December 2025 was a brutal reality check for security teams. While most were winding down for the holidays, threat actors weaponized a tectonic shift in the landscape, headlined by the “React2Shell” exploit. From mass web server takeovers to unauthenticated mail server compromises, the Top CVEs of December 2025 demand immediate action. Here is the breakdown of the month’s five most dangerous exploits and how to patch them.
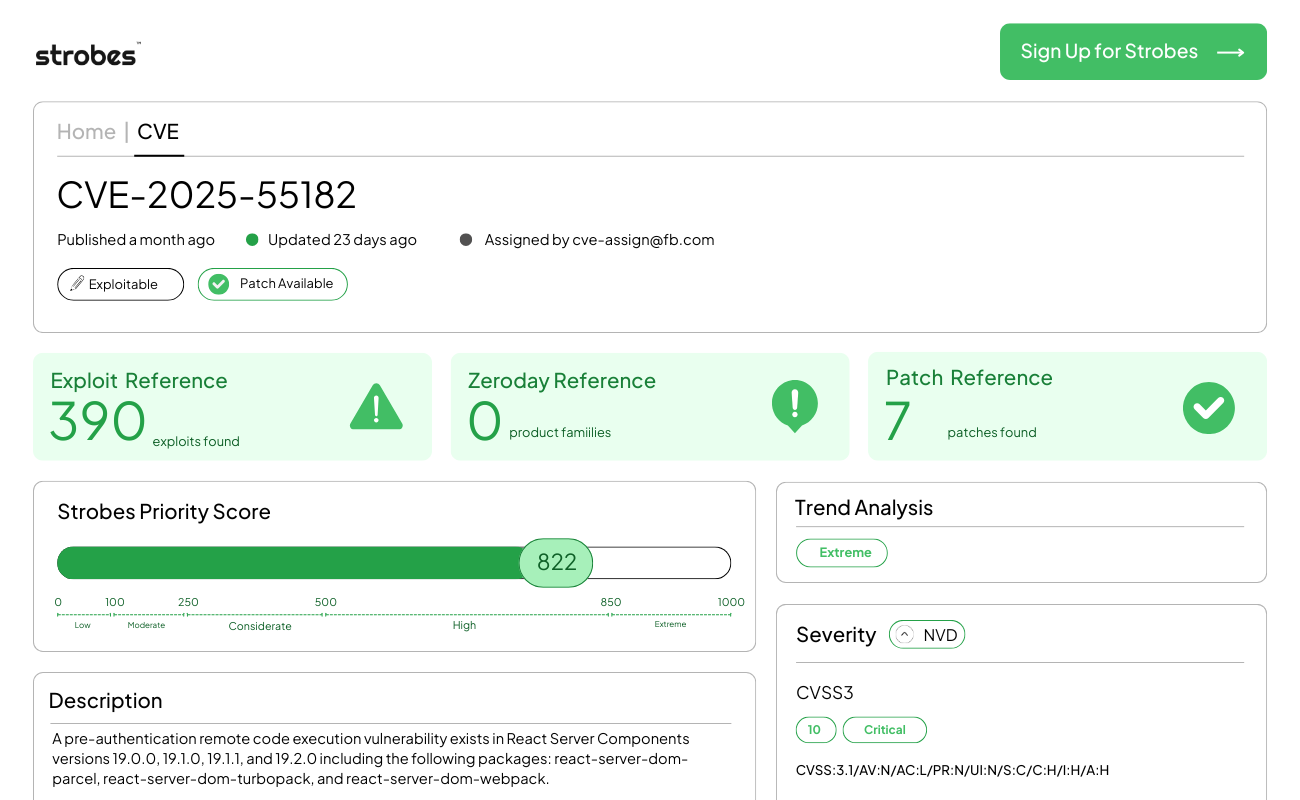
1. CVE-2025-55182 | React2Shell: Unauthenticated Remote Code Execution
CVE-2025-55182, colloquially known as “React2Shell,” is a maximum-severity vulnerability in the React framework (specifically affecting React 19 and Next.js versions utilizing React Server Components). It allows unauthenticated remote attackers to execute arbitrary code on the underlying server by sending a specially crafted HTTP request. By exploiting a flaw in how the server handles serialized data during the “Flight” protocol handshake, attackers can achieve full system compromise. Security researchers have labeled this the “Log4Shell of the Frontend” due to the ubiquity of React in modern web infrastructure.
