“Let’s buy one more tool,” – isn’t it something you have heard before? The CISO tools box is so jam-packed that it’s even tough to remember the work of each tool.
The biggest question for CISO is not how many tools are required but whether the tools offer real-time and actionable security. When every tool speaks its own language, it’s guaranteed to miss risk signals. You may get duplicate alerts, unclear context, and slow responses. And the blame game begins when the breach happens because alignment is missing.
This blog is a reminder that more isn’t always better. Smart CISOs asking – “How can I achieve more in less?”
Strategic tool consolidation doesn’t only mean cost saving. It is also about
- Eliminating noise, not just vulnerabilities
- Bringing the Dev, Sec, and Ops teams on one platform
- Getting real-time view from a single source without switching multiple times
Gartner Reports 75% of Organizations Prioritized Security Vendor Consolidation in 2022.
The Real Problem with CISO Tools Sprawl
You might think having more tools would make things better. It should help, right? But here’s the truth: it doesn’t. It only makes things messier. Most security stacks didn’t start off broken. They just ended up that way. A scanner here. A dashboard there. A reporting tool on top. Before you realize, you’re dealing with chaos.
Let’s look at what actually happens –
- The Big Picture Goes Missing: Each tool might be doing its job. But if they aren’t connected, how will your team know what’s truly at risk? You won’t be able to see the full story. Just scattered pieces.
- Security Teams Get Stuck in Managing Tools: They should be solving real security problems. But they have to manage logins, sync issues, and dashboards instead. They end up wasting time just trying to make things work.
- Alerts Pile Up But Clarity Doesn’t: One tool shows critical. Another says it’s low. Your team can’t be expected to trust every alert at face value. They need to know what’s real and what’s noise, and they rarely can.
- Costs Go Up and Value Goes Down: You might be paying twice for tools that do the same thing. Extra licenses, support fees, training sessions, it all adds up. But does it really give you better protection? Usually not.
In the end, it’s not just about tools. It’s about how they make your team feel. Overwhelmed. Confused. Stuck. And that’s exactly why strategic consolidation isn’t a nice-to-have , it’s a must-do.
The Strategic Value of Continuous Threat Exposure Management
CTEM is a model devised to discover, assess, prioritize, validate, and remediate threat exposures on a continuous basis. It might seem at first glance to be quite similar to traditional vulnerability management. But unlike vulnerability management, which is done at set intervals (or in a rush after a big security event), CTEM is done in much the same way Continuous Integration/Continuous Deployment (CI/CD) practices are done.
It is done in real-time. It is closely integrated with business objectives.
The essential steps of CTEM are:
- Finding out what assets, vulnerabilities, misconfigurations, and exposures exist within internal and external environments.
- Evaluating the effect and exploitability of what was found.
- Contextually ranking exposures based on business impact, threat intelligence, and risk posture.
- Confirming that remediation activities are authentic and that controls are effective.
- Pushing forward the remediation activities and closure.
CTEM is feasible only when tools are consolidated. This is necessary to take away the silos and create the end-to-end visibility one needs in order to see all the way through the phases and into the zones, from one phase to the next.
Rethinking Your Security Stack Capabilities Over Tools
Long-standing security postures have often focused on acquiring the best individual tools for each problem. But when you’re operating in a continuous threat exposure model, that piecemeal approach starts to create more noise than value. Instead of looking at tools in isolation, security leaders now need to focus on overall capability coverage, what’s needed, what’s already there, and where the gaps and overlaps really are.
Here’s how to approach it:
1. Define the Objectives of Business Security Capabilities
Start by identifying your most critical risk areas and aligning them with the core security outcomes you need to support. This might include capabilities like external attack surface management, risk-based vulnerability management, real-time compliance monitoring, and remediation automation. The goal is to shift the thinking from “What CISO tools do we have?” to “What problems must we solve?”
2. Evaluate Existing Tools
Once you’ve defined those capabilities, assess whether your current tools are actually delivering on them. Are they giving your teams full visibility? Are they helping reduce response time? Or are they slowing you down because of limited integration, siloed data, or poor UX? You’ll often find that tools once useful have become blockers simply because the environment around them evolved.
