Some vulnerabilities make headlines. Others quietly become someone’s worst day at work. The critical CVEs 2025 that surfaced in April weren’t just technical flaws, they were real entry points. Into networks. Into data. Into systems that were assumed to be secure.
The Top CVEs of April 2025 include everything from quietly embedded zero-days to flaws in core infrastructure already being exploited in the wild. These aren’t theoretical risks. They’re active threats.
If you’re tracking what truly matters, not just what’s new, this roundup brings you the context behind the CVEs that demand action, not just attention.
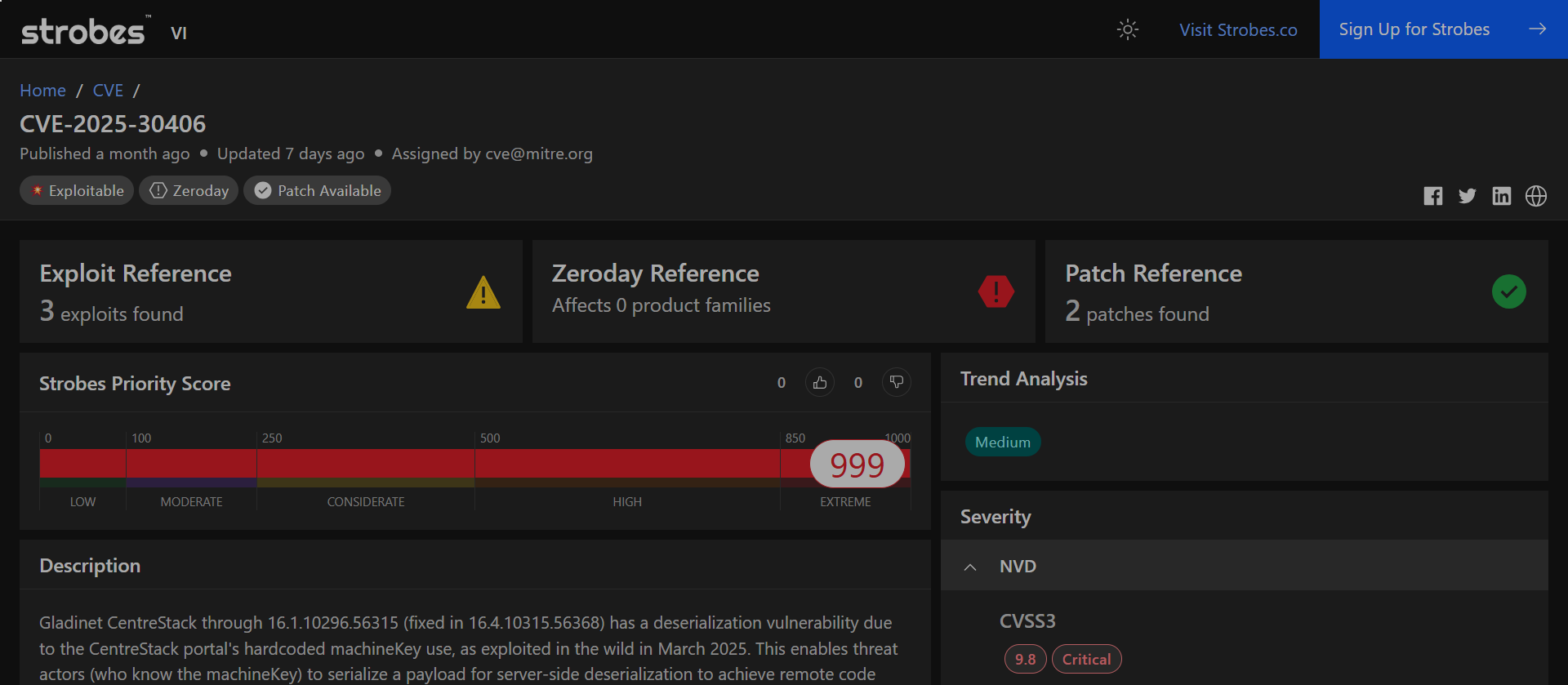
1. CVE-2025-30406: Remote Code Execution via Hardcoded Cryptographic Keys in CentreStack and Triofox
CVE-2025-30406 is a critical remote code execution (RCE) vulnerability discovered in Gladinet’s CentreStack and Triofox, popular enterprise file sharing and collaboration platforms. At its core, the flaw stems from hardcoded machineKey values in the web.config file of these ASP.NET-based applications, which are used to protect ViewState data.
