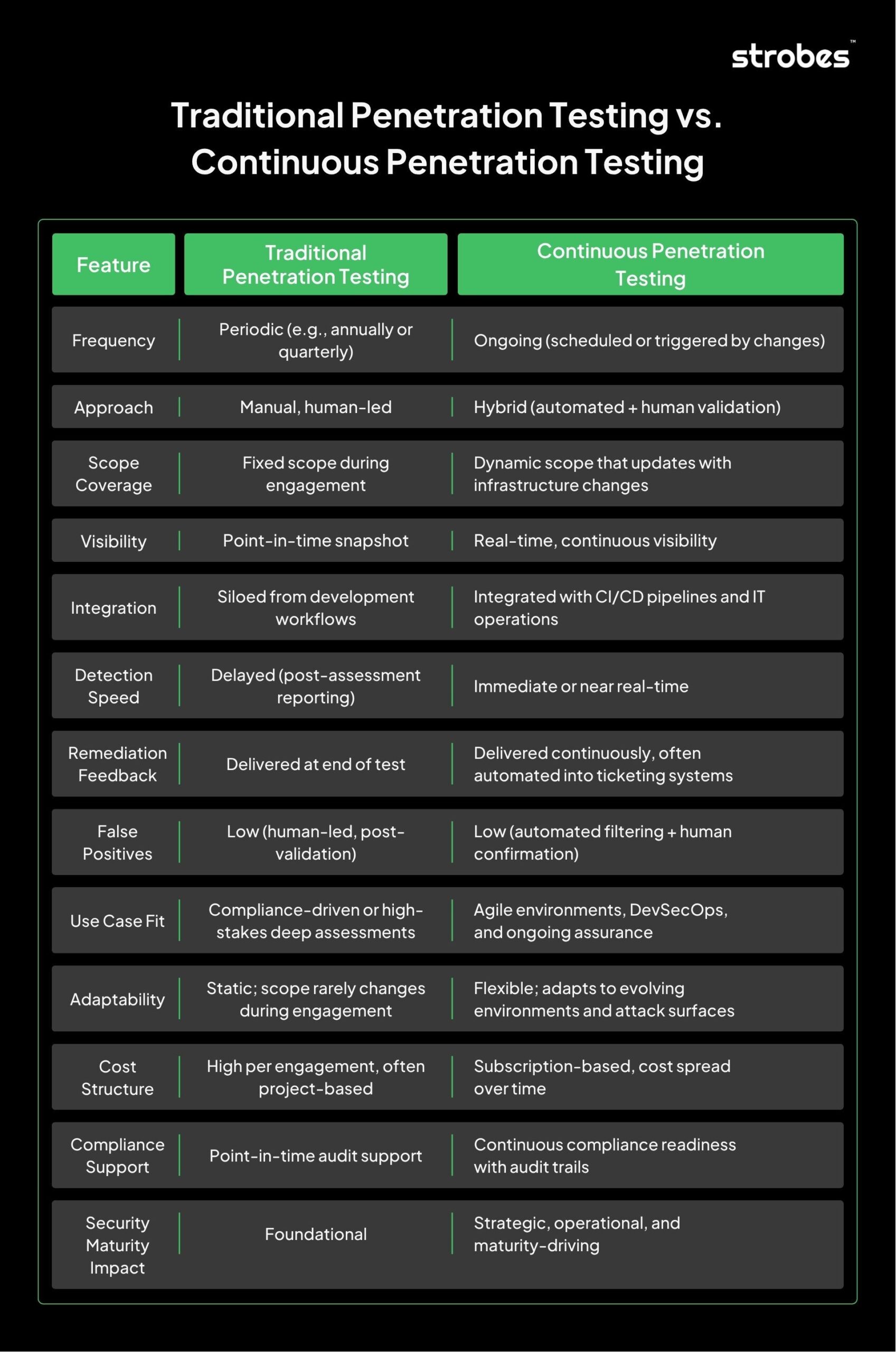
Continuous penetration testing is a modern security approach that performs real-time or near-real-time simulations of cyberattacks against an organization’s digital assets, ensuring vulnerabilities are identified and addressed as they emerge. Unlike traditional penetration testing, which provides only periodic snapshots of security posture, continuous penetration testing (continuous penetration testing) aligns with the pace of agile development, dynamic infrastructure, and constantly changing environments.
