Let me be real with you.
2025 wasn’t about launching a hundred features and patting ourselves on the back. It was about asking one uncomfortable question: Are we actually helping security teams reduce exposure, or are we just giving them another dashboard to stare at?
The answer shaped everything we built this year.
Gartner predicts that by 2026, organizations prioritizing security investments through a continuous exposure management program will be 3x less likely to suffer a breach. That’s not a small number. That’s the difference between being in the news for the right reasons or becoming another cautionary tale in next year’s breach report.
So we did something different. We rebuilt Strobes from the ground up as a unified CTEM execution platform. Not another point solution, not another tool in an already crowded stack.
Here’s what that actually means.
The Problem Nobody Wants to Admit
Security teams are drowning. Not in threats, but in tools.
In dashboards, exports, spreadsheets, and “urgent” tickets that all look the same when context is missing.
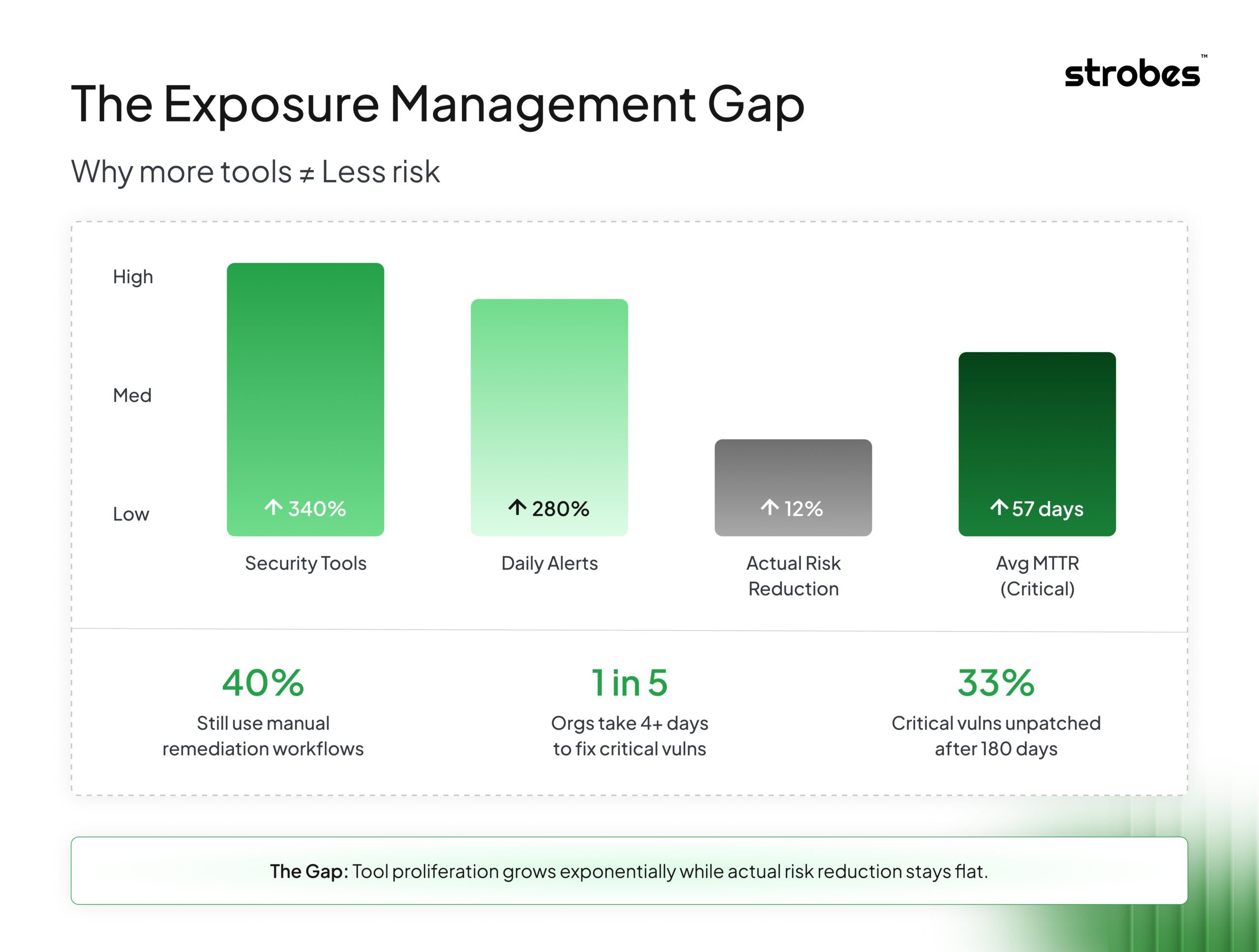
Here’s a stat that should make every security leader uncomfortable. Nearly 40% of organizations still rely on manual workflows for most of their vulnerability remediation processes. In 2025. When attackers are using AI to generate exploits faster than most teams can triage their morning alerts.
The average time to remediate a critical vulnerability? Still measured in days for 1 in 5 organizations. Meanwhile, exploitation timelines have compressed to hours.
This isn’t a tooling problem. It’s an operating model problem.
The traditional approach of buying a scanner, buying a pentesting engagement, buying a cloud security tool, buying an ASM solution creates exactly what it promises. A collection of tools. Not a program. Not a system. Definitely not continuous exposure management.
What happens in reality:
- No single source of truth. Your VM tool says one thing, your cloud scanner says another, and your pentest report is sitting in someone’s inbox from three weeks ago.