By leveraging these hardcoded keys, attackers can craft malicious ViewState payloads that pass integrity checks, allowing them to trigger server-side deserialization and execute arbitrary code on the target server, completely remotely.
This vulnerability was exploited as a zero-day in the wild, with confirmed incidents involving post-exploitation tools and payloads like MeshCentral, and was added to CISA’s Known Exploited Vulnerabilities (KEV) catalog in April 2025.
At a Glance
Attribute | Value |
| Severity | Critical |
| CVSS v3.1 Score | 9.0 (AV:N/AC:H/PR:N/UI:N/S:C/C:H/I:H/A:H) |
| Exploitation Status | Actively exploited in the wild |
| Attack Vector | Network (Remote) |
| User Interaction | None |
| Privileges Required | None |
| Scope | Changed |
| Vulnerability Type | Use of Hardcoded Cryptographic Key (CWE-321) |
| Affected Products | CentreStack ≤ v16.1.10296.56315 Triofox ≤ v16.4.10317.56372 |
Impact of Exploitation
- Full Remote Code Execution: Attackers gain the ability to run arbitrary code in the context of the IIS worker process.
- Privilege Escalation: RCE as the IIS App Pool identity, with the potential to escalate to NT AUTHORITY\SYSTEM.
- Data Breach Risk: Unauthorized access to sensitive corporate files hosted on the server.
- Persistence & Lateral Movement: Post-exploitation activity includes implanting remote management tools, such as MeshCentral, for ongoing control and lateral movement.
- Supply Chain Targeting: CentreStack and Triofox are commonly used in MSP environments, increasing downstream risk to client networks.
Technical Root Cause
The issue lies in static machineKey values shipped in the default configuration of the product:
<machineKey validationKey=”A123…Z” decryptionKey=”1A23…F” validation=”SHA1″ decryption=”AES” />
These keys are used by ASP.NET to validate ViewState data. If the keys are known or predictable, attackers can generate valid ViewState blobs that pass validation and inject malicious serialized payloads. This results in insecure deserialization, leading to arbitrary code execution on the server.
This vulnerability is similar in nature to the 2020 Telerik UI exploit chain—but with the dangerous twist of known keys shipped by default.
Mitigation Guidance
Apply Patches Immediately:
Gladinet has released patches addressing the flaw in the following versions:
- CentreStack: v16.4.10315.56368
- Triofox: v16.4.10317.56372
Update all instances without delay.
Hardening Recommendations:
- Regenerate machineKey values: If patching is not immediately possible, replace hardcoded keys in web.config with unique values using Microsoft’s machineKey generator.
- Restrict Access: Limit public exposure of CentreStack/Triofox web portals. Use firewalls or reverse proxies to allow access only from trusted IPs or VPNs.
- Monitor for IoCs:
- Unexpected PowerShell or command-line execution
- Deployment of web shells or unknown executables
- MeshCentral traffic or installations
- Segregate Internet-Facing Infrastructure: Place these applications in segmented DMZ environments to contain breaches.
- Implement EDR and Logging: Use endpoint detection tools to alert on anomalous ASP.NET activity or deserialization behaviors.
Why It Ranks Among April 2025’s Top CVEs?
- Confirmed Zero-Day: Actively exploited before the vendor issued a fix.
- High-Impact RCE: Enables full remote control of affected servers without user interaction.
- Weak Default Configs: Exploitation relies on predictable hardcoded keys, easily abused.
- Enterprise & MSP Risk: Products are used in multi-tenant environments, multiplying the blast radius of compromise.
- Post-Exploitation Visibility: Incidents have shown real-world abuse with backdoors and full system compromise.