In practice, continuous penetration testing operates as a hybrid of automation and human expertise. It continuously scans systems for potential entry points and security flaws, validates findings to reduce false positives, and integrates seamlessly into DevOps pipelines. This ensures that every code push, configuration change, or deployment is evaluated for risk in real time, before it can be exploited.
Industry Insight
When continuous testing is more than a buzzword and embedded into how organizations secure change in real time, it shifts from a tool to a core security function.
What Continuous Penetration Testing Isn’t?
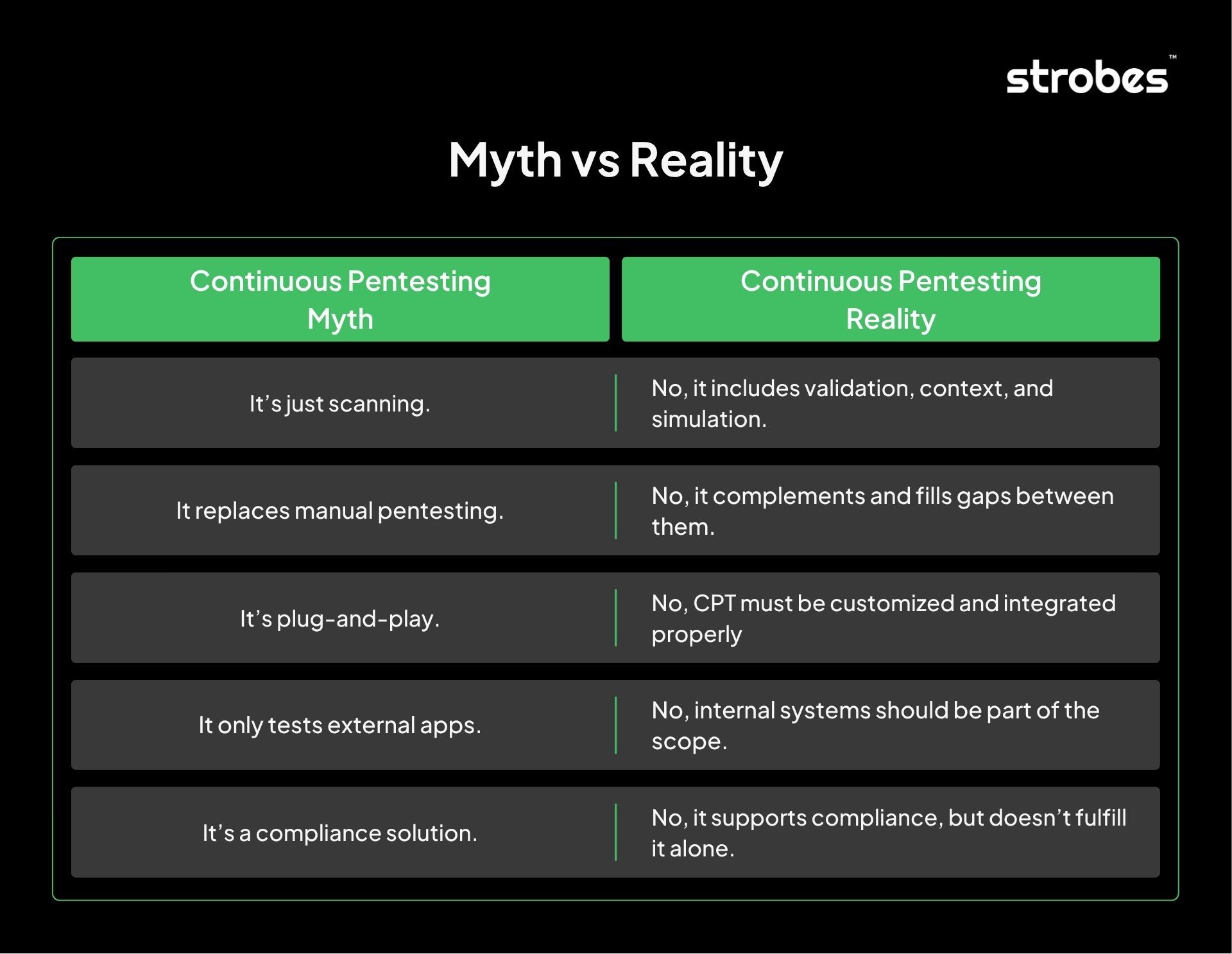
To fully understand the value of continuous penetration testing (continuous penetration testing), it’s equally important to clarify what it does not do. Misconceptions in the market, often fueled by vague vendor claims or surface-level tooling, can lead to misplaced expectations or ineffective implementations. Let’s clear the air.