- Duplicate work everywhere. The same vulnerability shows up in three different tools, gets triaged three times, and maybe gets fixed once.
- Remediation cycles that drag on forever. Findings bounce between security, DevOps, and infrastructure teams with no clear ownership and no workflow state anyone trusts.
We built Strobes to fix this.
One Platform That Turns Modules Into Mission Control
In 2025, we made the most significant architectural decision in our company’s history.
Strobes became one platform instead of a collection of modules.
When you land on the Strobes CTEM dashboard, you see:
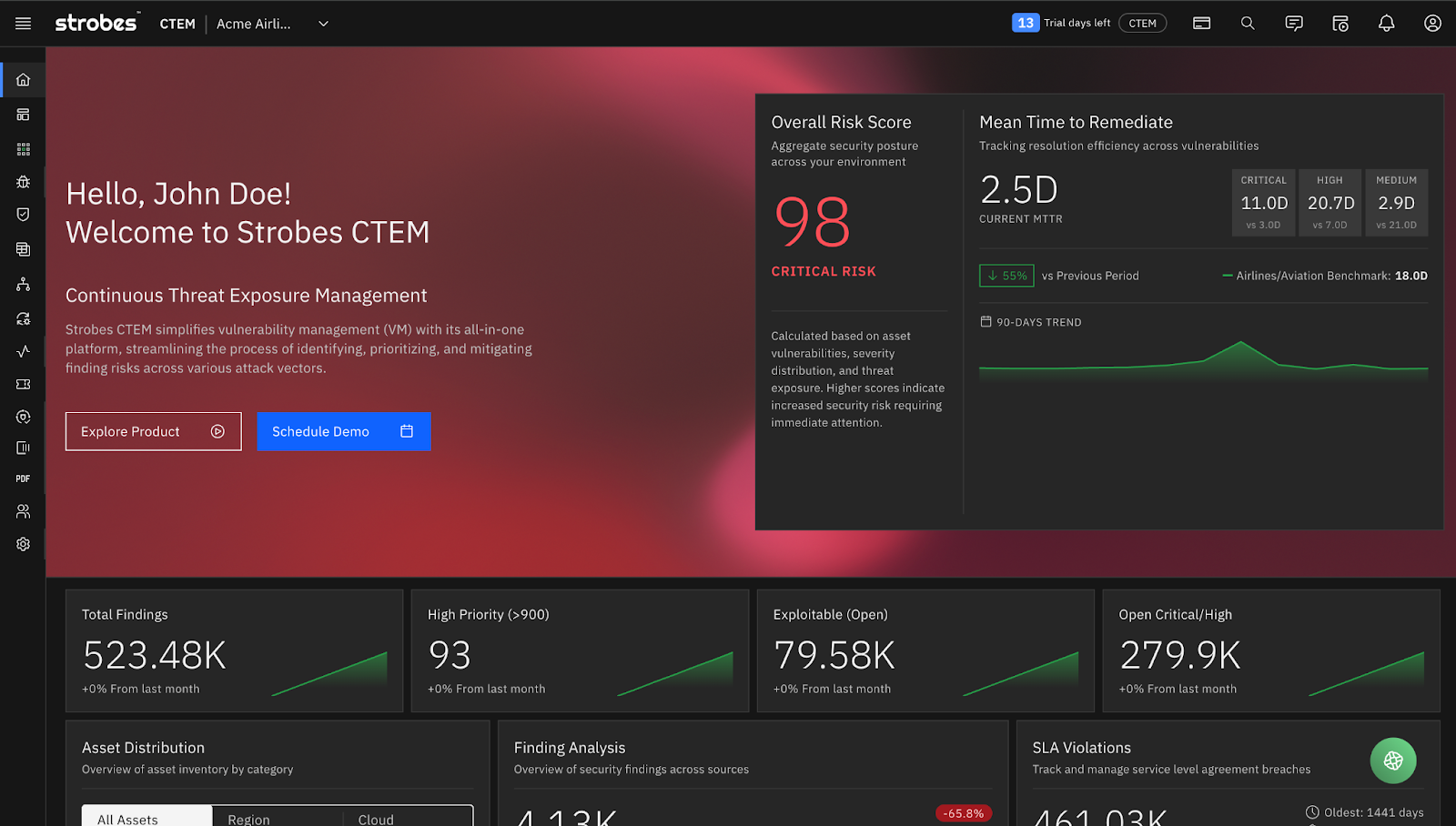
Overall Risk Score.
A single number that represents your current exposure state. Not just a count of vulnerabilities, but a contextualized score that factors in asset criticality, exploitability, and business impact. In the screenshot above, that’s a 98. Critical. One number that tells leadership exactly where you stand.
Mean Time to Remediate (MTTR).
Broken down by severity. Critical issues were remediated in 2.5 days. High in 11 days. Medium in 20.70 days. You can immediately see where your process is working and where it’s breaking down.
Exposure Metrics at a Glance:
- 523.48K total findings across all sources
- 93 high-priority findings requiring immediate attention
- 79.58K exploitable findings that represent real risk
- 279.9K critical and high-severity findings
SLA Violations.
461.03K findings with SLA status tracked. You know exactly what’s overdue, what’s at risk, and what’s on track.
Integration Status.
See which scanners and connectors are active, which need configuration, and what percentage of your tooling is actually feeding data into the platform.
Top Vulnerabilities and CVE Trends.