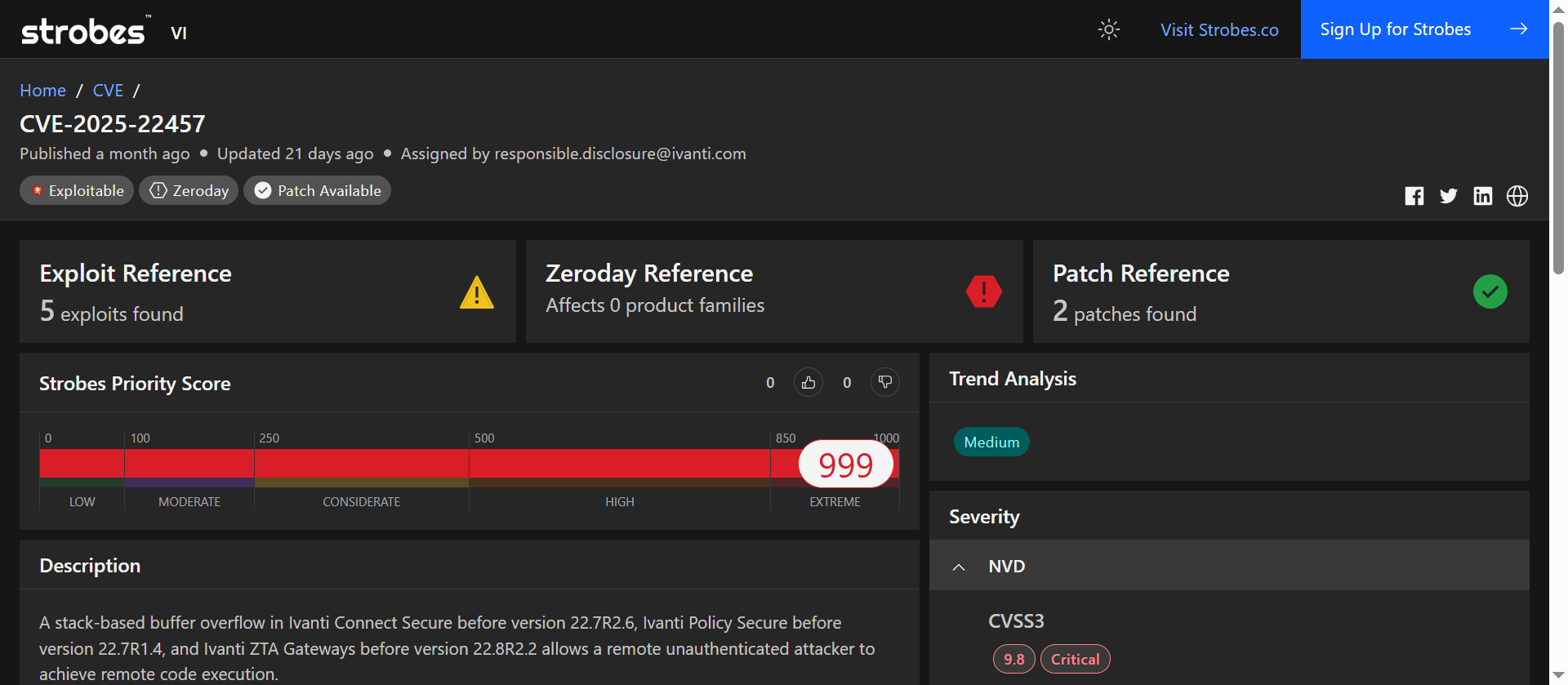
2. CVE-2025-22457: Critical Stack-Based Buffer Overflow in Ivanti Connect Secure, Policy Secure, and ZTA Gateways
CVE-2025-22457 is a critical vulnerability identified in Ivanti’s Connect Secure, Policy Secure, and ZTA Gateway products. This stack-based buffer overflow flaw allows remote, unauthenticated attackers to execute arbitrary code on affected systems, potentially leading to full system compromise. The vulnerability arises from improper input validation, enabling attackers to overwrite memory and hijack control flow.