It’s Not Just Automated Vulnerability Scanning
Automated scanners are a component of continuous penetration testing, but they are not the whole system. Scanners identify known vulnerabilities using signatures and scripts. They are fast and scalable, but limited. They can’t:
- Chain vulnerabilities together to simulate real attack paths.
- Identify logic flaws, authorization bypasses, or multi-stage exploits.
- Accurately determine business impact without context.
Continuous penetration testing combines automation with expert validation and adversarial simulation, making it significantly more advanced and reliable than automated scanning alone.
It’s an Extension and Not a Replacement for Manual Pentests
Some believe continuous penetration testing eliminates the need for traditional, human-led penetration tests. That’s not accurate. In reality:
- Continuous penetration testing automates repetitive testing and enhances coverage between formal pen test engagements.
- It provides continuous visibility and maintains a baseline of risk detection.
- However, deep-dive, scenario-based testing, especially for applications, APIs, and custom business logic, still requires dedicated manual assessments.
It’s Not One-Size-Fits-All
Continuous penetration testing isn’t a plug-and-play checkbox solution. Its effectiveness depends on:
- Proper scoping
- Integration into DevOps and remediation workflows
- Organizational readiness and follow-through
A continuous penetration testing program must be tailored to the organization’s environment, development velocity, and risk appetite. Without customization, even the best continuous penetration testing tool becomes just another alert generator.
It’s Not Only for External-Facing Assets
Another common misconception is that continuous testing is only valuable for public web applications. In reality, a mature continuous penetration testing program should test:
- Internal applications and services
- APIs and microservices
- Cloud environments and IAM policies
- Remote access points, VPNs, and third-party integrations
True continuous penetration testing ensures complete attack surface coverage, both internal and external.
It’s Not a Compliance Shortcut
Continuous penetration testing supports compliance, but it’s not a substitute for it. Relying on continuous penetration testing alone doesn’t satisfy the requirements of many standards (e.g., PCI DSS, ISO 27001), which often demand:
- Independent assessments
- Formal documentation
- Manual verification of high-risk systems
Instead, continuous penetration testing should be seen as a compliance enabler, helping maintain continuous readiness and reducing audit friction by surfacing risk in real time.
How Does Continuous Penetration Testing Work?
Continuous penetration testing operates through an orchestrated combination of automation, human expertise, and seamless integration with existing development and IT workflows. Unlike static, point-in-time assessments, this method is dynamic, constantly evolving to reflect the infrastructure it protects. Here’s how the process functions in practice:
1. Dynamic Asset Discovery
The foundation of continuous testing is a constantly updated understanding of the organization’s digital footprint. This includes:
- Automated discovery of domains, IP ranges, APIs, cloud instances, and shadow assets.
- Real-time adjustment of scope as new infrastructure is deployed or existing components change.
- Elimination of manual tracking gaps that often result in overlooked vulnerabilities.
By continuously mapping the attack surface, the system ensures no asset is left untested.
2. Automated Vulnerability Scanning and Enumeration
Once assets are identified, automated tools simulate adversarial behavior to uncover vulnerabilities:
- Scheduled and event-triggered scans adapted to deployment frequency.
- Coverage of common CVEs, misconfigurations, insecure protocols, and outdated dependencies.
- Correlation engines that filter redundant findings and group related issues for context.
Automation brings speed and breadth to the testing process, ensuring new vulnerabilities are flagged shortly after they appear.
3. Expert Validation and Attack Simulation
Automation alone cannot assess business logic flaws, exploit chains, or subtle misconfigurations. That’s why expert penetration testers are embedded in the loop:
- Manual verification of critical findings to reduce false positives.