Real-time intelligence on what’s actively being exploited, what’s trending, and what matters most to your environment.
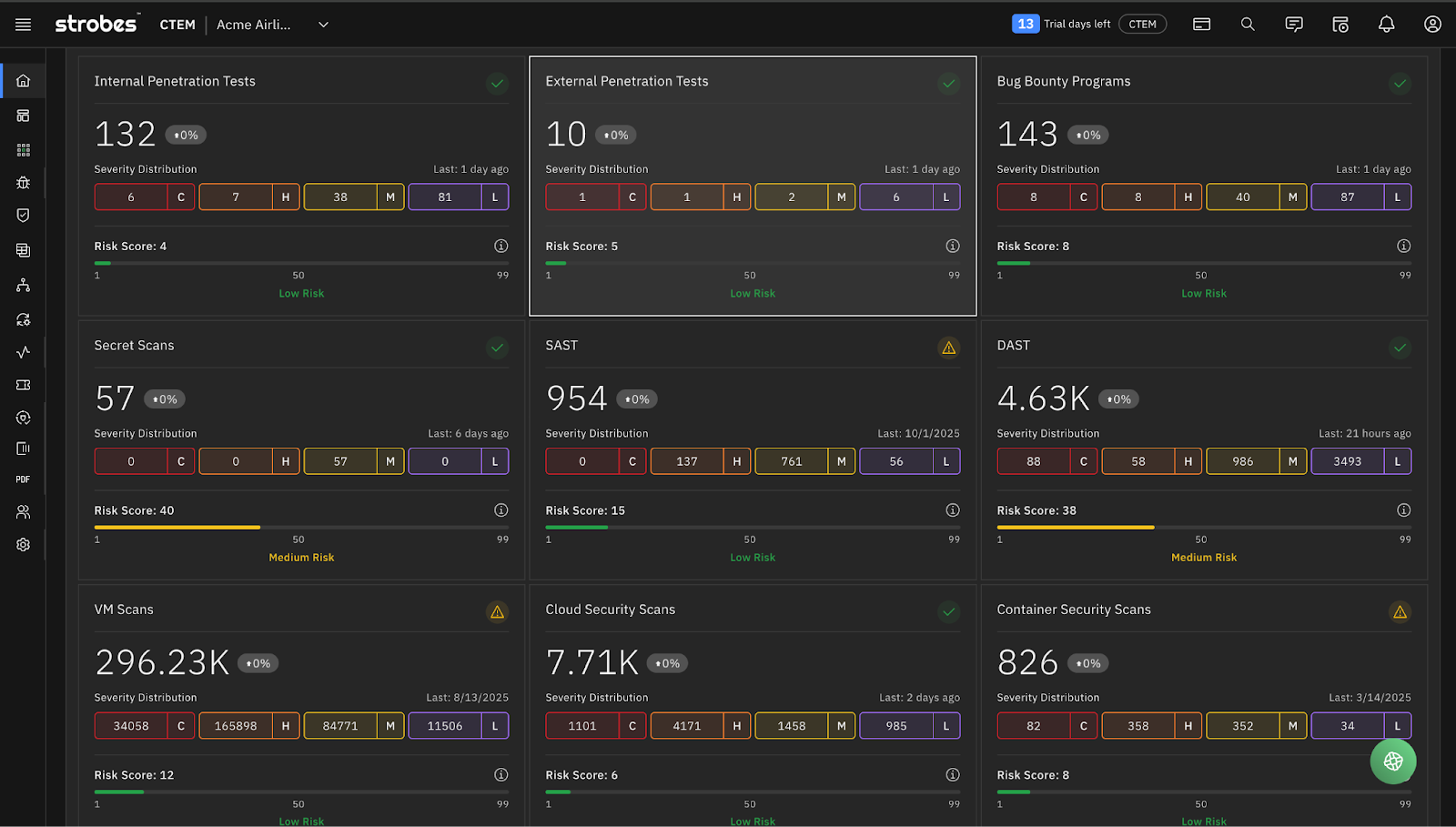
Program Metrics.
Internal pentests, external pentests, bug bounty submissions, red team findings, SAST results, API security scores. All in one view, with trend data showing whether you’re improving or regressing.
This isn’t a dashboard we built because dashboards are expected. It is the operational command center for teams that are serious about reducing exposure, not just measuring it.
This wasn’t a rebrand. This wasn’t putting a new wrapper around the same old capabilities. This was a fundamental rethinking of how exposure management should work.
The CTEM framework gives us five phases: Scoping, Discovery, Prioritization, Validation, and Mobilization. Most vendors pick one or two and call it a day. We built for all five.
 What This Looks Like in Practice
What This Looks Like in Practice
Scoping: You define what matters, not just assets, but business context. Which systems drive revenue? Which environments hold customer data? Strobes lets you model your actual attack surface based on business criticality, not just IP ranges.
Discovery: We unified how findings enter the platform. Cloud misconfigurations from Defender, DAST results from Acunetix, manual pentest findings from your red team, API vulnerabilities from your own assessments, they all flow into the same system, normalized and correlated.
Prioritization: This is where most tools fail. They give you CVSS scores and call it a day. But a high CVSS vulnerability on a staging server nobody uses should not compete with a medium-severity finding on your payment processing system. We built prioritization that factors in asset criticality, exploitability, and business impact, because that is what real risk looks like.
Validation: Before you spend cycles on remediation, you need to know the finding is real and exploitable. Our integrated validation workflows let you confirm exposure without context switching between platforms.