Vulnerability Breakdown
CVE-2025-55182 originates from a fundamental logic error in the React Server Components (RSC) rendering engine. To optimize performance, React uses a serialized format called the “Flight” protocol to pass state and components between the server and the client.
The vulnerability exists because the server-side logic responsible for reconstructing these objects fails to validate the type of functions being “revived” during deserialization. An attacker can craft a malicious JSON-like payload that mimics a legitimate component state but includes a reference to a restricted server-side module (such as child_process). When the React engine processes this payload to update the view, it inadvertently executes the attacker’s embedded command. Because this occurs before any custom application-level authentication middleware is typically triggered, the exploit is fully unauthenticated.
Impact of Exploitation
If an attacker successfully exploits React2Shell, the consequences are catastrophic:
- Full Server Takeover: The attacker gains the ability to execute shell commands with the same privileges as the web server process (e.g., www-data or node).
- Secrets Exfiltration: Access to the server environment allows for the theft of .env files, database credentials, API keys, and cloud provider metadata tokens.
- Supply Chain Injection: Attackers can modify the application source code or inject malicious scripts directly into the frontend delivered to all visiting users.
- Lateral Movement: From the compromised web server, attackers often pivot into the internal VPC, targeting databases and internal microservices
Mitigation & Patching
| Mitigation Step | Status / Action |
| Patch Availability | Immediate. Update to React 19.0.1+ or Next.js 15.1.0+ (or the backported 14.x security releases). |
| Exploit Activity | Extremely High. Proof-of-Concept (PoC) code is public, and mass-scanning for vulnerable / and /_next/data endpoints is ongoing. |
| Immediate Workaround | If patching is impossible, use a Web Application Firewall (WAF) to inspect and block requests containing serialized RSC headers (e.g., RSC: 1) with suspicious payloads. |
| Hardening Tip | Ensure your Node.js process is running with the least privilege possible and utilize a hardened container image with a read-only filesystem. |
| Detection | Monitor server logs for unusual POST or GET requests to RSC-enabled routes that contain high-density encoded characters or references to system-level modules. |
| Hunt Suggestions | Search for unexpected outbound network connections from your web tier, particularly to known C2 (Command & Control) IPs or common cryptomining pools. |
Why is this CVE in Our Top Picks of the Month?
CVE-2025-55182 is our top pick because it targets the very foundation of the modern web. React is the most popular frontend library in the world, and the shift toward Server Components means that vulnerabilities that were once “client-side only” have now moved to the server. The “zero-click” and unauthenticated nature of this exploit makes it a dream for threat actors. Its inclusion in the December 2025 threat landscape signals a paradigm shift in how we must secure JavaScript-based infrastructure.
Strobes Recommendation
- Identify: Use an SCA (Software Composition Analysis) tool to identify every instance of React 19 and Next.js in your environment.
- Patch: This is a “Tier 0” priority. Deploy the patched versions of your framework immediately.
- Rotate: Treat all environment variables on vulnerable servers as compromised. Rotate all database passwords and API keys immediately after patching.
- Verify: Conduct a post-incident scan to ensure no web shells or “Shadow” admin accounts were left behind by automated exploit scripts.
Bottomline
A critical, unauthenticated RCE in the world’s most popular web framework. This is not a drill. If you use React Server Components, you must patch today. Failure to do so leaves your entire server environment open to automated takeover and data exfiltration.
2. CVE-2025-66516 | Apache Tika Unauthenticated XXE and SSRF Vulnerability
CVE-2025-66516 is a critical vulnerability in Apache Tika (specifically affecting core and PDF parsing components) that allows unauthenticated remote attackers to trigger a Server-Side Request Forgery (SSRF) or XML External Entity (XXE) injection. By submitting a specially crafted document for parsing, an attacker can force the server to disclose local system files or interact with internal network resources that are otherwise shielded from the public internet. Given Apache Tika’s role as the “gold standard” for content detection and extraction in enterprise search engines, document management systems, and mail gateways, the vulnerability poses a massive “hidden” risk to the global software supply chain.

Vulnerability Breakdown
CVE-2025-66516 stems from the default configuration of the XML parsers used within Apache Tika’s PDF and metadata extraction modules. When the system processes a document containing malicious XML content, it fails to disable the resolution of external entities.