- Logical flaw testing and contextual risk analysis based on real-world attack patterns.
- Chaining of seemingly low-risk vulnerabilities to simulate full exploitation scenarios.
This hybrid approach ensures that results are not just detected, they’re credible, actionable, and business-relevant.
4. Prioritized Reporting and Real-Time Alerting
Validated vulnerabilities are immediately categorized and routed to the appropriate teams through:
- Real-time integration with ticketing systems (e.g., Jira, ServiceNow) and collaboration tools.
- Risk-based prioritization models that consider asset sensitivity, exploitability, and external exposure.
- Executive dashboards and analyst views tailored for both operational and strategic oversight.
This tight feedback loop enables rapid triage and resolution without disrupting workflow velocity.
5. Seamless CI/CD Integration
Security testing is embedded into the software development lifecycle without impeding agility:
- Security checkpoints are inserted into CI/CD pipelines, allowing pre- and post-deployment scanning.
- Development teams receive contextual alerts that map directly to the lines of code or configurations involved.
- Release cycles remain uninterrupted, while vulnerabilities are addressed earlier and with lower remediation costs.
Continuous penetration testing complements agile delivery by aligning security enforcement with the pace of innovation.
6. Long-Term Learning and Metrics
Over time, continuous testing evolves based on organizational behavior and threat intelligence:
- Analytics highlight recurring vulnerabilities, slow remediation trends, and at-risk systems.
- Benchmarking against internal SLAs and external compliance requirements.
- Data-driven insights feed back into security awareness, tooling improvements, and development training.
This iterative process helps organizations not just maintain security, but mature it over time.
7. Comprehensive Coverage Across the Environment
Continuous penetration testing spans all relevant digital surfaces, including:
- Public and internal web applications
- Cloud infrastructure (AWS, Azure, GCP)
- APIs, microservices, and containers
- VPNs, access controls, internal tools, and third-party integrations
This breadth ensures that every critical component is tested, not just perimeter assets.
Key Features of Continuous Penetration Testing
- Real-time, automated vulnerability scanning
- Expert-led validation for accurate findings
- Seamless DevOps integration
- Continuous asset discovery and scope adjustment
- Risk-based reporting and remediation workflows
- Security that evolves with your infrastructure
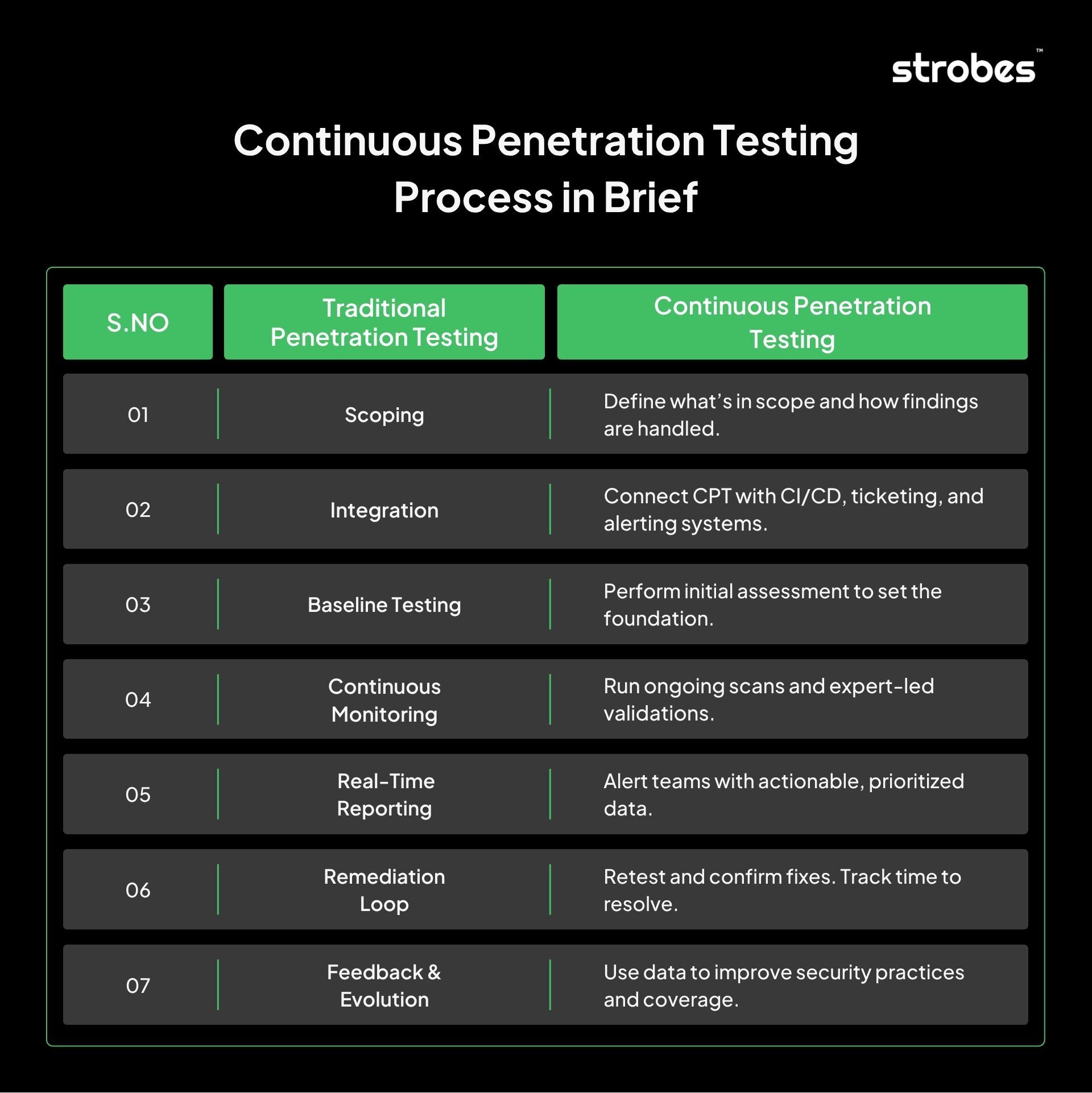
What Is the Continuous Penetration Testing Process?