Mobilization: Findings that do not reach remediation do not matter. We built workflows that push directly into GitHub Issues, sync with Jira, and track closure end to end. No more findings sitting in a dashboard waiting for someone to notice them.
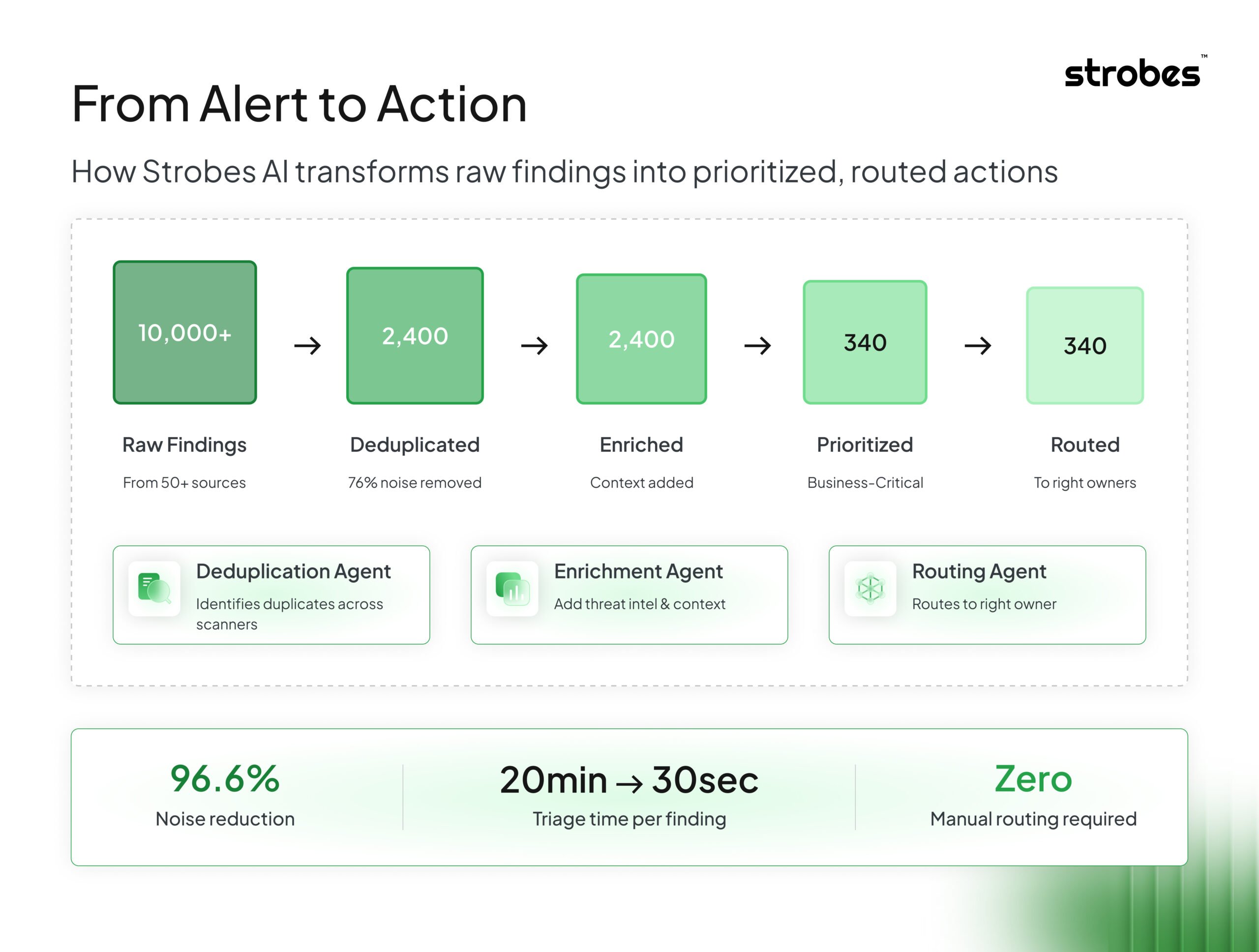
Strobes AI Turns Automation into Real Work Reduction
Here’s my problem with most “AI-powered” security tools: they add complexity, not reduce it.
You end up with another interface to manage, another set of results to validate, and another thing generating alerts that need human review. The promise of AI was supposed to be less work, not more work in a different format.
So when we built Strobes AI, we started with a simple filter: Does this actually reduce the manual work security teams are doing today?
If the answer wasn’t clearly yes, we didn’t ship it.
What Strobes AI Actually Does
Intelligent Triage and Deduplication
The same vulnerability showing up across multiple scanners and assessments is one of the biggest time sinks in security operations. Strobes AI identifies and correlates duplicate findings automatically, so your team sees one issue to fix, not five copies of the same problem across different tools.
Contextual Enrichment
When a finding arrives, Strobes AI enriches it with relevant context: related vulnerabilities, historical data about similar issues in your environment, and known exploitation patterns. This is not about generating more data. It is about making the data you have more actionable.
Smart Routing
Getting findings to the right owner should not require a project manager. Strobes AI learns from your remediation patterns and suggests routing based on asset ownership, historical fix assignments, and team capacity.
Custom Risk Prioritization Built Around How Your Business Actually Works
Here’s something that frustrates me about the security industry. We keep trying to solve prioritization with universal formulas.
