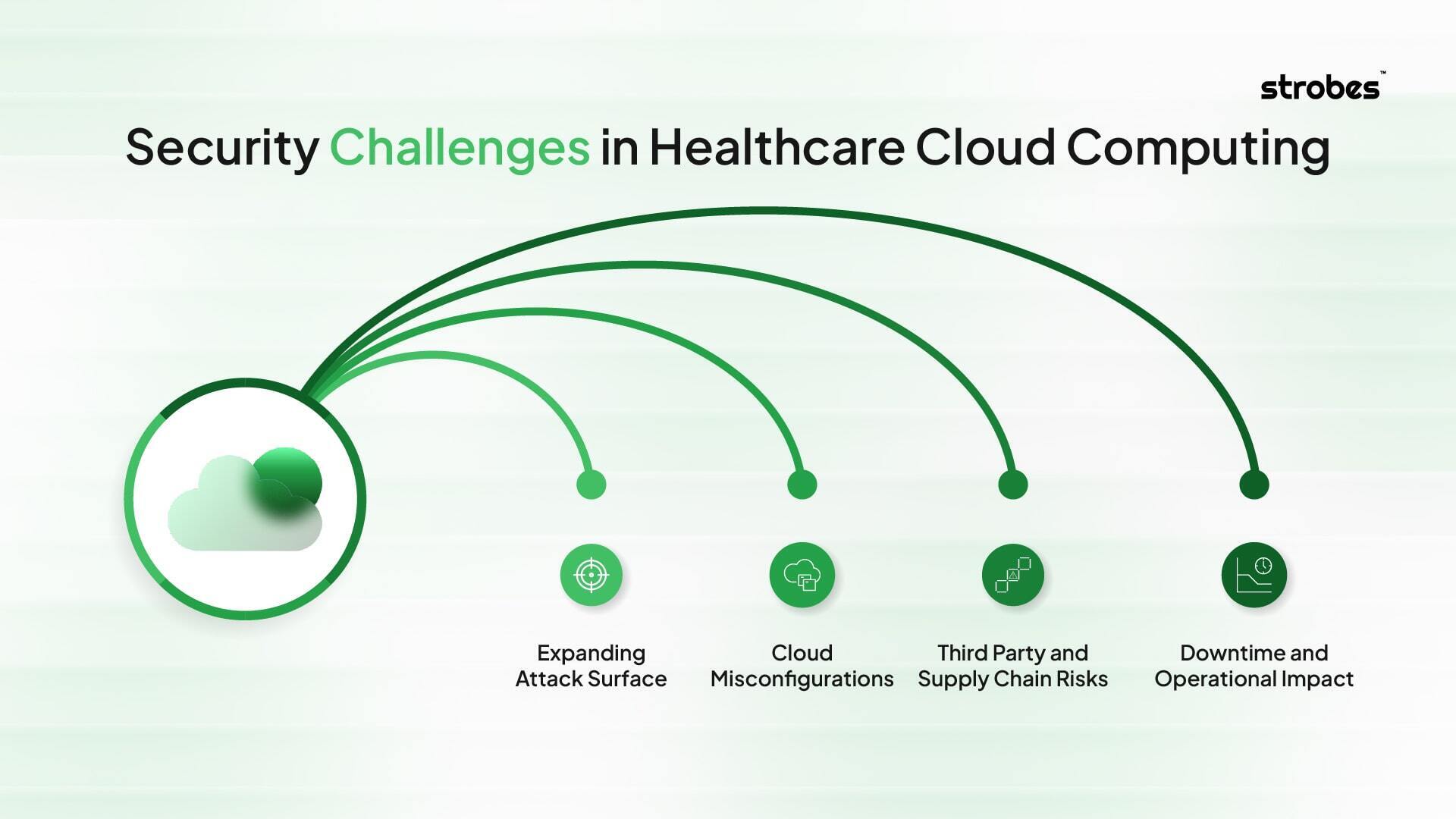
Healthcare organizations are perhaps some of the most challenging industries to migrate critical systems and sensitive data to the cloud. Unlike other industries, the stakes involved here are not mere compliance and revenue – but patient outcomes.
Expanding Attack Surface
Every new piece of digital technology creates yet another door by which an attacker can enter. Electronic health records (EHR), telemedicine platforms, medical IoT devices, SaaS applications, and third-party integrations all increase cloud footprint. And many of these assets are not adequately inventoried or monitored, resulting in lost visibility. Without a unified view of this attack surface, cloud security in healthcare becomes a guessing game.