The continuous penetration testing process outlines how security testing is conducted and maintained on an ongoing basis. It’s not a one-time engagement, but a structured, repeatable cycle that integrates with development, operations, and remediation workflows. This process ensures that security testing is aligned with the speed of infrastructure and application changes. Here’s how the process typically works from start to finish:
1. Define Scope and Objectives
Before testing begins, the organization and testing provider establish:
- Which assets and environments will be tested.
- What frequency or event-based triggers will be used.
- How findings will be reported and handled.
This step ensures the testing program is targeted, relevant, and aligned with business goals.
2. Set Up Integrations
Continuous testing is most effective when it’s integrated with existing systems. This may include:
- CI/CD pipelines for automated testing on deployment.
- Ticketing platforms like Jira or ServiceNow for remediation tracking.
- Notification systems like Slack or email for real-time alerts.
The goal is to embed security into existing workflows rather than operate separately.
3. Perform Initial Baseline Assessment
A full assessment is performed to establish a security baseline. This includes:
- Asset discovery and attack surface mapping.
- Automated scans for known vulnerabilities.
- Manual validation of high-impact findings.
This baseline provides a starting point for ongoing monitoring and identifies immediate issues that require attention.
4. Enable Continuous Testing
With the system configured and initial findings resolved, continuous testing begins. This phase includes:
- Scheduled and change-triggered scanning.
- Ongoing asset discovery as environments evolve.
- Expert validation of critical vulnerabilities.
Testing is now active and running continuously in the background.
5. Real-Time Detection and Reporting
As new vulnerabilities are found:
- They are validated and prioritized based on severity, impact, and exploitability.
- Alerts are sent directly to the appropriate teams.
- Findings are documented with reproduction steps and remediation guidance.
This ensures issues are visible and actionable without unnecessary noise.
6. Remediation and Retesting
Once a fix is implemented:
- The system can retest the vulnerability automatically or upon request.
- Closed-loop reporting confirms that the issue has been resolved.
- Metrics are updated to reflect resolution time and frequency.
This supports faster, verified remediation and minimizes repeat issues.
7. Continuous Feedback and Refinement
Over time, organizations can use testing data to:
- Identify recurring issues or weak spots.