Disclosed in April 2025, this vulnerability has been actively exploited in the wild, with threat actors deploying sophisticated malware post-exploitation. It has been added to the CISA Known Exploited Vulnerabilities Catalog, underscoring its severity and the urgency for remediation.
At a Glance
Attribute | Value |
| Severity | Critical |
| CVSS v3.1 Score | 9.8 (AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H) |
| Exploitation Status | Actively exploited in the wild |
| Attack Vector | Network (Remote) |
| User Interaction | None |
| Privileges Required | None |
| Scope | Unchanged |
| Vulnerability Type | Stack-Based Buffer Overflow (CWE-121) |
| Affected Products | Ivanti Connect Secure ≤ 22.7R2.5 Ivanti Policy Secure ≤ 22.7R1.3 Ivanti ZTA Gateways ≤ 22.8R2.1 |
Impact of Exploitation
- Remote Code Execution: Unauthenticated attackers can execute arbitrary code on the target system.
- System Compromise: Full control over the affected device, potentially leading to data theft or further network infiltration.
- Deployment of Malware: Observed use of malware families such as TRAILBLAZE and BRUSHFIRE post-exploitation.
- Persistence and Evasion: Attackers have modified integrity checking tools to evade detection and maintain access.
Technical Root Cause
The vulnerability stems from insufficient bounds checking in functions handling input data. Specifically, the application fails to validate the length of user-supplied input before copying it into a fixed-size buffer on the stack. This oversight allows attackers to craft input that overflows the buffer, overwrites adjacent memory, and enables the execution of malicious code.
Mitigation Guidance
Apply Patches Immediately:
Ivanti has released patches addressing this vulnerability:
- Connect Secure: Update to version 22.7R2.6 or later.
- Policy Secure: Update to version 22.7R1.4 or later.
- ZTA Gateways: Update to version 22.8R2.2 or later.
For detailed instructions, refer to Ivanti’s April Security Advisory.
Additional Recommendations:
- Run Integrity Checks: Utilize Ivanti’s Integrity Checker Tool (ICT) to detect signs of compromise.
- Isolate Affected Systems: If compromise is suspected, disconnect the system from the network immediately.
- Conduct Forensic Analysis: Perform a thorough investigation to identify any unauthorized access or modifications.
- Reset Credentials: Change all passwords and revoke any potentially compromised credentials.
- Monitor for Indicators of Compromise (IoCs): Stay vigilant for known IoCs associated with this vulnerability.
Why It Ranks Among April 2025’s Top CVEs?
- Active Exploitation: The vulnerability has been exploited in the wild, with confirmed incidents involving advanced malware deployments.
- High Impact: Successful exploitation grants attackers full control over affected systems, posing significant risks to organizations.
- Widespread Use of Affected Products: Ivanti’s solutions are widely deployed across various sectors, increasing the potential attack surface.
- Sophisticated Threat Actors: Exploitation attributed to advanced persistent threat (APT) groups indicates a high level of threat sophistication.