An attacker can embed an external entity reference within a document (such as a PDF or an XML-based Office file). When Tika attempts to “extract” the text or metadata, the underlying parser follows the external reference. This can lead to the server reading local files (e.g., /etc/passwd or configuration files containing cloud metadata secrets) and sending the contents back to the attacker. Furthermore, because Tika often sits deep within a “trusted” zone of a corporate network, it can be used as a pivot point to scan internal ports or attack internal APIs that do not require authentication from internal IPs.
Impact of Exploitation
If an attacker succeeds, likely outcomes include:
- Sensitive Data Exfiltration: Attackers can read sensitive files from the host server, including credentials, SSH keys, and environmental variables.
- Internal Network Reconnaissance: The Tika server can be forced to map the internal network, identifying internal databases and administration panels.
- Cloud Credential Theft: In cloud environments (AWS/Azure/GCP), attackers can query the Instance Metadata Service (IMDS) to steal temporary security tokens, leading to full cloud environment takeover.
- Service Disruption: Maliciously crafted “billion laughs” XML payloads can cause a Denial of Service (DoS) by exhausting the server’s CPU and memory resources.
Mitigation & Patching
| Mitigation Step | Status / Action |
| Patch Availability | Upgrade to Apache Tika 3.0.1 or higher immediately. This version disables external entity resolution by default across all parsing modules. |
| Exploit Activity | High. Security researchers have published PoCs (Proof of Concept), and automated scanners are actively testing document upload portals for this vulnerability. |
| Immediate Workaround | If patching is delayed, configure your Web Application Firewall (WAF) to inspect file uploads for XML signatures (<!ENTITY) and block suspicious document types. |
| Hardening Tip | Run Tika in a highly restricted container with no outbound internet access and limited access to the local filesystem (Read-Only). |
| Detection | Monitor system logs for unexpected outbound network connections from the Tika service, especially to internal IP ranges or cloud metadata IP (169.254.169.254). |
| Hunt Suggestions | Search for unusual file access patterns originating from the Tika process. Audit your document processing pipeline for any “failed” parsing jobs that coincide with high CPU spikes. |
Why is this CVE in Our Top Picks of the Month?
CVE-2025-66516 is a “silent killer” because Apache Tika is rarely a standalone product; it is a library embedded in thousands of other applications. Organizations may not even realize they are running Tika until it is exploited. Its CVSS 10.0 rating and the ease of exploitation—simply uploading a file to a resume portal, a cloud storage bucket, or a CRM—make it a primary target for ransomware groups looking for an initial foothold in the enterprise.
Strobes Recommendation
- Inventory: Use an SBOM (Software Bill of Materials) tool to identify every application in your environment that utilizes the Apache Tika library.
- Patch: Prioritize patching of Tika-server instances and applications that accept public document uploads.
- Network Segregation: Ensure document-parsing workers are isolated in a DMZ or a “sandbox” VPC with zero egress to the internal network.
- Rotate Secrets: If you suspect an SSRF attack has occurred, immediately rotate all cloud IAM roles and service account tokens associated with the affected server.
Bottomline
A critical, easily triggered XXE/SSRF vulnerability in a ubiquitous document-parsing library. Because Tika is often a sub-component of larger systems, this is a high-priority supply chain event. Failure to patch or isolate the parser could lead to a total leak of server secrets and a breach of the internal network.