CVSS is useful. EPSS is useful. But neither of them knows that your organization considers the marketing website less critical than the internal HR system, even though the marketing site has a larger attack surface and more public exposure.
Risk is not just technical severity. It is technical severity weighted by business context.
In 2025, we continued investing in custom prioritization that reflects how your organization actually thinks about risk.
- Asset criticality tiers you define
- Business impact scoring based on data classification
- Threat context specific to your industry and attack patterns
- SLA policies that vary by asset type and exposure level
The goal is simple. When your team looks at their queue, the things at the top are the things that actually matter most to your business. Not the things that scored highest on a generic severity calculator.
Customizable Engagement Workflows Designed for Real-World Security Work
“Open” and “Closed” are not enough.
Real security operations have states like:
- Awaiting Retest
- Validated by Security
- Blocked by Change Freeze
- Pending Evidence
- Escalated to Engineering Lead
Every organization defines these differently. Trying to force complex security workflows into generic status labels is how you end up with spreadsheets running parallel to your “official” tracking system.
In 2025, we shipped fully customizable engagement workflows:
- Define your own states that match how your teams actually work
- Create transition rules that enforce process (e.g., can’t move to “Closed” without validation)
- Build reports that reflect true progress, not approximations
When stakeholders share a common language for tracking work, you spend less time in status meetings and more time actually fixing things.
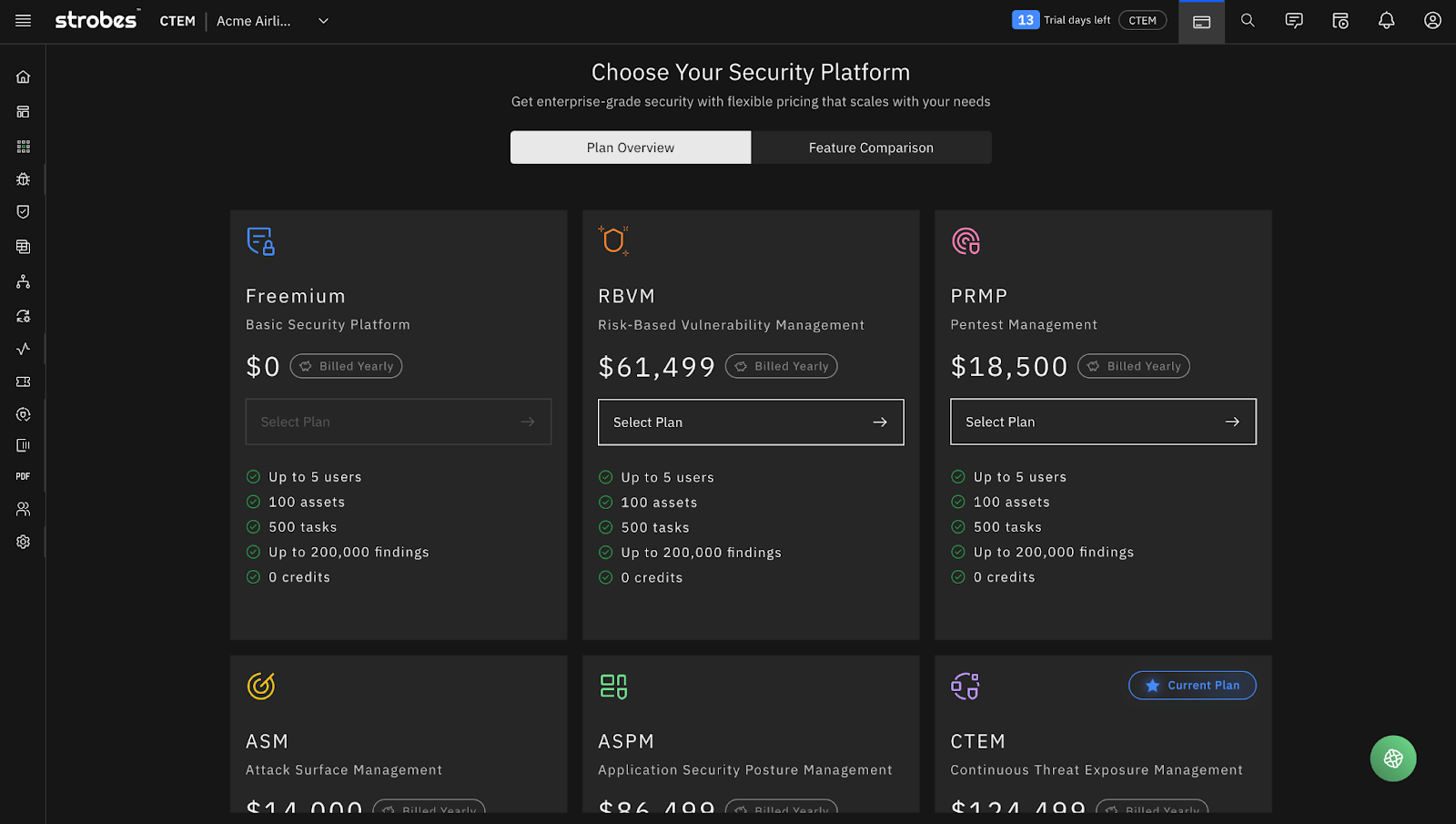
Simple Pricing that Aligns with Real Security Needs
Here’s something that always bothered me about enterprise security pricing: you need a procurement team and a three-month sales cycle just to figure out what something costs.
In 2025, we rebuilt our pricing model around a simple principle: you should be able to understand what you’re buying and what it costs without scheduling a call.