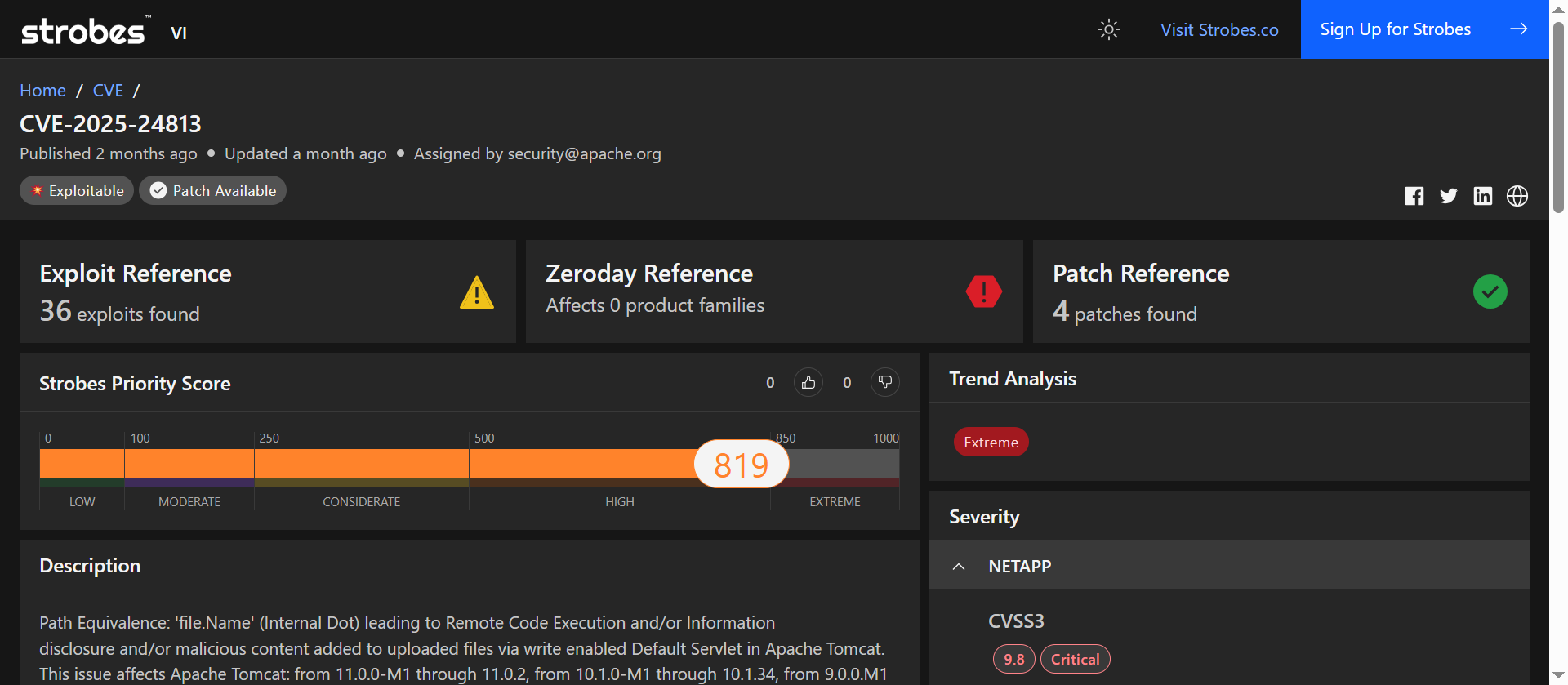
3. CVE-2025-24813: Remote Code Execution via Path Equivalence in Apache Tomcat
CVE-2025-24813 is a critical remote code execution (RCE) vulnerability affecting Apache Tomcat, a widely used open-source Java servlet container. The flaw arises from improper handling of file paths containing internal dots (.), leading to path equivalence issues. Under specific non-default configurations, this vulnerability allows unauthenticated attackers to upload malicious files and execute arbitrary code on the server.
The vulnerability was publicly disclosed on March 10, 2025, and has been observed in active exploitation attempts shortly thereafter. Due to its potential impact and the availability of proof-of-concept (PoC) exploits, it has been added to CISA’s Known Exploited Vulnerabilities (KEV) Catalog.
At a Glance
Attribute | Value |
| Severity | Critical |
| CVSS v3.1 Score | 9.0 (AV:N/AC:H/PR:N/UI:N/S:C/C:H/I:H/A:H) |
| Exploitation Status | Actively exploited in the wild |
| Attack Vector | Network (Remote) |
| User Interaction | None |
| Privileges Required | None |
| Scope | Changed |
| Vulnerability Type | Path Equivalence leading to RCE |
| Affected Products | Apache Tomcat 11.0.0-M1 to 11.0.2<br>Apache Tomcat 10.1.0-M1 to 10.1.34<br>Apache Tomcat 9.0.0.M1 to 9.0.98 |
Impact of Exploitation
- Remote Code Execution: Attackers can execute arbitrary code on the server, potentially leading to full system compromise.
- Information Disclosure: Unauthorized access to sensitive files and data.
- File Manipulation: Injection of malicious content into existing files.
- Persistence: Deployment of backdoors or malware for ongoing access.