3. Recognize Functional Redundancies
Take a closer look at where features overlap. Alerting, scanning, ticketing, asset management, many tools offer these functions, but having five platforms doing variations of the same thing just adds confusion. This is where consolidation creates real value, streamlining operations, removing duplication, and making it easier for teams to act on the right data, faster.
4. Focus on Information Movement and Fit
A great platform doesn’t just deliver features, it fits seamlessly into your workflow and connects security data across environments. Look for solutions that reduce friction, not add to it. CISO Tools that help move risk intelligence effortlessly between teams, systems, and decision points will always bring more value than niche tools that live in their own corner and require yet another dashboard.
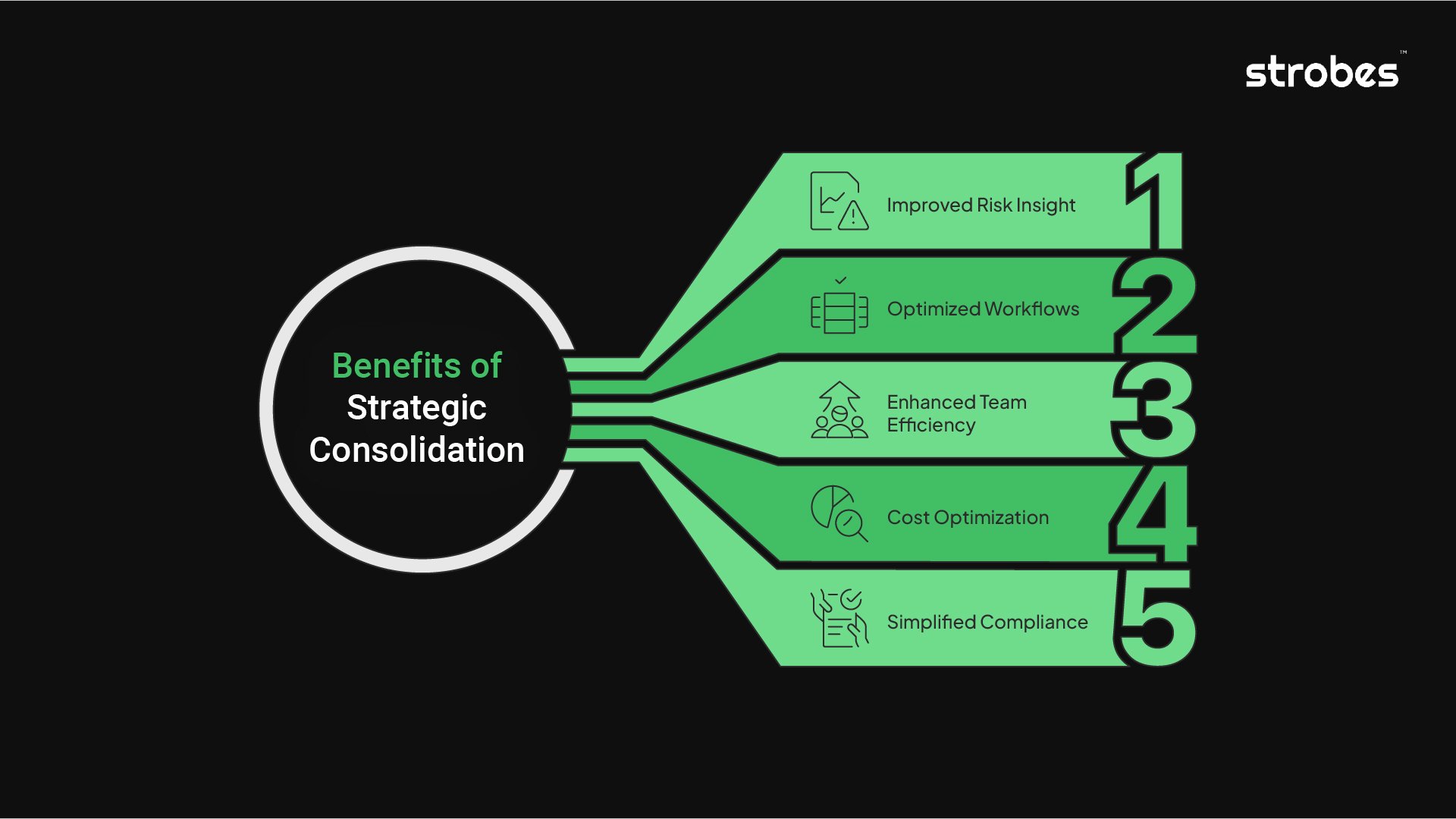
Benefits of Strategic Tool Consolidation
Tool consolidation isn’t just about cutting down your tech stack, it’s about building a stronger, more efficient, and more focused security program. When done right, consolidation brings visibility, speed, and simplicity to areas that were once fragmented and frustrating.