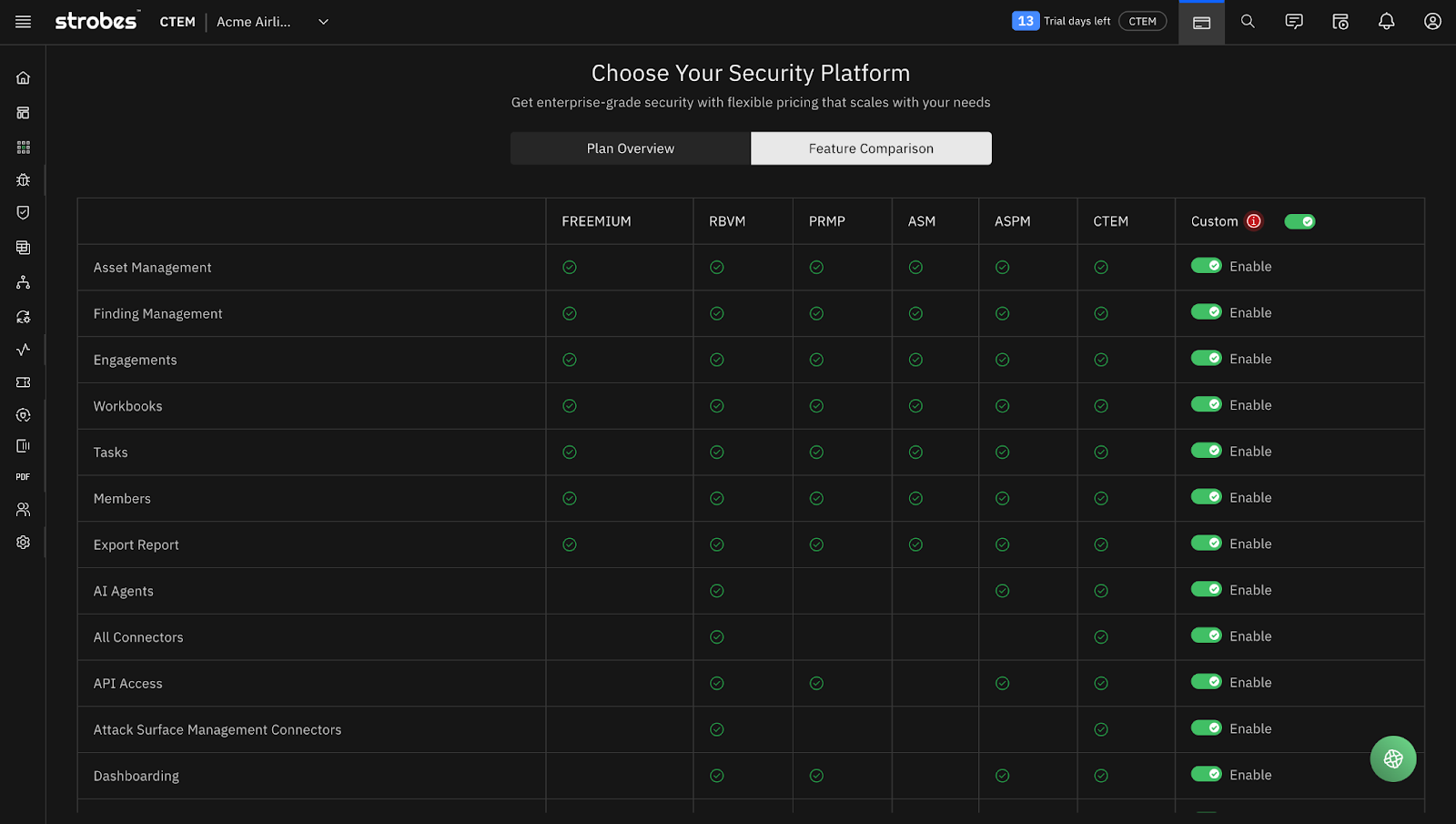
Six Plans, Clear Differentiation
Freemium. Seriously. Up to 5 users, 100 assets, 500 tasks, 200,000 findings. This isn’t a crippled trial. It is a real platform you can use to manage your security program. Perfect for small teams who want to see if Strobes fits their workflow before committing.
RBVM. Risk-Based Vulnerability Management. Everything in Freemium plus AI Agents, all connectors, API access, ASM connectors, and advanced dashboarding. For teams that have outgrown basic VM and need contextual prioritization.
PRMP. Pentest Report Management Platform. Built for teams that run regular penetration testing engagements and need structured workflow management, reporting, and remediation tracking.
ASM. Attack Surface Management. Continuous discovery and monitoring of your external-facing assets. Know what is exposed before attackers do.
ASPM. Application Security Posture Management. Full AppSec lifecycle. SAST, DAST, SCA, API security. Managed in one platform with developer-friendly workflows.
CTEM. The full platform. Everything we have built, unified. Exposure Assessment and Exposure Validation across your entire attack surface. This is what continuous threat exposure management looks like when it is not fragmented across vendors.
Integrations That Make the Platform the Control Plane
Unification only works if your data can actually converge. We spent significant effort this year making Strobes the place where exposure signals come together, not another tool teams have to check separately.
Key Integrations Added in 2025
Microsoft Defender for Cloud
Cloud posture data shouldn’t live in its own silo. This integration brings cloud vulnerabilities, misconfigurations, and alerts into Strobes so you can manage cloud risk alongside everything else.