- Improve development practices based on common security findings.
- Adjust scope, integrations, or testing frequency based on operational needs.
This makes continuous testing not just reactive, but proactive and informative.
Why is Continuous Penetration Testing Important?
Continuous penetration testing plays a key role in modern security programs. It provides timely detection of vulnerabilities, supports agile development, and enables better control over security posture across changing environments. Unlike periodic tests, it operates continuously to align with how systems are developed, deployed, and maintained today.
1. Reduces Exposure Between Traditional Tests
Scheduled penetration tests leave long intervals during which new vulnerabilities can go unnoticed. Continuous testing reduces this risk by:
- Monitoring for changes and new assets.
- Running tests when updates occur.
- Alerting teams to issues shortly after they emerge.
This reduces the time a vulnerability remains unaddressed.
2. Supports Agile and DevOps Workflows
In fast-paced development environments, waiting for periodic security reviews is not practical. Continuous penetration testing addresses this by:
- Running tests as part of CI/CD pipelines.
- Providing feedback during or after deployments.
- Allowing teams to fix issues without delaying releases.
It fits naturally into modern development practices.
3. Identifies Real-World Threats Quickly
Attackers use automation and shared tools to find vulnerabilities shortly after they appear. Continuous penetration testing addresses this by:
- Simulating common attack patterns continuously.
- Including human review for critical or complex findings.
- Prioritizing risks based on potential impact.
This helps security teams stay ahead of real threats.
4. Enhances Readiness for Audits and Reviews
Many compliance standards now expect evidence of continuous monitoring. Continuous penetration testing supports this by:
- Keeping a running history of tests and results.
- Providing documented remediation efforts.
- Aligning with security control frameworks.
It helps maintain a consistent security posture.
5. Improves Time to Remediate Issues
Identifying a vulnerability is not enough; fixing it quickly is what reduces risk. Continuous penetration testing improves response by:
- Integrating with ticketing systems to route findings directly.
- Prioritizing based on severity and context.
- Enabling re-tests once fixes are in place.
This supports a more efficient remediation cycle.
6. Contributes to Long-Term Security Improvements
Over time, continuous penetration testing data shows patterns in how and where issues occur. Organizations can use this to:
- Spot recurring weaknesses.
- Measure how quickly vulnerabilities are resolved.
