December 2025 closed the year with several high-impact data breaches across retail, education, healthcare research, and telecom. These incidents were not driven by a single cause. Some stemmed from misconfigured systems, others from ransomware, and several from third-party access failures. What ties them together is the scale and sensitivity of the exposed data. Social Security numbers, financial records, and personal identifiers were involved across multiple cases.
This roundup breaks down the most significant data breaches reported in December 2025, explaining what happened, what data was exposed, how organisations responded, and the clear lessons security teams can take forward.
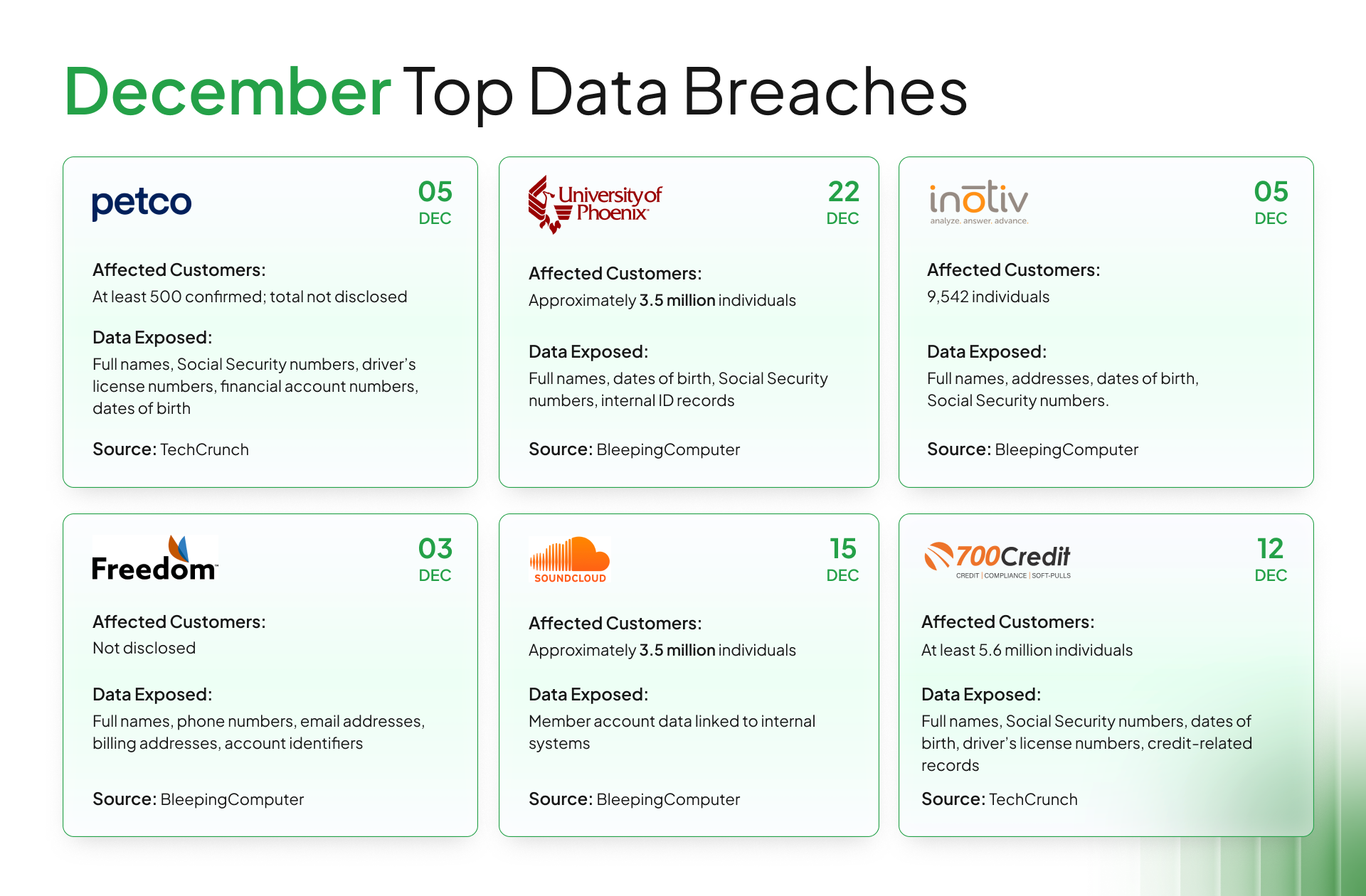
 1. Petco Confirms Security Lapse Exposing Sensitive Customer Data
1. Petco Confirms Security Lapse Exposing Sensitive Customer Data
Incident Overview:
Petco announced a security lapse that resulted in a data breach. The company found that a setting within one of its software applications incorrectly allowed certain files to be accessible from the internet without proper restrictions, then it took action to fix the issue and remove exposed files.