Acunetix
Automatic sync of DAST scan results. AppSec findings get triaged, prioritized, and tracked in the same workflow as your infrastructure vulnerabilities.
AccuKnox CSPM + DAST
Cloud posture and dynamic application testing signals in one workflow. No more switching between tools to get the full picture.
GitHub Issues Integration
Remediation needs to live where developers work. Two-way sync means findings pushed to GitHub stay aligned with status updates in Strobes.
Postman Collections + OpenAPI Imports
APIs are often the biggest blind spot. Importing API definitions gives teams visibility into endpoints and potential security gaps, especially critical in environments where APIs change constantly.
CycloneDX & SPDX (SBOM Support)
Software supply chain security isn’t optional anymore. With native CycloneDX and SPDX integration, Strobes now ingests Software Bill of Materials directly into your exposure management workflow. Track vulnerable components across your entire software supply chain, correlate SBOM data with known CVEs, and prioritize remediation based on actual deployment context, not just theoretical risk. When the next Log4Shell drops, you’ll know exactly which applications are affected within minutes, not days.
The Numbers That Show Why This Matters
Let me ground this in some industry context:
- Organizations adopting CTEM will be three times less likely to suffer a breach by 2026, according to Gartner.
- 33% of critical vulnerabilities remain unpatched for over 180 days. That window is often all attackers need.
- The global average cost of a breach reached 5.08 million dollars in 2025 based on IBM data.
- Security AI reduced breach costs by 34 percent, saving an average of 1.9 million dollars for organizations that deployed it effectively.
- By 2028, more than half of threat exposure findings will come from nontechnical vulnerabilities, according to Gartner. This means CTEM programs must expand beyond technical scanning alone.
The math is clear. Organizations that build continuous, contextualized exposure management programs outperform those still relying on point-in-time assessments and hoping for the best.
A Partner Portal Built for MSSPs at Scale
Security isn’t just an enterprise problem — it’s an ecosystem challenge. MSSPs, consultancies, and security service providers need tools that work across multiple clients without the operational nightmare of managing separate instances for each customer.
In 2025, we launched the Strobes Partners Portal — purpose-built for organizations that deliver security services at scale.
What Partners Get
Multi-Tenant Management One portal, all your clients. In the screenshot above, that’s 809 customers managed through a single partner dashboard. Each customer gets their own isolated environment with their own data, users, and configurations, but you get a unified view of your entire book of business.
License Tracking & Utilization 788 active licenses across 12 PTaaS services, with real-time utilization metrics. Know exactly how your customers are using the platform, where there’s capacity, and where you need to expand.
Utilization Breakdown See at a glance:
- Task utilization: 390%
- User utilization: 17%
- Asset utilization: 5%
- Vulnerability utilization: 7%
This tells you which dimensions are maxed out and where there’s room to grow — critical intelligence for pricing conversations and capacity planning.
PTaaS Services Integration For partners delivering penetration testing as a service, the portal integrates directly with your testing workflow. Manage engagements, track findings, and deliver reports — all through the same interface your analysts already use.
Training Academy Access Onboard your team with structured training. Partners get access to the Strobes Training Academy so new analysts can get productive quickly without consuming your senior resources.
Why This Matters for the MSSP Model
The traditional MSSP approach to vulnerability management is painful:
- Spin up a separate instance for each client
- Manage credentials and access across dozens of environments
- Manually aggregate data for reporting
- Lose visibility into cross-client trends
Strobes Partners flips that model:
- One platform, many tenants. Operational efficiency without sacrificing isolation