Here’s what it can unlock:
1. Improved Risk Insight
When all your risk data flows into a single platform, everything becomes easier to understand. You get a complete view of vulnerabilities, misconfigurations, and asset exposure, across your internal and external environments. Unified risk scoring and contextual insights allow decision-makers to act faster and more confidently, because they’re no longer relying on scattered reports or half-formed pictures.
2. Optimized Workflows
Integrated platforms reduce the back-and-forth. From detection to triage to remediation, workflows become smoother and more automated. No more manually stitching together results from five different tools, the entire process can run end-to-end, with built-in triggers, playbooks, and accountability at every step. Less friction means faster action.
3. Enhanced Team Efficiency
Security teams shouldn’t be spending hours figuring out how tools talk to each other, they should be focused on reducing risk. With fewer interfaces to manage, onboarding becomes easier, cross-team collaboration improves, and analysts can spend more time investigating and responding instead of copy-pasting data. Smart platforms also help teams make smarter decisions, by surfacing what matters and hiding the noise.
4. Cost Optimization
Reducing tool count naturally brings down costs, not just in licensing, but in support contracts, maintenance overhead, and integration work. With fewer vendors to manage, procurement becomes cleaner, negotiations become stronger, and your ROI becomes easier to prove. And perhaps most importantly, your security budget can be reallocated toward actual outcomes, not tool sprawl.
5. Simplified Compliance and Reporting
Consolidation also pays off during audits and reporting cycles. When all your evidence lives in one system, generating reports becomes faster and far more accurate. Real-time dashboards replace spreadsheet chaos. Gaps are easier to identify. And teams are less likely to make errors under pressure, simply because they’re not chasing data across multiple systems.
A CTEM-Aligned Playbook for CISOs
To implement tool consolidation successfully under a CTEM model, CISOs should follow a structured approach:
| Steps | Actions |
|---|---|
| Define Risk Goals | Align security investments with business-critical risks and compliance obligations. |
| Conduct Capability Mapping | Identify essential CTEM capabilities and map current tools against them. |
| Eliminate Redundancy | Identify overlapping functionalities and retire tools that add little unique value. |
| Choose a CTEM-Centric Platform | Select platforms that integrate multiple CTEM functions natively (e.g., VM, ASM, remediation). |
| Automate Key Workflows | Leverage AI and automation to reduce manual triage, alerting, and compliance tasks. |
| Align Teams | Ensure that Dev, Ops, and Sec teams are trained on unified workflows and shared objectives. |
How Strobes Make Security Operations Simpler and Smarter?
At Strobes, we didn’t set out to build another security tool. We set out to solve the very problem so many teams are struggling with, too many disconnected tools, too many dashboards, and too little clarity.
Our platform is built from the ground up with CTEM and consolidation in mind. Instead of forcing you to manage risk across five different systems, Strobes brings everything into one unified space, where discovery, prioritization, remediation, and reporting all work together. Here’s how it helps security teams cut through the clutter and take control:
Unified Attack Surface Management (ASM)
You can’t fix what you don’t see. Strobes continuously discovers assets across cloud, on-prem, and hybrid environments, including domains, IPs, shadow IT, and third-party connections. Everything is automatically mapped and monitored, so nothing stays hidden for long.