What Data Was Exposed:
The company’s public notices (filed with state attorneys general) indicate that the exposed data included extremely sensitive personal details such as:
- Customer full names
- Social Security numbers
- Driver’s license numbers
- Financial account numbers (including credit and debit card numbers)
- Dates of birth
Number of Affected Individuals:
Petco did not disclose the full total. Notices filed suggest at least 500 customers in California were impacted, along with additional affected individuals in Massachusetts, Montana, and Texas, but the full scope remains unspecified.
Business Impact:
The breach has significant implications for customer trust and company compliance, triggering mandatory notifications and possible legal scrutiny. Exposure of highly sensitive identifiers can lead to increased costs and heightened regulatory attention.
Company Response:
Once the issue was discovered, Petco corrected the application setting, removed public access to the files, and began notifying affected customers. The company offered free identity theft and credit monitoring services to impacted individuals in states where this is required.
Key Lesson:
Security misconfigurations can expose deeply personal data even without an external attack, showing the importance of proactive configuration checks, access controls, and ongoing audits to safeguard sensitive information.
Date of Breach: December 5, 2025
Source: TechCrunch
2. University of Phoenix Data Breach Affects 3.5 Million Individuals
Incident Overview:
The University of Phoenix disclosed a data breach after unauthorised access was identified within a system operated by a third-party service provider. The intrusion involved data linked to students, applicants, and employees. The university was alerted after the service provider detected suspicious activity affecting stored records.
What Data Was Exposed:
According to official disclosures, the accessed data may include full names, dates of birth, Social Security numbers, and internal identification information associated with academic or employment records. The university stated that passwords, payment card data, and banking details were not involved.
Number of Affected Individuals:
The breach impacted approximately 3.5 million individuals. This includes current and former students, applicants, and staff members whose information was stored within the affected system.
Business Impact:
The incident led to significant operational strain across compliance, legal, and IT teams. It triggered large-scale notification requirements and attracted regulatory attention due to the volume and sensitivity of the exposed data. The exposure also raised concerns related to identity misuse risks for affected individuals.
Company Response:
The University of Phoenix notified impacted individuals and offered credit monitoring and identity protection services. It also reviewed vendor access practices and assessed controls related to third-party data handling and oversight.
Key Lesson:
Third-party service providers often store large volumes of sensitive personal information. Without strict oversight and access controls, vendor-managed systems can become a major source of exposure for educational institutions.
Date of Breach: December 22, 2025
Source: BleepingComputer
3. Pharma firm Inotiv discloses data breach after ransomware attack
Incident Overview:
In December 2025, Inotiv disclosed a data breach after confirming that a ransomware attack led to unauthorised access to internal systems. The disclosure followed a forensic review that determined personal information was accessed and taken during the incident.
What Data Was Exposed:
The exposed data included personal information such as full names, addresses, dates of birth, and Social Security numbers. Inotiv stated that no payment card details or banking information were involved.
Number of Affected Individuals:
Inotiv confirmed that 9,542 individuals were impacted by the breach and received formal notification letters in December 2025.
Business Impact:
The breach resulted in system disruption, mandatory disclosure requirements, and increased compliance and legal review. As a pharmaceutical research services provider, the incident also created operational strain while investigations and notifications were carried out.
Company Response:
Inotiv secured affected systems, engaged external cybersecurity specialists, and notified law enforcement authorities. The company also initiated direct communication with impacted individuals and offered identity monitoring services as part of its response actions.
Key Lesson:
Ransomware incidents in research-focused organisations can lead to direct exposure of personal records. Clear asset visibility, timely detection, and structured response actions help reduce data exposure and downstream risk.
Date of Breach: December 5, 2025
Source: BleepingComputer
4. Freedom Mobile Discloses Data Breach Exposing Customer Data
Incident Overview
Freedom Mobile confirmed a data breach after detecting unauthorised access to one of its internal systems. The company stated that the activity was identified through internal monitoring and was linked to a third-party system used to support customer operations. Following confirmation, Freedom Mobile initiated containment measures and began notifying impacted customers.
What Data Was Exposed
According to the disclosure, the exposed information primarily included customer account details such as full names, phone numbers, email addresses, billing addresses, and account identifiers. Freedom Mobile stated that payment card numbers, banking details, and government-issued identification were not accessed as part of the incident.
Number of Affected Individuals
Freedom Mobile has not published an exact figure for the total number of impacted customers. However, the company acknowledged that a subset of its customer base was affected, and notifications were issued to all individuals whose information was confirmed to be involved.
