- 30-Day Access: Enjoy four weeks of unrestricted access to our ASM platform.
- Technical Support: Our dedicated support team is available 24/7 to assist you during your trial period.
- No Obligations: Experience the benefits of our ASM solution without any commitment or hidden fees.
Start Free Trial Now
Real-time monitoring of all your known and unknown digital assets
Automated Vulnerability Scanning
Identify misconfigurations and stay one step ahead of threats
Domain Protection
Detect, and eliminate harmful domains to maintain the security of your brand
Account Takeover Protection
Identify potential leaks of vital credentials before they are compromised
Have more than 10k assets?
We work with companies to monitor well over millions of assets, if you’re looking for a custom quote then reach out to us!
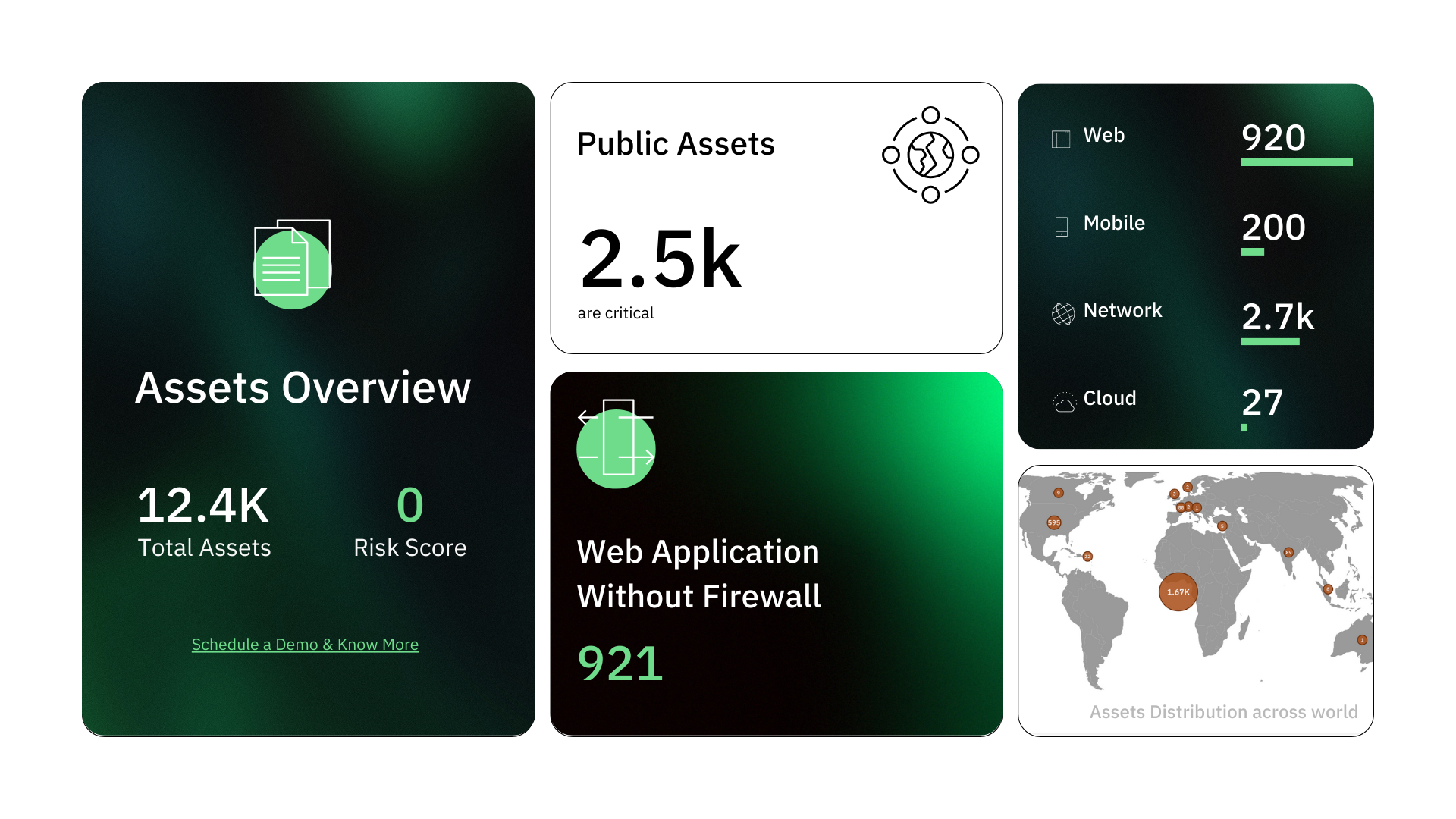
Request Custom QuoteReal-time Asset Discovery & Scanning
- Identify known, unknown, third-party, and malicious assets
- Cover IT resources, devices, applications, websites, and more.