Advanced Vulnerability Management (RBVM)
We integrate with your existing scanners or use our built-in ones. Vulnerabilities are automatically deduplicated, enriched with threat intel, and prioritized based on risk and exploitability. No more spreadsheet juggling, just clear, actionable insights on what matters most.
Automated Remediation Workflows
Fixing issues shouldn’t mean more manual work. Strobes lets you assign, track, and validate remediation tasks directly within the platform. With integrations to Jira, ServiceNow, and Slack, your teams stay informed and accountable, without switching context.
Compliance and Reporting
Customizable dashboards and real-time reports mean you’re always audit-ready. Whether it’s internal stakeholders, regulators, or customers, you can generate clean, accurate reports with just a few clicks, no last-minute scrambling.
AI-Powered Automation
Our AI agents take on the tedious tasks, from triaging findings and mapping them to compliance controls, to triggering automated patching workflows. That gives your analysts time back, and gives your program the speed it needs.
By consolidating these capabilities, Strobes replaces complexity with clarity. Security teams move faster, leadership gets better visibility, and risk gets resolved, not just tracked.
Tool consolidation sounds like a no-brainer, less chaos, better visibility, faster response. But the reality? It can hit resistance. People get attached to their tools. Teams worry about disruption. Budgets get tight. And change feels risky. These challenges are real, but they can be worked through, with the right approach and the right narrative behind it.
Here are the most common roadblocks, and how security leaders are handling them:
1. Cultural Resistance and Tool Attachment
It’s natural for teams to hold onto what they know. A tool that’s been around for years becomes familiar, even if it’s no longer effective. What helps here is context.
Show your teams how consolidation frees up their time, reduces alert fatigue, and makes their work more impactful. Position it as a step forward, not a replacement of their efforts. People don’t resist change, they resist confusion. So be clear about the “why.”
2. Specialized Tool Requirements in Certain Areas
Some industries or compliance frameworks still require niche tools, and that’s okay. Consolidation doesn’t have to mean giving up everything. Think of it as centralizing what can be centralized. Specialized tools can still feed into a core platform, so they don’t operate in isolation. Integration, not elimination, is the goal here.
3. Integration and Workflow Disruption
Some tools are deeply embedded into daily workflows. Pulling them out can feel risky. That’s why it’s smart to start small, replace low-risk, high-overhead tools first. Show quick wins. Phase out gradually, not all at once. And always keep teams looped in so adoption feels like a shared journey, not a forced migration.
4. Budget Constraints and Timing
Consolidation might require upfront investment, especially when replacing tools under existing contracts. But that investment quickly pays off, in fewer renewals, less maintenance, and reduced operational drag. Frame the ROI in terms of time saved, risk reduced, and visibility gained. Most importantly, tie it to business impact. That’s what unlocks buy-in.
Final Thoughts
Today’s CISOs are at the helm of a vast, expanding, and diversifying digital universe. What’s in it? More and more businesses are busy establishing a vast array of digital pathways to the outside world, all of which offer new and inviting opportunities for cybercriminals.
To protect all that growing cyber territory and ensure digital trust, the CISO within each of those businesses has the job of closing all the digital doors that ought not to be open and overseeing an effective digital security program. As this responsibility grows, CISO Tools Consolidation becomes a strategic necessity streamlining overlapping solutions to reduce complexity and improve operational efficiency.
The CTEM provides a strategic lens that sees tool consolidation not just as an IT project, but as a function that enables business. When organizations adopt platforms that support several CTEM phases, they can:
- Decrease the number of unnecessary tools.
- Risk insights are centralized.
- Make operational agility better
- Speed up the processes of fixing problems.
Strobes Security believes the future of cybersecurity is in consolidation without compromise. We unify capabilities under a single pane of glass, empowering CISOs with clarity, speed, and control. Book a demo to see how streamlined security can look for your organization.
Related Reads:
- Why Ignoring Vulnerability Prioritization is a CISO’s Worst Nightmare?
- Continuous Threat Exposure Management (CTEM) – The Ultimate Guide for CISOs
- The Unfair Blame Game: Why CISOs Shouldn’t Shoulder All the Responsibility
- 6 Key Attributes of an Effective CISO
- CISO’s Solution for Better Vulnerability Management