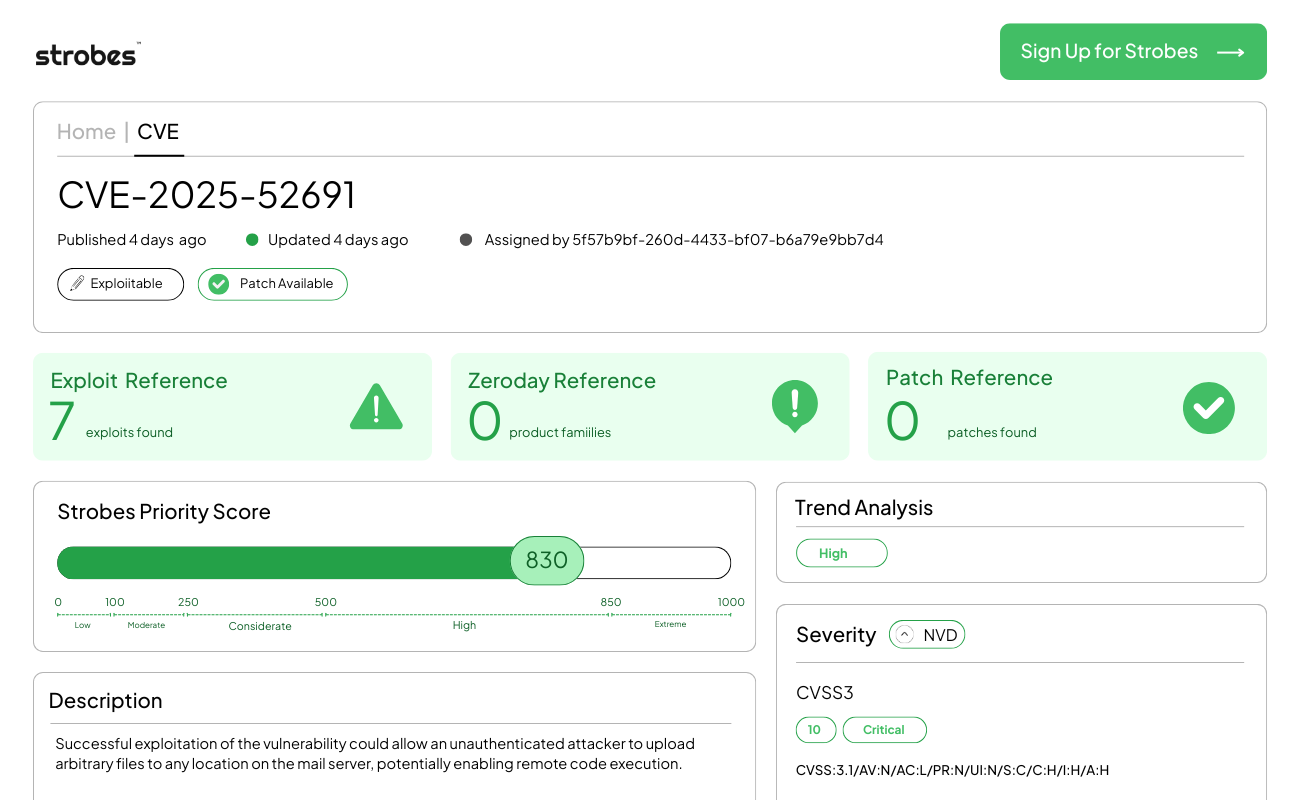
3. CVE-2025-52691 | SmarterTools SmarterMail Unauthenticated Arbitrary File Upload
CVE-2025-52691 is a critical vulnerability in SmarterTools SmarterMail (affecting Build 9406 and earlier) that allows unauthenticated remote attackers to bypass security controls and achieve Remote Code Execution (RCE). By exploiting an insecure file upload mechanism, attackers can plant malicious web shells on the server, effectively seizing control of the organization’s email infrastructure. SmarterTools released an emergency update in late December 2025 following reports from the Cyber Security Agency of Singapore (CSA) regarding the flaw’s potential for mass exploitation.
Vulnerability Breakdown
CVE-2025-52691 stems from a failure in the application’s attachment handling and temporary file management logic. The SmarterMail web interface allows users to upload files for various purposes (attachments, profile images, etc.); however, the server fails to properly sanitize the destination path or validate the file extension during specific unauthenticated API calls.
An attacker can craft a multi-part POST request that leverages directory traversal sequences (e.g., ../../) to escape the intended “temp” directory. By doing so, they can write an executable file—such as an .aspx web shell—directly into the web root or a startup folder. Since the vulnerability exists in a pre-authentication routine, the attacker does not need a valid mailbox or login credentials to execute this “write-what-where” primitive.
Impact of Exploitation
If an attacker succeeds, likely outcomes include:
- Complete Server Takeover: The attacker gains the same privileges as the SmarterMail service (often SYSTEM or Network Service), allowing for full control of the host OS.
- Email Exfiltration: Unauthorized access to all stored emails, attachments, and contact lists across all domains hosted on the server.
- Business Email Compromise (BEC): Attackers can send legitimate-looking emails from internal accounts to facilitate wire fraud or distribute malware to partners.
- Ransomware Gateway: Historically, vulnerabilities in mail servers are used as the initial entry point to deploy file-encrypting ransomware across the broader corporate network.