Cloud Misconfigurations
Misconfigurations are one of the biggest causes of data exposure. Overly permissive IAM role access, insecure APIs, and a lack of robust security on storage buckets (see S3 in AWS or Blob storage in Azure) result in many millions of PHI records being left exposed to the public internet. This report shows that of all industries that share exposed and sensitive data online, 20% of breaches caused by misconfiguration directly expose healthcare organizations, emphasizing how easily organizational attacks can be carried out through simple misconfigurations.
Third Party and Supply Chain Risks
Hospitals and providers depend on a wide network of partners, including insurers, billing systems, telehealth vendors, and lab systems. Every exposure is linked to inherited risk. If one vendor fails to become secure against attackers, attackers can pivot into the healthcare provider’s systems. Third-party exposures are increasingly being leveraged in ransomware campaigns as many of the most sensitive workflows systematically span organizational boundaries.
Downtime and Operational Impact
For hospitals, downtime is more than a nuisance–it can halt the delivery of care. The average cost of downtime in healthcare is estimated at $7,900 per minute, but the true cost is measured in delayed procedures and risk for patient safety. Recent attacks targeting cloud-based scheduling or e-prescription systems have already proven how attackers can cripple entire hospitals.
How Compliance Shapes Cloud Security in Healthcare?
Compliance is not only a legal requirement for healthcare, it’s a necessity. It’s the fundamental cornerstone of how cloud environments must be designed, monitored, and audited. In fact, cloud security in healthcare is shaped more by regulation than in almost any other sector.
HIPAA and HITECH as the Baseline
The Health Insurance Portability and Accountability Act (HIPAA) establishes the floor in the healthcare field. The Security Rule specifically requires organizations to protect electronic protected health information (ePHI) in a manner that safeguards the confidentiality, integrity, and availability of the information. In cloud environments, this means:
- Encryption for all patient data at rest and in transit.
- Multi-Platform audit log entries that create a record of who can access what and catch unauthorized attempts
- Business Associate Agreements (BAAs) with cloud providers to reinforce cloud providers’ shared responsibility for protecting PHI.
The HITECH Act extends HIPAA to require notifications of breaches and increase enforcement. For cloud workloads, this implies that certain elements (automated monitoring, real-time detection, reporting, etc.) should be completely integrated into the infrastructure.
Regulations Beyond HIPAA
The pressures of compliance don’t stop at HIPAA:
- The 21st Century Cures Act mandates interoperability and secure APIs, creating new risks as PHI moves between systems hosted on the cloud.
- Consumer rights management, as required by privacy laws such as CCPA and CPRA, requires providers to manage deletion and access requests across a heterogeneous collection of cloud workloads.
- NIST Cybersecurity Framework and CIS Benchmarks become de facto best practices and security baselines for the cloud.
Automated Continuous Compliance
Compliance in the cloud cannot be static. Traditional annual audit is a poor metric in dynamic environments where assets, workloads, and integrations evolve daily. Instead, there is only one sustainable solution:
- Cloud Security Posture Management (CSPM) products scan cloud environments for CIS benchmarks and HIPAA requirements. Open S3 buckets or other weak IAM roles are flagged in real time.
- Automated compliance reporting establishes audit-ready evidence for HIPAA, HITECH, and state law compliance audits, going from months to minutes of preparation time.
- Risk-based compliance mapping links vulnerabilities to specific groups of regulatory requirements. For example, missing encryption controls are connected to HIPAA 164.312(a)(2)(iv), so teams can remediate using the regulatory context.
Why Compliance and Security Need to Go Together
Some providers still approach compliance as a checkbox activity. In reality, cloud security in healthcare requires a compliance-first design. Regulations also dictate the way in which encryption is deployed, access logs are kept, data is distributed, and breaches must be reported upon. Without integrating these into the day-to-day brand, organizations run the risk of not only regulatory fines but also patient trust.
Compliance goes well beyond cloud security. It has become the blueprint on how healthcare organizations should architect, operate, and continuously improve their cloud environments.