- Address shadow IT, orphaned IT, and subsidiary assets.
- Detect rogue assets crafted by threat actors.
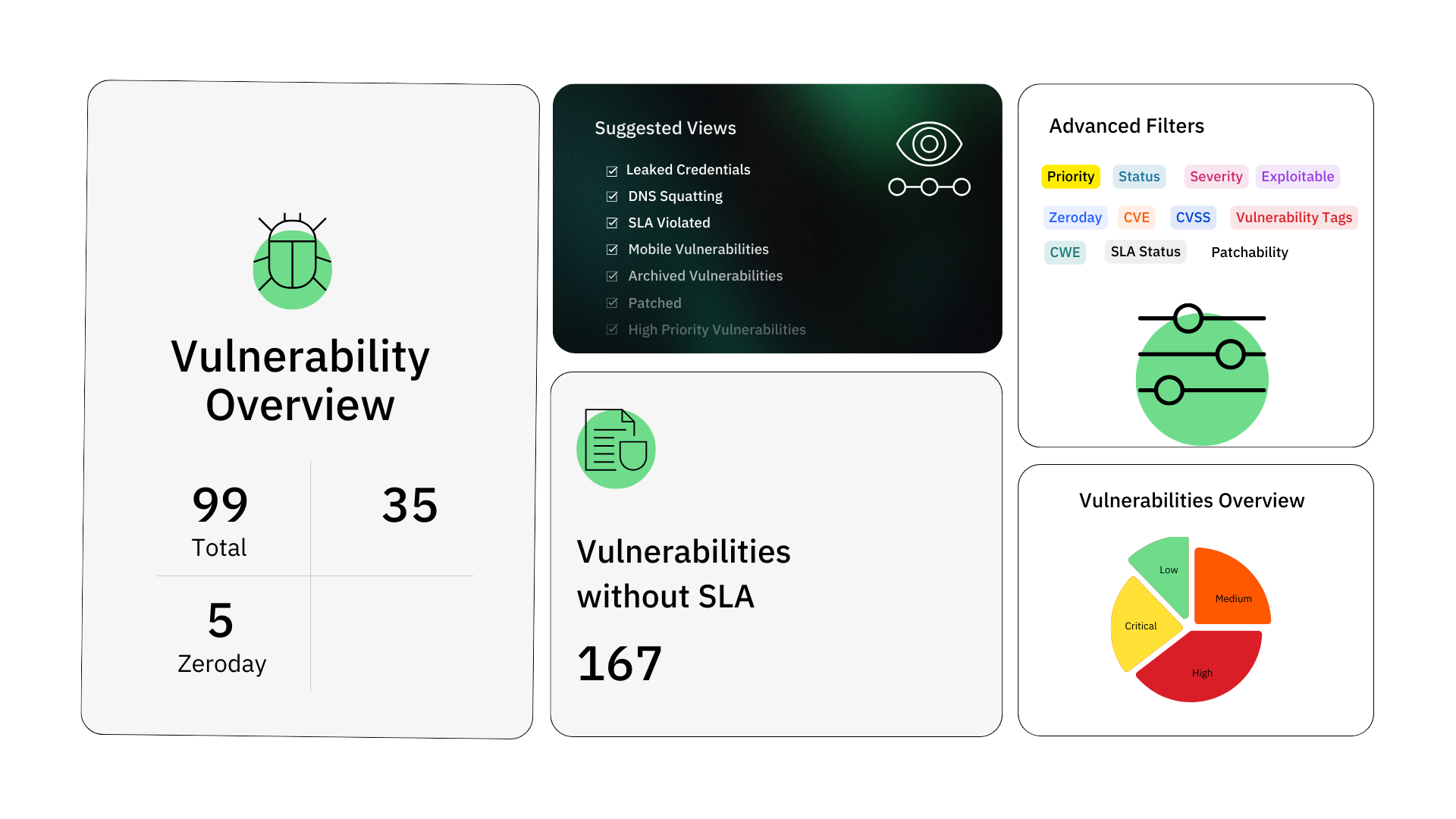
Vulnerability Scanning and Threat Intelligence
- Identify outdated technologies and vulnerabilities.
- Unearth threats like XSS, misconfigurations, and SQL injections.
- Identify exposed services and potential entry points.
- Spotlight default credentials for swift account protection.
- Pinpoint TLS and SSL-related vulnerabilities.
- Stay updated with CVEs and zero-day threats.
Ensure online integrity with vigilant domain protection
- Guard against phishing domains and breaches.
- Detect expired and counterfeit SSL & TLS certificates.