Mitigation & Patching
| Mitigation Step | Status / Action |
| Patch Availability | Apply SmarterMail Build 9413 or later. Build 9483 (Dec 18, 2025) is recommended for the most stable and secure experience. |
| Exploit Activity | Critical Monitor. While initially reported via responsible disclosure, the ease of exploitation has led to widespread scanning by IABs (Initial Access Brokers). |
| Immediate Workaround | Restrict access to the SmarterMail Web UI via IP whitelisting or VPN. Disable “Anonymous” file upload features in the admin settings if possible. |
| Hardening Tip | Ensure the SmarterMail service is running with the least privileges necessary. Use a dedicated service account rather than NT AUTHORITY\SYSTEM. |
| Detection | Scan the \SmarterMail\Service\ and \SmarterMail\MRS\ directories for unexpected .aspx, .ashx, or .php files created recently. |
| Hunt Suggestions | Search IIS logs for POST requests to upload endpoints that return a 200 OK, followed by immediate GET requests to new files in unconventional directories. |
Why is this CVE in Our Top Picks of the Month?
CVE-2025-52691 is a standout risk because it targets the primary communication hub of an enterprise. Unlike many vulnerabilities that require a foothold inside the network, this is a “front-door” exploit. The combination of a 10.0 CVSS score and the fact that mail servers must be internet-facing makes it a perfect target. Its disclosure just before the holiday season follows the pattern of “Log4Shell” and “ProxyLogon,” where attackers capitalize on reduced IT staffing during the break.
Strobes Recommendation
- Emergency Update: Update SmarterMail to Build 9413 or higher immediately. This should be treated as an out-of-band security emergency.
- Integrity Check: Perform a file integrity check of your web directories. Look specifically for files created in the last 30 days that do not match the standard installation manifest.
- Review API Logs: Inspect logs for unusual activity involving the System Admin or File Upload API endpoints from unknown external IPs.
- Monitor SMTP Traffic: Watch for sudden spikes in outbound mail volume, which could indicate the server is being used as a spam relay or for internal phishing.
Bottomline
This is an unauthenticated RCE on a critical infrastructure component. If you run SmarterMail and have not updated since mid-December 2025, you should assume a high probability of compromise and initiate a forensic review alongside your patching efforts.
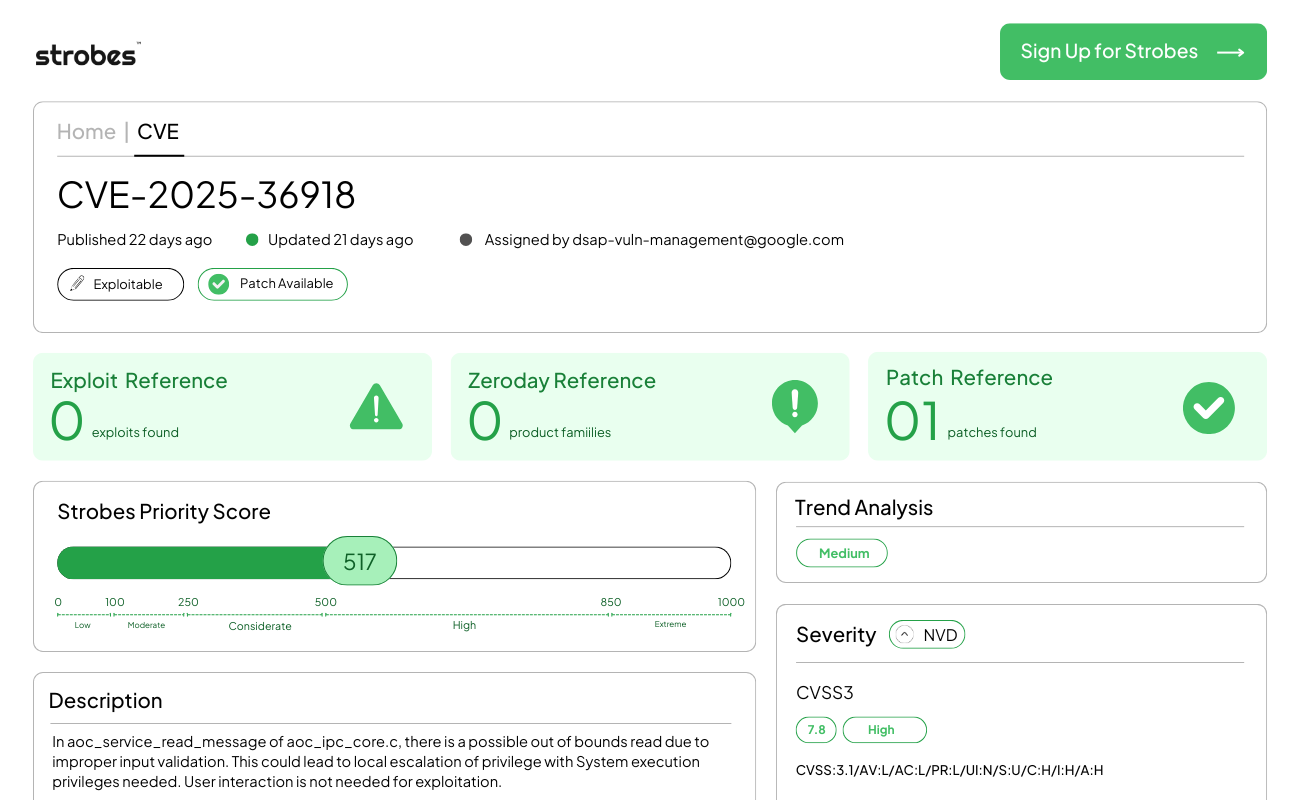
4. CVE-2025-36918 | Windows MSHTML Platform Remote Code Execution Vulnerability
CVE-2025-36918 is a critical remote code execution (RCE) vulnerability in the Windows MSHTML engine, a core component used by various applications, including Microsoft Office and Outlook, to render web-based content. This flaw allows unauthenticated attackers to execute arbitrary code on a target system by tricking a user into opening a specially crafted file or visiting a malicious website. Microsoft issued an emergency security update in December 2025 following reports of this vulnerability being utilized in high-precision spear-phishing campaigns against government and financial institutions.
Vulnerability Breakdown