- Centralized visibility. See patterns across your client base
- Consistent workflows. Train your team once and apply it everywhere
- White-label ready. Your brand, your client relationships, our infrastructure
- If you’re an MSSP or security consultancy looking to scale your VM/CTEM practice, this is the operational backbone that makes it possible.
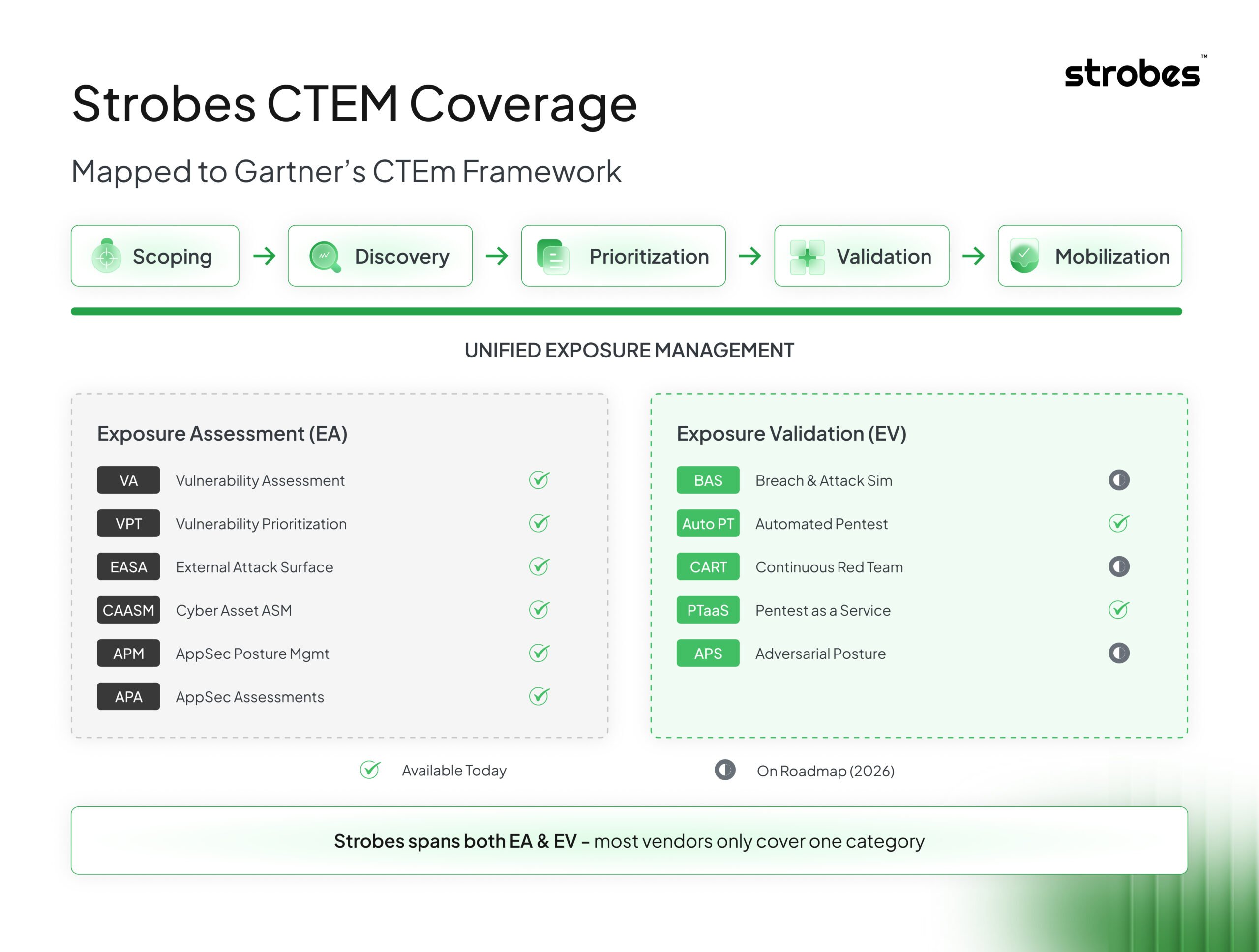
How Strobes Maps to Gartner’s CTEM Framework
Let’s get specific about where Strobes fits in the CTEM landscape.
Gartner’s CTEM framework defines two major technology categories under Unified Exposure Management:
Exposure Assessment (EA): The tools and processes that help you understand what’s exposed, including Vulnerability Assessment (VA), Vulnerability Prioritization Technology (VPT), External Attack Surface Assessment (EASA), Cyber Asset Attack Surface Management (CAASM), Application Security Posture Management (APM), and Application Security Assessments (APA).
Exposure Validation (EV): The tools that prove exposures are real and exploitable, including Breach and Attack Simulation (BAS), Automated Penetration Testing (Auto PT), Continuous Automated Red Teaming (CART), Penetration Testing as a Service (PTaaS), and Adversarial Exposure Validation (AEV).
Most vendors live in one box. Maybe two if they’ve done an acquisition recently.
Strobes spans both.
The Agent-Augmented Offensive Security Team
The security talent shortage isn’t getting better. The attack surface isn’t getting smaller. The only way forward is augmentation, human analysts working alongside AI agents that handle the tasks machines do better.
Consider the math:
- Manual vulnerability triage: 20+ minutes per finding
- Agent-assisted triage: Seconds, with human review for edge cases
- Traditional pentest cycle: 2–4 weeks
- Agent-driven continuous validation: Hours, on-demand
This isn’t about replacing security professionals. It’s about giving them leverage. One analyst managing a fleet of specialized agents accomplishes what previously required a team of five.
Gartner predicts that by 2028, more than half of threat exposure findings will come from nontechnical vulnerabilities. That means CTEM programs, and the tools that support them, need to evolve beyond traditional scanning. Agents that can reason about business context, validate complex attack chains, and adapt to new threat patterns aren’t a nice-to-have. They’re the only way to keep pace.
What Differentiates Strobes Now
Let me be direct about where we stand:
Strobes is a CTEM execution platform. Not a vulnerability scanner. Not a pentest management tool. Not another dashboard.
An execution platform means:
- Unified operating layer across all exposure categories, cloud, app, network, API, pentest findings, third-party assessments, SBOM data
- Practical AI that reduces manual work instead of creating new interfaces to manage
- Business-aware prioritization that reflects what actually matters to your organization
- Workflow control that matches how your teams operate, not how a product manager imagined they might
- Integrations that keep remediation close to where work happens
- Agent-ready architecture designed for the autonomous security operations future
We help teams move from “we have findings” to “we have closure”, and continuously prove risk reduction over time.
Closing Thoughts
2025 was about unification and operational control.
2026 is about scaling that control with intelligent automation.
The security industry has spent years generating more alerts, more dashboards, more data. The organizations that will succeed are the ones that figure out how to actually act on exposure, continuously, consistently, measurably.
That’s what we’re building.
The CTEM framework gives us the map. Strobes Agents give us the vehicle. What remains is execution, and that’s where we’ve always focused.
If you’re tired of tools that generate reports nobody reads, findings that never reach remediation, and security programs that can’t answer basic questions about risk reduction, let’s talk.
We’re not building another security tool. We’re building the operating system for continuous exposure management.
Thanks for being part of the journey.

 What This Looks Like in Practice
What This Looks Like in Practice