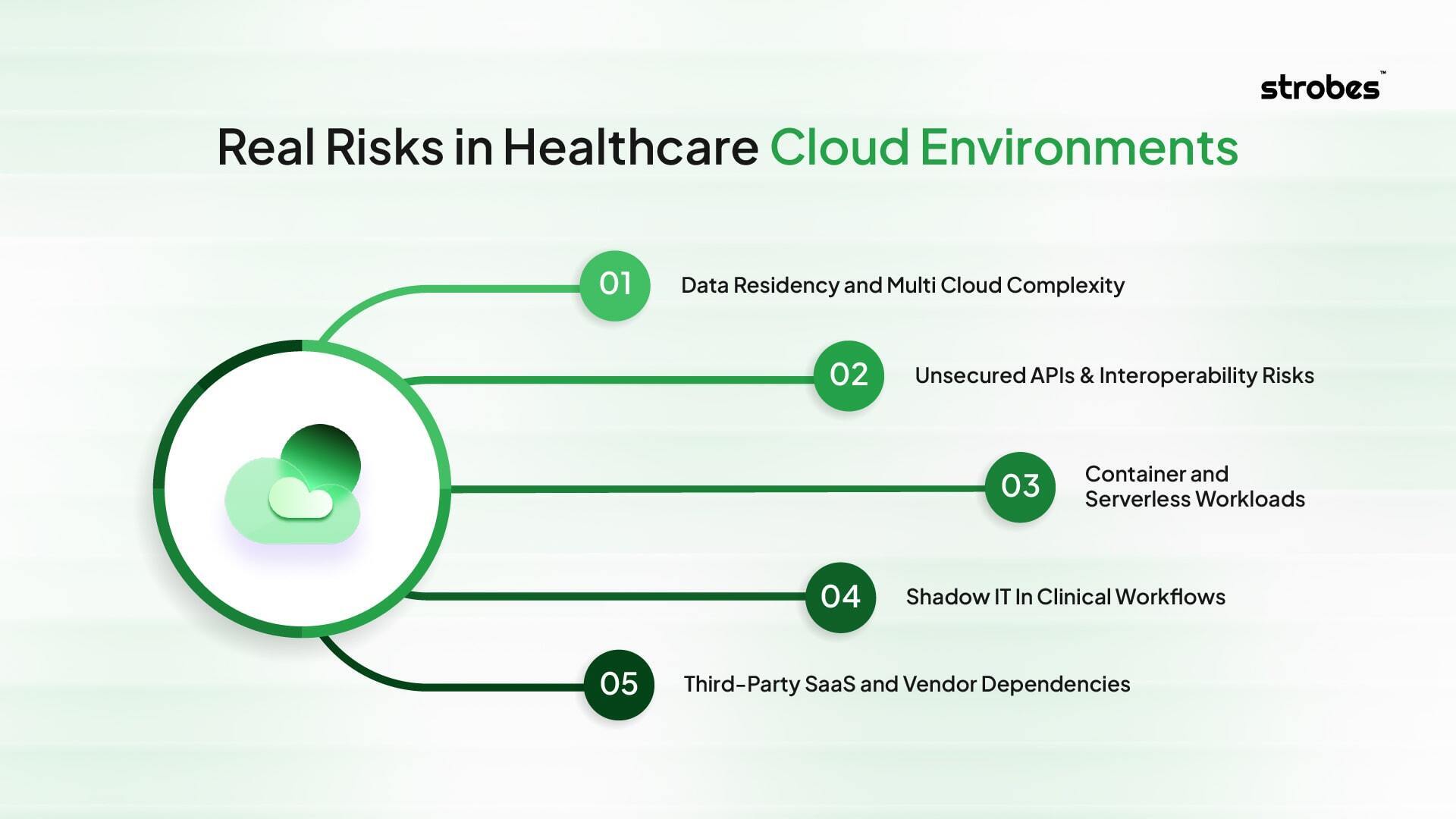
Understanding the Real Risks in Healthcare Cloud Environments
The risks for cloud adoption within healthcare are much more than simple misconfigurations. They apply to infrastructure, applications, and third-party integrations, and they need to be monitored on an ongoing basis.
Data Residency and Multi Cloud Complexity
AWS, Azure, and Google Cloud are used together in many healthcare systems. Every cloud has its own security controls, IAM models, and compliance frameworks. It is that misalignment that leaves gaps for attackers to exploit. For instance, IAM policies with the wrong level of permissions in the cloud may no longer be least-privilege compliant in another.
Unsecured APIs & Interoperability Risks
There has been broad adoption of APIs to support interoperability as a result of the 21st Century Cures Act and patient access mandates. Unpatched or improperly patched APIs can spill PHI or allow lateral movement in critical systems.
Container and Serverless Workloads
Containers and serverless functions are used extensively for contemporary healthcare applications. Without container image scanning and without runtime security protections, these deployments can contain unpatched vulnerabilities or malicious code.
Shadow IT In Clinical Workflows
Cloud-based SaaS solutions are often implemented in business departments without IT oversight. Shadow applications: Applications that are used to process PHI, but don’t have encryption, MFA, or compliance mapping.
Third-Party SaaS and Vendor Dependencies
Billing systems, insurance integrations, and telemedicine platforms are often in a position beyond the direct control of the security team. If a partner’s environment is compromised, that can hoist the healthcare network above ground.
This is why cloud security in healthcare cannot rely on periodic scans alone. It involves ongoing attack surface inventory, API monitoring, runtime workload analysis, and vendor risk assessments.