CVE-2025-36918 is rooted in a “Use-After-Free” (UAF) condition within the MSHTML (Trident) engine’s processing of CSS property inheritance. When the engine parses a maliciously crafted HTML document containing nested style elements, it fails to properly manage memory pointers during the rendering phase.
An attacker can exploit this by hosting a malicious website or sending an email containing an embedded HTML object. When the victim’s system attempts to render the content, the MSHTML engine accesses a memory location that has already been deallocated. This memory corruption allows the attacker to hijack the execution flow of the host application (like Outlook.exe or Explorer.exe) and execute a payload in the context of the current user. Because MSHTML is integrated deeply into the Windows shell, this exploit bypasses many traditional browser-based sandboxes.
Impact of Exploitation
If an attacker succeeds, likely outcomes include:
- Full System Compromise: Attackers gain the ability to install programs, view or change data, and create new accounts with full user rights.
- Stealthy Lateral Movement: Since the exploit often runs within trusted processes like Outlook, it can be used to harvest local credentials and move through the network undetected.
- Ransomware Deployment: The vulnerability serves as an ideal “dropper” for secondary payloads, including infostealers and ransomware encryptors.
- Data Exfiltration: Immediate access to the victim’s documents, emails, and saved browser passwords without requiring administrative escalation.
Mitigation & Patching
| Mitigation Step | Status / Action |
| Patch Availability | Apply the Windows December 2025 Cumulative Update immediately. This addresses the memory handling logic in mshtml.dll. |
| Exploit Activity | Very High. Active exploitation has been confirmed by multiple threat intelligence feeds, primarily via malicious .docx and .rtf attachments. |
| Immediate Workaround | Disable the rendering of HTML emails in Outlook (View as Plain Text) and restrict the opening of Office documents from untrusted external sources. |
| Hardening Tip | Use Windows Defender Application Guard or similar containerization tools to isolate office applications from the rest of the operating system. |
| Detection | Monitor for unusual child processes spawned by Outlook.exe or Winword.exe (e.g., cmd.exe, powershell.exe, or certutil.exe). |
| Hunt Suggestions | Search telemetry for crashes in mshtml.dll or edgehtml.dll, followed by unexpected network connections to unknown IP addresses. |
Why is this CVE in Our Top Picks of the Month?
CVE-2025-36918 represents a massive “attack surface” risk because the MSHTML engine remains a legacy dependency for many enterprise applications, even those not using Internet Explorer. The ability to trigger RCE via the Outlook Preview Pane makes this a “one-click” or “zero-click” threat, which is highly effective during holiday periods when users are more likely to interact with urgent-looking emails. Its inclusion in the CISA KEV catalog underscores the reality that this is not a theoretical threat, but a weaponized one.
Strobes Recommendation
- Prioritize Workstations: Deploy the December cumulative update to all end-user workstations first, as these are the primary targets for phishing.
- Enable Attack Surface Reduction (ASR): Configure ASR rules to “Block all Office applications from creating child processes.”