Business Impact
The breach resulted in operational and reputational impact for Freedom Mobile. Customer support volumes increased following public disclosure, and internal teams were required to prioritise forensic analysis, regulatory reporting, and customer communication. The incident also drew attention from privacy regulators due to the exposure of personal customer data.
Company Response
Freedom Mobile stated that it immediately secured the affected system, restricted unauthorised access, and engaged external cybersecurity experts to investigate the incident. Impacted customers were notified and provided guidance on monitoring account activity. The company also confirmed that additional security controls were implemented to reduce the risk of similar incidents going forward.
Key Lesson
This breach highlights the risk introduced by third-party systems handling customer information. Strong vendor oversight, continuous monitoring, and strict access controls remain critical for protecting customer data and limiting the impact of unauthorised access.
Date of Breach: December 3, 2025
Source: BleepingComputer
5. SoundCloud Member Data Breach and VPN Disruption
Incident Overview
SoundCloud confirmed unauthorized access to internal systems that resulted in member data being taken. The incident also caused disruption to internal VPN access, prompting an immediate security response and system review. The breach was publicly confirmed in December 2025.
What Data Was Exposed
SoundCloud stated that member data linked to internal systems was accessed. While full details were not publicly itemized, the data was associated with user accounts rather than core streaming content.
Number of Affected Individuals
The company did not release an exact figure at the time of disclosure.
Business Impact
The breach disrupted internal access systems and raised trust concerns among users. Operational teams were required to rotate credentials and re-establish secure access.
Company Response
SoundCloud restricted access, reviewed authentication controls, and initiated internal audits. Impacted users were notified as required.
Key Lesson
Identity and remote access systems remain high-value targets. Weak controls or compromised credentials can expose user data even when production services remain stable.
Date of Breach: December 15, 2025
Source: Bleeping Computer
6. Data Breach at 700Credit Exposes Data of 5.6 Million Individuals
Incident Overview
700Credit, a U.S.-based provider of credit reporting and compliance tools for auto dealerships and lenders, disclosed a data breach that exposed sensitive personal information. The company confirmed that an unauthorised party gained access to certain internal systems that stored consumer data used for credit checks and risk assessments.
The breach came to light after abnormal activity was detected within the environment, prompting an internal investigation and external forensic review.
What Data Was Exposed
Based on regulatory filings and public disclosures, the compromised data includes a mix of high-risk personal and financial information, such as:
- Full names
- Social Security numbers
- Dates of birth
- Driver’s license numbers
- Credit-related records used by lenders and auto dealers
This type of data is commonly used in credit eligibility checks, which increases the risk of identity fraud if misused.
Number of Affected Individuals
700Credit confirmed that at least 5.6 million individuals were impacted by the breach.
The affected population includes consumers whose data was processed through dealerships, financial institutions, and lending partners that rely on 700Credit’s services.
Business Impact
The breach carries serious consequences across multiple fronts:
- Regulatory scrutiny due to the scale and sensitivity of exposed information
- Mandatory breach notifications across multiple U.S. states
- Increased legal and compliance costs
- Reputational damage among lenders, auto dealers, and financial partners
For businesses that rely on third-party credit data providers, this incident also raises concerns about vendor risk and downstream exposure.
Company Response
700Credit stated that it took immediate steps to secure its systems once the issue was identified. Actions reported include:
- Restricting unauthorised access
- Engaging cybersecurity and forensic experts
- Notifying affected individuals and regulators
- Offering credit monitoring and identity protection services to impacted users
The company has also indicated that it is reviewing internal controls and access management practices.
Key Lesson
This breach highlights a recurring issue across financial data ecosystems. Organisations handling credit and identity data must maintain strict visibility over who can access sensitive systems, how that access is monitored, and how third-party platforms are governed. A single lapse at a service provider can expose millions of individuals and create cascading risk for every partner connected to that platform.
Date of Breach: December 12, 2025
Source: TechCrunch
Conclusion:
The data breaches reported in December 2025 point to a clear issue. Exposure did not come from advanced tactics alone. It came from misconfigured applications, weak third-party controls, and limited visibility into where sensitive data actually lived. Once access was gained, organisations were forced into reactive mode, dealing with notifications, legal pressure, and customer trust damage.
This is exactly where Strobes Security changes the outcome. Strobes helps you continuously track assets, identify exposure early, prioritise what truly matters, and validate risk before it turns into an incident. Instead of reacting after data is exposed, teams gain clarity on misconfigurations, vendor risks, and attack paths while there is still time to act.
Explore how Strobes Security helps teams identify, prioritise, and reduce real exposure.
Book a platform walkthrough and see how continuous exposure management works.

 1. Petco Confirms Security Lapse Exposing Sensitive Customer Data
1. Petco Confirms Security Lapse Exposing Sensitive Customer Data