- Identify fake domain names to prevent impersonation.
- Thwart domain takeovers by addressing misconfigurations.
- Safeguard applications from crypto hacking and malware.
- Unveil fraudulent phishing pages, protecting your brand.
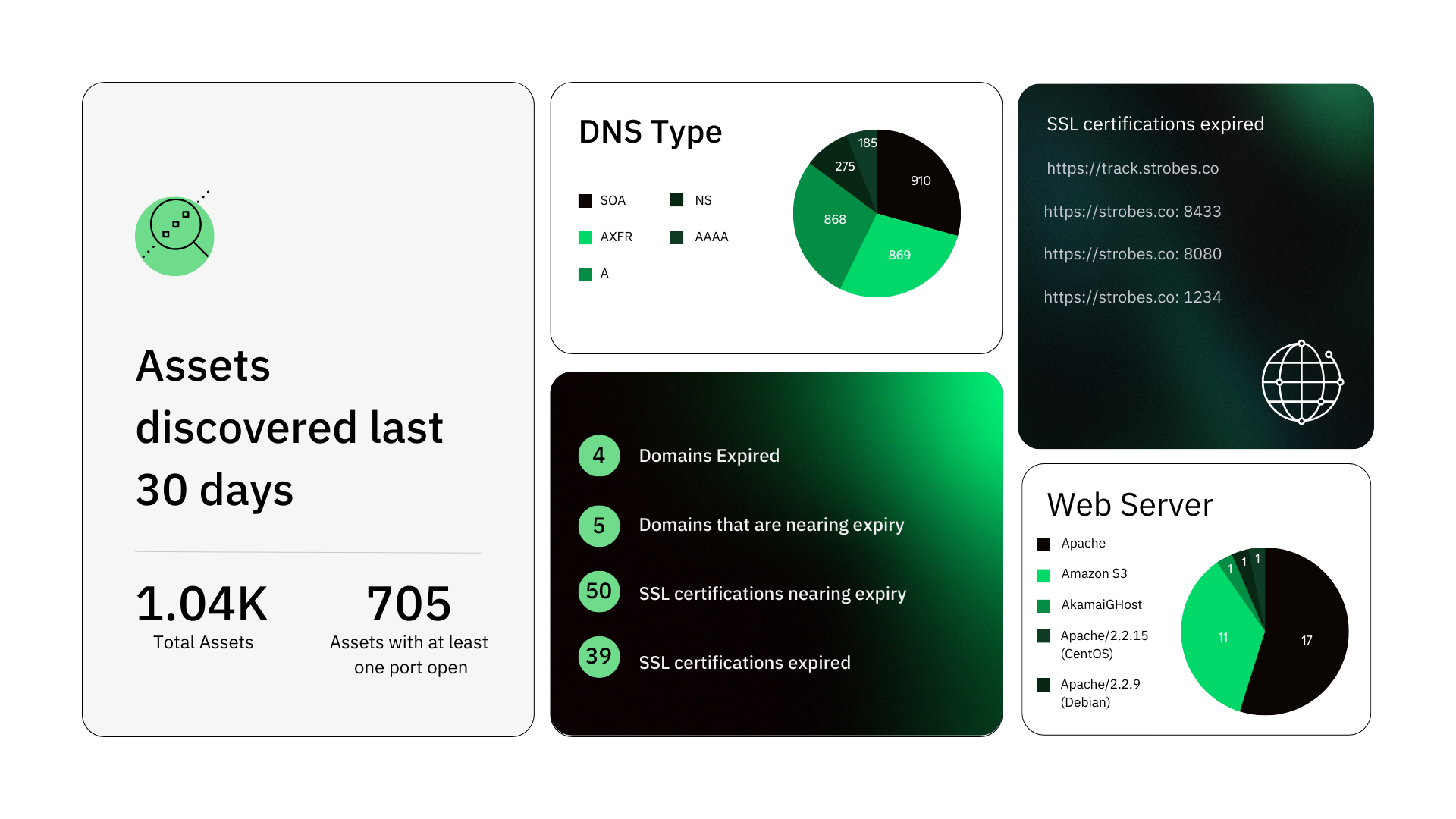
Discover how Strobes efficiently manages attack surfaces, mitigates risks, and enhances your cybersecurity posture. To delve into the specifics, check out the official datasheet.

Enterprises trust us with their attack surface, get to know yours today.
In today’s rapidly evolving digital landscape, your organization’s security posture is only as strong as its weakest link. With the proliferation of devices, applications, and web interfaces, your external attack surface — the sum of all potential entry points that an attacker can exploit — has exponentially expanded. But do you truly know where those vulnerabilities lie?