- Scan Attachments: Update email gateway signatures to detect the specific CSS/HTML patterns associated with this MSHTML exploit.
- Audit Logs: Review Windows Error Reporting (WER) logs for repeated crashes in web-rendering DLLs over the last 14 days.
Bottomline
This is a critical, weaponized RCE targeting the core of the Windows ecosystem. It turns simple document viewing into a system-level breach. If your organization relies on Microsoft 365 or Windows-based endpoints, patching this vulnerability is the single most important action to take before the 2025 holiday break.
CVE-2025-68615 | Net-SNMP snmptrapd Remote Stack-Based Buffer Overflow
CVE-2025-68615 is a critical vulnerability in the Net-SNMP package (specifically the snmptrapd daemon) that allows unauthenticated remote attackers to execute arbitrary code or cause a permanent Denial of Service (DoS) via a single malformed UDP packet. By sending a specifically crafted SNMP Trap message with an oversized OID (Object Identifier) or Variable Binding, attackers can trigger a stack-based buffer overflow, gaining control over the instruction pointer on the host system. This vulnerability has seen a surge in exploit attempts targeting Linux-based networking equipment and IoT gateways throughout December 2025.
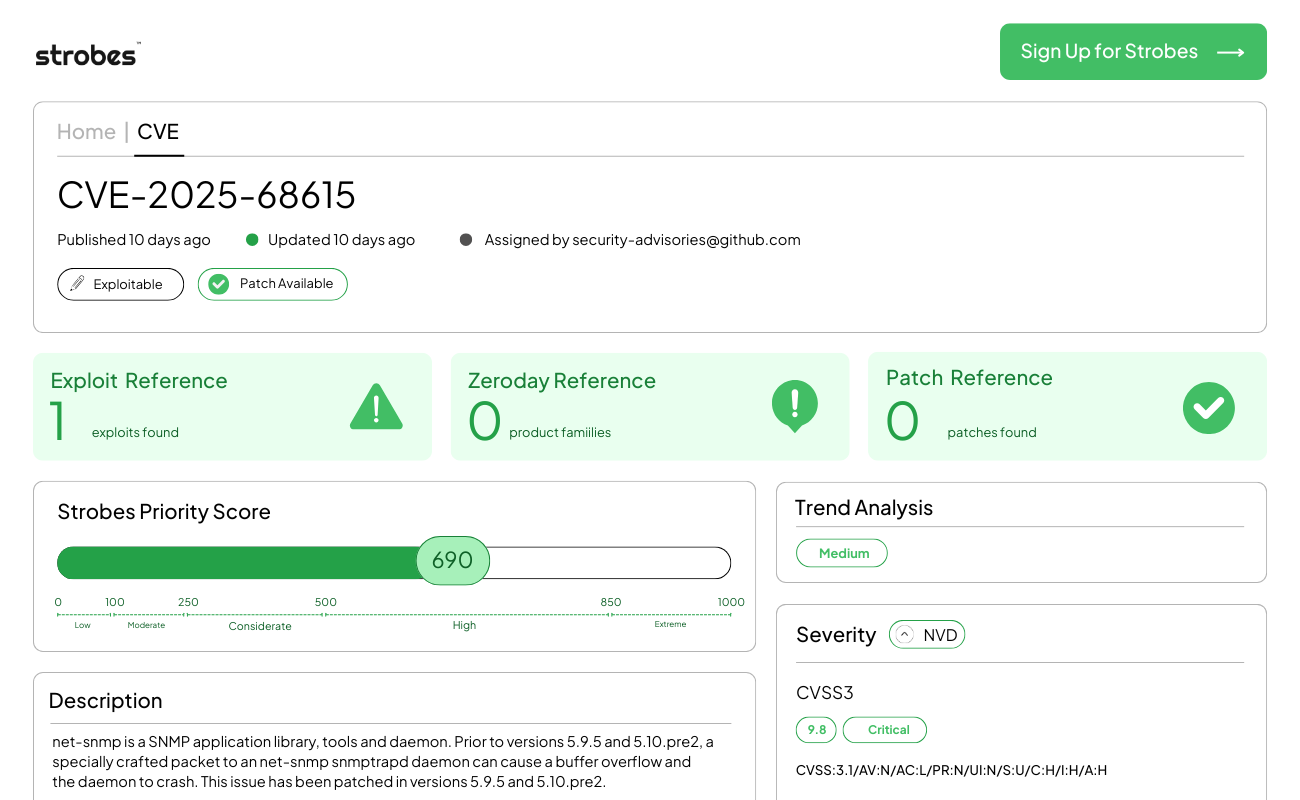
Vulnerability Breakdown
CVE-2025-68615 stems from inadequate bounds checking within the snmp_parse_varbind function used by the snmptrapd service. When processing incoming Trap messages, the daemon fails to validate the length of data mapped to specific internal buffers before copying it into the stack.