A Framework for Strengthening Cloud Security in Healthcare
Audits and ad hoc tools won’t suffice. They require an iterative and ongoing strategy where visibility, prioritization, compliance, testing, and secure development all support one another.
Persistent Visibility with Attack Surface Management
You cannot defend what you cannot see. Attack Surface Management (ASM) makes it easy to discover and monitor all assets in the cloud in real time.
- Detect domains, subdomains, APIs, IPs, certificates, and cloud workloads.
- Identify shadow IT applications in use beyond IT control
- Map assets to business functions for greater context
- Constantly enhanced attack surface monitoring, not just scanning now and then.
Risk-Based Vulnerability Management for Prioritization
All vulnerabilities are not created equal. Risk-Based Vulnerability Management (RBVM) is an approach to prioritize those activities that are most important.
- Combine vulnerabilities with exploitability and active threat intelligence
- Prioritize risk based on business impact, asset sensitivity, and compliance exposure.
- Eliminate noise through vulnerability deduplication across multiple scanners
- Zero in on the top 3% of vulnerabilities with the highest risk
Connect with Security Posture Management in the Cloud
Compliance in healthcare cloud environments is an ongoing, not a one-time, thing. The automated process is provided by Cloud Security Posture Management (CSPM).
- AWS and Azure Accounts Audit against CIS and HIPAA compliance controls
- Identify misconfigurations, such as open buckets, weak IAM policies, or unencrypted databases.
- On-demand generation of audit-ready reports to simplify HIPAA, HITECH, and SOC 2 compliance.
- Put the policies in place and notify teams in real time.
Strength Testing combined with Cloud Penetration Testing
Scanners only go so far. Cloud penetration testing tests defenses in the wild.
- Simulate Privilege Escalation, data exfiltration, and ransomware attacks
- Detect IAM misconfigurations, weak authentication, and overprivileged access.
- Uncover vulnerabilities in Kubernetes clusters and containerized workloads
- Verify remediation actions based on re-testing, not just reporting
Building Secure Development with Application Security Posture Management
Applications are the driving force in healthcare today, but they are also creating supply chain and coding risks. Application Security Posture Management (ASPM) adds security to the development pipeline.
- Perform Static Application Security Testing (SAST) to detect insecure coding at early stages.
- Perform SCA (Software Composition Analysis) for vulnerability tracking of open source libraries.
- Keep a Software Bill of Materials (SBOM) that gives visibility into dependencies.
- Integrate into CI/CD pipelines to provide developers with feedback.
Why This Framework Works
When these five pillars work together, healthcare builds a proactive cloud security in healthcare model that delivers:
- Full visibility of all assets and risks
- Focused prioritization on vulnerabilities that are worth paying attention to
- Complete compliance management that is automatic, not manual.
- Visible proof of defenses surviving real-world attacks
- Applications protected from code to cloud
This framework is more than a checkbox compliance model. It’s closely related to the mission of healthcare, protecting patients, maintaining trust, and continuity of care.
Best Practices for Cloud Security in Healthcare
- Maintain a single source of the truth asset inventory across AWS, Azure, GCP, and private clouds – including shadow IT and SaaS applications – with automated discovery and tagging for systems that contain PHI
- Risk-based vulnerability management that combines CVSS scores with exploitability, threat intelligence, and business impact to prioritize the most critical assets
- Compliance Self-Assessment and Dashboard – Leverage CSPM to automate the process of enforcing CIS benchmarks, identifying misconfigurations in real time, and producing HIPAA and HITECH-ready reports.
- Continuous testing with PTaaS and cloud penetration testing to validate IAM controls, identify insecure storage, and simulate real-world threats like ransomware
- Secure applications and components before they can be exposed to production by integrating security within development pipelines with SAST and SCA.
- Develop and test cloud-specific incident response playbooks around stolen keys, misconfigured buckets, and cloud-native attack patterns.
With these best practices in place, cloud security in healthcare becomes more than just a reactive defense mechanism; it’s a proactive approach to building resilient, compliant, and patient-trusting systems that ensure operational continuity.
Conclusion
The adoption of cloud in healthcare is only seeing an increase. Each new application, device or partner is a source of value but also adds exposure. The real test is striking a balance between compliance, risk, and ROI without hindering care delivery.
Strong cloud security in healthcare is not only about avoiding breaches. This not only reinforces the trust of patients but also ensures that services are occurring, while also creating space for innovation.
With a platform like Strobes, healthcare providers can have continuous visibility, smarter risk prioritization, and automated compliance reporting, all at a single point of truth. The result is efficient and robust security that protects patients.
Book a free demo today to see how Strobes can strengthen your healthcare cloud security.