Technical Root Cause
The vulnerability stems from Apache Tomcat’s handling of file paths with internal dots (.) during partial PUT requests. When the default servlet is configured to allow write operations (disabled by default) and partial PUT requests are enabled (enabled by default), attackers can exploit path equivalence issues to upload malicious files outside the intended directories.
In scenarios where Tomcat uses file-based session persistence (not enabled by default) and includes a deserialization-vulnerable library, attackers can upload crafted session files containing serialized payloads. Upon deserialization, these payloads can lead to arbitrary code execution.
Mitigation Guidance
Apply Patches Immediately:
Upgrade to the following Apache Tomcat versions that address this vulnerability:
- Apache Tomcat 11.0.3 or later
- Apache Tomcat 10.1.35 or later
- Apache Tomcat 9.0.99 or later
Additional Recommendations:
- Disable Write Permissions: Ensure the default servlet’s write capability is disabled by verifying the readonly parameter is set to true in conf/web.xml.
- Restrict Partial PUT: Disable support for partial PUT requests if not required.
- Monitor for Suspicious Activity: Implement logging and monitoring to detect unusual PUT or GET requests, especially those targeting session files.
- Use Web Application Firewalls (WAFs): Deploy WAFs to detect and block malicious requests exploiting this vulnerability.
- Conduct Regular Security Audits: Review server configurations and access controls to prevent unauthorized file uploads.
Why It Ranks Among April 2025’s Top CVEs?
- Active Exploitation: Observed in the wild shortly after disclosure, indicating real-world attacker interest.
- Unauthenticated Attack Vector: Does not require prior authentication, increasing the risk of widespread exploitation.
- Widespread Impact: Affects multiple versions of Apache Tomcat, a widely used web server.
- Complex Exploitation Requirements: While exploitation requires specific configurations, the severity of potential impact elevates its risk profile.
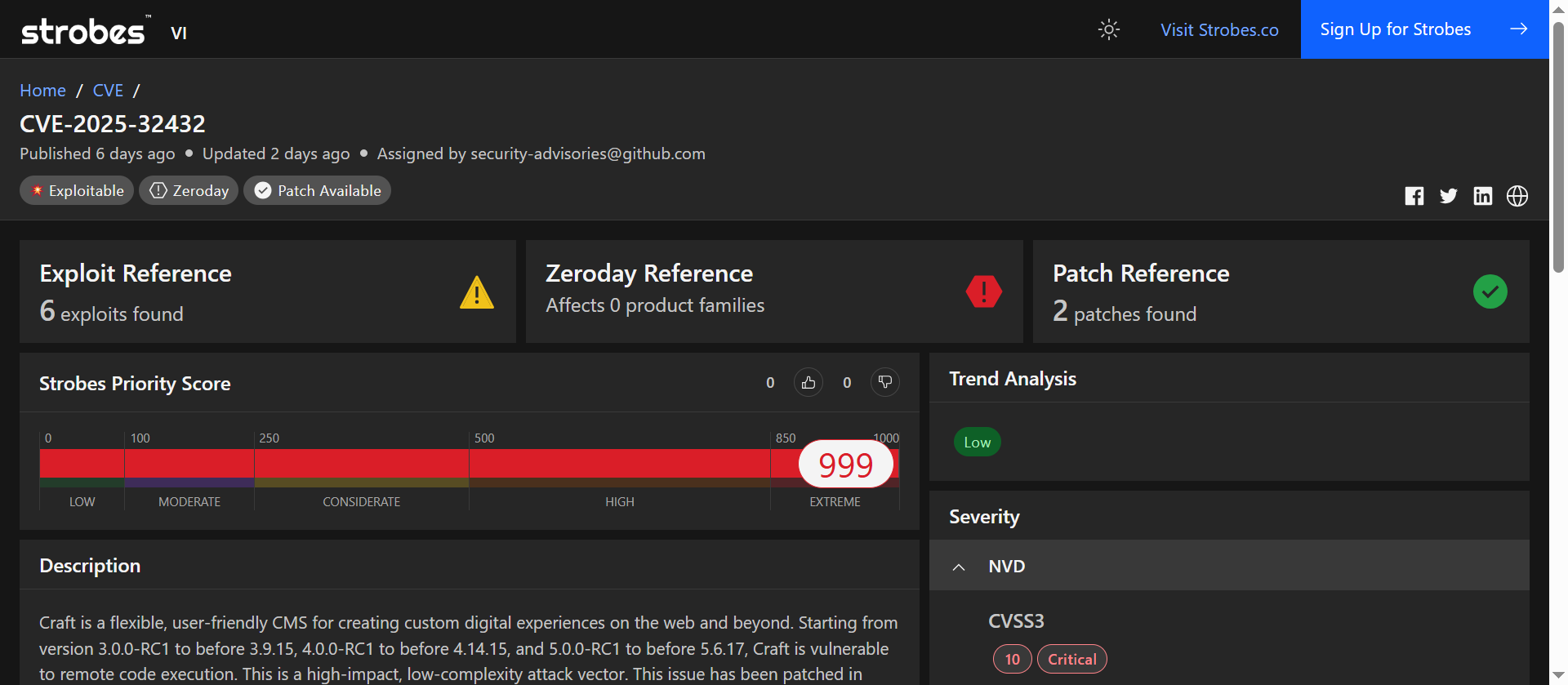
4. CVE-2025-32432: Unauthenticated Remote Code Execution in Craft CMS
CVE-2025-32432 is a critical unauthenticated remote code execution (RCE) vulnerability affecting Craft CMS, a widely-used content management system. The flaw resides in the asset transformation feature, allowing attackers to execute arbitrary code on the server without authentication. This vulnerability has been actively exploited in the wild.
At a Glance
| Attribute | Value |