An attacker can transmit a UDP packet to port 162 containing an ASN.1 encoded SNMP Trap with a deeply nested or excessively long variable binding. This overflows the allocated buffer memory, allowing the attacker to overwrite the return address of the function. Because snmptrapd often runs with root or high-level system privileges to manage network events, a successful exploit provides the attacker with full administrative control over the underlying Linux or Unix host.
Impact of Exploitation
If an attacker succeeds, likely outcomes include:
- Remote Code Execution (RCE): Attackers can deploy persistent backdoors or reverse shells directly into the core network monitoring infrastructure.
- Infrastructure Blindness: By crashing the Trap daemon or taking control of it, attackers can suppress legitimate security alerts from other network devices, masking a larger attack.
- Lateral Movement: Monitoring servers often have trusted access to the rest of the management network; a compromise here serves as a perfect pivot point for targeting the entire data center.
- IoT Botnet Recruitment: Since Net-SNMP is embedded in millions of edge devices, this CVE is highly attractive for large-scale botnet operators.
Mitigation & Patching
| Mitigation Step | Status / Action |
| Patch Availability | Update Net-SNMP to version 5.9.5 or apply the backported vendor patch. Most Linux distributions (Ubuntu, RHEL, Debian) released security advisories on Dec 12, 2025. |
| Exploit Activity | High. Public proof-of-concept (PoC) code has been integrated into automated scanning frameworks, targeting exposed industrial control systems (ICS). |
| Immediate Workaround | If patching is not possible, disable the snmptrapd service if not strictly required, or implement strict ACLs to only allow SNMP traffic from known, trusted IP addresses. |
| Hardening Tip | Enable ASLR (Address Space Layout Randomization) and DEP (Data Execution Prevention). Use a non-root user to run the SNMP daemon if your configuration allows. |
| Detection | Monitor system logs for snmptrapd segmentation faults or unexpected crashes. Check for unusual binary executions originating from the SNMP service process. |
| Hunt Suggestions | Use network-level monitoring to identify unusually large UDP packets (exceeding 1500 bytes) directed at port 162. Search for “0x41414141” (A’s) patterns in packet payloads. |
Why is this CVE in Our Top Picks of the Month?
CVE-2025-68615 represents a “Foundation-level” risk. Net-SNMP is one of the most widely deployed open-source libraries in the world, found in everything from enterprise servers to smart power grids. The ability to achieve unauthenticated RCE via a connectionless protocol (UDP) makes this extremely easy to weaponize at scale. As organizations closed for the holiday season in late 2025, this vulnerability became a primary target for “quiet” infiltration into critical management segments.
Strobes Recommendation
- Update Now: Prioritize patching for all internet-facing gateways and core monitoring servers (Zabbix, Nagios, SolarWinds instances utilizing Net-SNMP).
- Filter Traffic: Ensure that UDP port 162 is blocked at the perimeter and only accessible via a secure management VPN.
- Verify Integrity: Audit all scripts and binaries in /usr/sbin/ and /tmp/ for unauthorized modifications if the SNMP service has recently restarted unexpectedly.
- Rotate Community Strings: If a compromise is suspected, consider all SNMP community strings (v1/v2c) and v3 credentials compromised and initiate a rotation.
Bottomline
Critical, remotely exploitable buffer overflow in a ubiquitous network service. This is a high-priority event for any organization managing Linux infrastructure or IoT devices. A failure to secure the SNMP daemon could result in a silent takeover of your network monitoring and management plane.
Final Take
The Top CVEs of December 2025 prove that threat actors are shifting focus toward the core building blocks of modern infrastructure. Between the massive blast radius of React2Shell and the hidden supply chain risks in Apache Tika, the perimeter is no longer a physical line. It is now every line of code in your environment.
Don’t let your security strategy rely on yesterday’s headlines. Shift from reactive patching to proactive intelligence by surfacing breaking CVEs, live exploit activity, and shifting risk scores the second they trigger on the Strobes VI Platform.