| Severity | Critical |
| CVSS v3.1 Score | 10.0 (AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H) |
| Exploitation Status | Actively exploited in the wild |
| Attack Vector | Network (Remote) |
| User Interaction | None |
| Privileges Required | None |
| Scope | Changed |
| Vulnerability Type | Code Injection (CWE-94) |
| Affected Products | 3.0.0-RC1 to <3.9.15, 4.0.0-RC1 to <4.14.15, 5.0.0-RC1 to <5.6.17 |
Impact of Exploitation
- Full Remote Code Execution: Attackers can execute arbitrary code on the server, potentially leading to full system compromise.
- Data Breach Risk: Unauthorized access to sensitive data stored on the server.
- Website Defacement: Attackers can modify website content, leading to reputational damage.
- Malware Deployment: Installation of malicious software, including web shells and backdoors.
- Lateral Movement: Attackers can move within the network to compromise additional systems.
Technical Root Cause
The vulnerability stems from improper handling of asset transformation requests in Craft CMS. Specifically, the actions/assets/generate-transform endpoint fails to adequately validate input, allowing attackers to inject malicious payloads. By sending specially crafted POST requests to this endpoint, attackers can trigger deserialization of untrusted data, leading to arbitrary code execution.
In versions 3.x, the asset ID is validated before the transformation object is created, whereas in versions 4.x and 5.x, the validation occurs afterward. This discrepancy allows attackers to exploit the vulnerability by identifying valid asset IDs and injecting malicious payloads.
Mitigation Guidance
Apply Patches Immediately:
Craft CMS has released patches addressing the flaw in the following versions:
- 3.x: Update to version 3.9.15
- 4.x: Update to version 4.14.15
- 5.x: Update to version 5.6.17
Hardening Recommendations:
- Restrict Access: Limit access to the actions/assets/generate-transform endpoint using firewall rules or access controls.
- Monitor Logs: Check server logs for suspicious POST requests to the vulnerable endpoint, especially those containing the string __class in the body.
- Implement Web Application Firewall (WAF): Deploy a WAF to detect and block malicious requests targeting known vulnerabilities.
- Regular Security Audits: Conduct periodic security assessments to identify and remediate potential vulnerabilities.
Why It Ranks Among April 2025’s Top CVEs?
- Zero-Day Exploitation: The vulnerability was actively exploited before patches were available, highlighting its critical nature.
- High Impact: Allows unauthenticated attackers to execute arbitrary code, leading to full system compromise.
- Wide Affected User Base: Craft CMS powers over 150,000 websites, amplifying the potential impact.
- Ease of Exploitation: The attack requires no authentication and minimal technical skill, making it accessible to a broad range of threat actors.
5. CVE-2025-1976: Privilege Escalation via Code Injection in Brocade Fabric OS
CVE-2025-1976 is a critical vulnerability identified in Brocade Fabric OS, a key component in data center networking environments. The flaw arises from improper
IP address validation, allowing a local user with administrative privileges to execute arbitrary code with full root access on affected systems.
This vulnerability was actively exploited in the wild and has been added to the CISA Known Exploited Vulnerabilities (KEV) catalog, underscoring its severity and the urgency for remediation.
At a Glance
Attribute | Value |
| Severity | High |
| CVSS v3.1 Score | 6.7 (AV:L/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H) |
| CVSS v4.0 Score | 8.6(AV:A/AC:L/AT:N/PR:L/UI:N/VC:H/VI:H/VA:H/SC:N/SI:N/SA:N) |
| Exploitation Status | Actively exploited in the wild |
| Attack Vector | Adjacent (Local network access required) |
| User Interaction | None |
| Privileges Required | Low |
| Confidentiality/Integrity/Availability | High |
| Scope | Unchanged |
| Fixed Version | Brocade Fabric OS version 9.1.1d7 |
| Vulnerability Type | Code Injection (CWE-94), OS Command Injection (CWE-78) |
| Affected Products | Brocade Fabric OS versions 9.1.0 through 9.1.1d6 |
Impact of Exploitation
- Full Root Access: Exploiting this vulnerability allows attackers to execute arbitrary code with root privileges, effectively taking full control of the system.
- System Modification: Attackers can modify the Fabric OS, including adding malicious subroutines or altering existing functionalities.
- Network Compromise: Given Fabric OS’s role in managing data center networks, exploitation can lead to broader network compromise, including data interception or disruption of services.
- Persistence: The ability to inject code at the OS level enables attackers to establish persistent backdoors, making detection and removal challenging.
Technical Root Cause
The vulnerability stems from a flaw in the IP address validation process within Brocade Fabric OS. Specifically, the system fails to properly sanitize input, allowing an authenticated user with administrative privileges to inject malicious code. This oversight enables the execution of arbitrary commands with root-level access.
Mitigation Guidance
Apply Patches Immediately:
Upgrade to Brocade Fabric OS version 9.1.1d7, which addresses this vulnerability.
Additional Recommendations:
- Review User Roles: Audit and minimize administrative privileges to reduce potential attack vectors.
- Network Segmentation: Isolate management interfaces and restrict access to trusted networks.
- Monitoring and Logging: Implement robust monitoring to detect unusual activities, such as unexpected command executions or configuration changes.
- Regular Updates: Establish a routine patch management process to ensure timely application of security updates.
Why It Ranks Among April 2025’s Top CVEs?
- Active Exploitation: The vulnerability has been exploited in real-world attacks, emphasizing its practical risk.
- High Impact: Successful exploitation grants attackers full control over critical network infrastructure components.
- Prevalence: Brocade Fabric OS is widely deployed in enterprise environments, increasing the potential impact.
- Delayed Detection: The requirement for administrative access may delay detection, allowing attackers to operate undetected for extended periods.
Final Words
April’s Critical CVEs 2025 weren’t just technical issues, they showed how quickly attackers can find and use real gaps in security. Keeping up isn’t about reacting to every alert. It’s about having the right visibility, knowing which risks matter most, and focusing your efforts where they’ll have the most impact. Approaches like
Continuous Threat Exposure Management (CTEM) help teams move away from scattered patching toward a more practical, prioritized response.It’s not about doing more, it’s about doing what counts.
Want the full picture? Explore Strobes’ Vulnerability Intelligence platform for deeper insights.
Sources & References
1. CVE-2025-30406
2. CVE-2025-22457
3. CVE-2025-24813
4. CVE-2025-32432
5. CVE-2025-1976