- Adjust development or security practices based on trends.
This makes security more measurable and manageable.
Manual pentests take weeks.
Get validated results faster with Strobes PTaaS.
Summary
- Continuous testing closes the gap between periodic assessments.
- It works well with fast-moving development teams.
- It helps detect and respond to threats faster.
- It supports audit and compliance efforts.
It improves visibility into how security practices are performing over time.
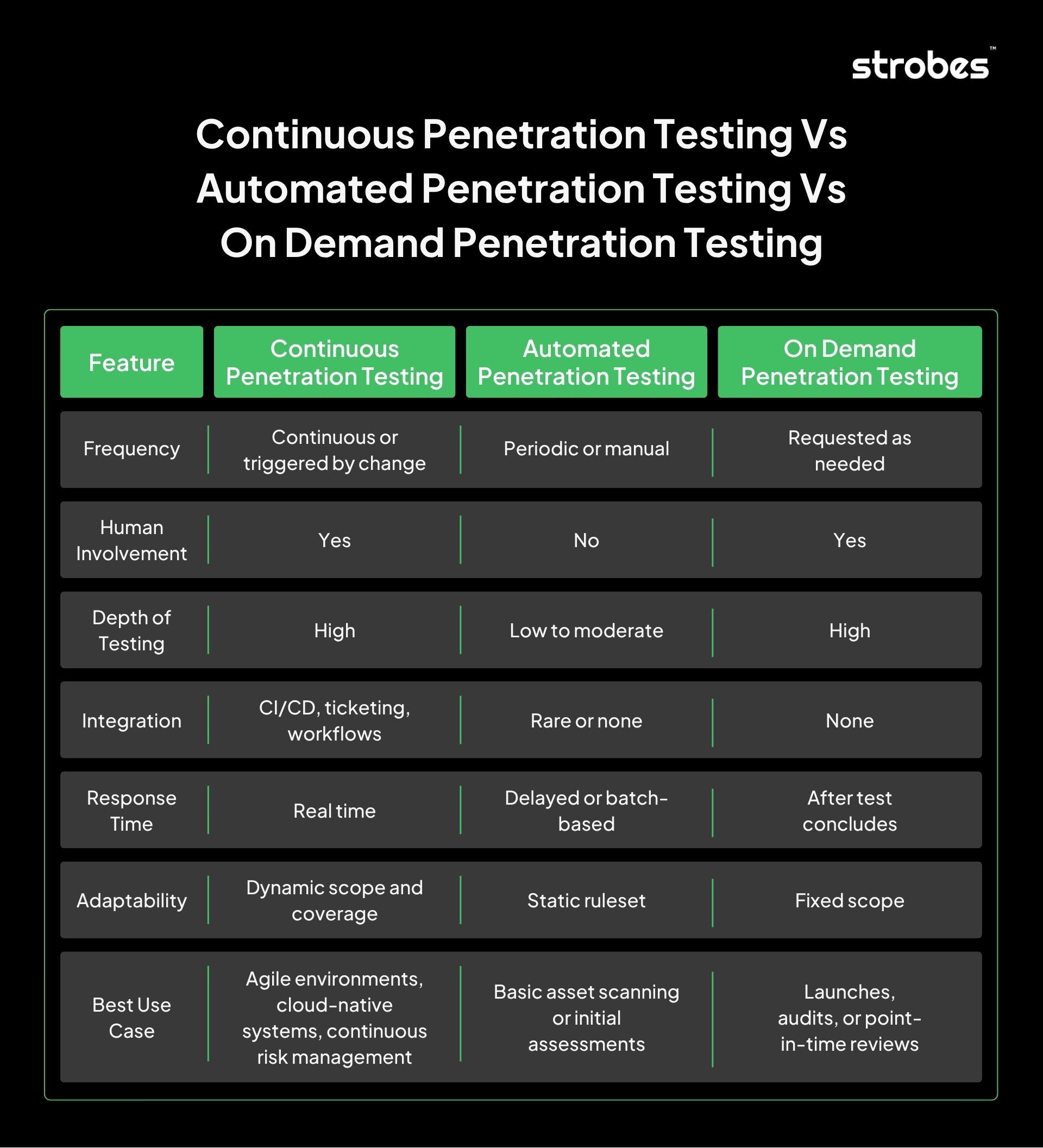
How is Continuous Penetration Testing Different from Automated and On-Demand Pentesting?
The terms continuous, automated, and on-demand penetration testing are often used interchangeably. However, each approach serves a different purpose, offers varying levels of depth, and fits differently within modern security programs. Understanding the distinctions is essential for choosing the right testing model for your organization.
Continuous Penetration Testing Offers Integrated and Ongoing Security
This approach blends automated scanning with expert validation and runs continuously or in response to system changes. It adapts to new assets and integrates with DevOps and IT workflows.
Key Characteristics
- Testing triggered by deployments, updates, or a schedule
- Includes manual validation of critical findings
- Results delivered in real time through integrated systems
- Scales with asset growth and environmental changes
Automated Penetration Testing Prioritizes Speed Over Context
Automated penetration testing relies entirely on software tools. While it provides broad coverage quickly, it lacks the ability to interpret context or simulate complex attack paths.
Key Characteristics
- Runs predefined vulnerability checks without manual input
- Limited to known issues and pattern recognition
- Often generates false positives
- Does not account for logical flaws or business impact
On Demand Penetration Testing Provides Deep But Static Assessments
On demand penetration testing is scheduled as needed and performed manually. It offers in-depth analysis but lacks the responsiveness or continuity of continuous penetration testing.
Key Characteristics
- Conducted manually by ethical hackers on request
- Focused on a specific system or release
- Results are delivered after the engagement ends
- No integration with real-time systems or pipelines
Key Takeways
- Continuous testing aligns with modern infrastructure and development practices.
- Automated testing offers speed but limited insight.
- On demand testing delivers depth but lacks continuity.
Only continuous penetration testing combines the benefits of both speed and depth while remaining aligned with how organizations operate today.
Static reports don’t help in CI/CD.
Strobes gives real-time dashboards with risk context.
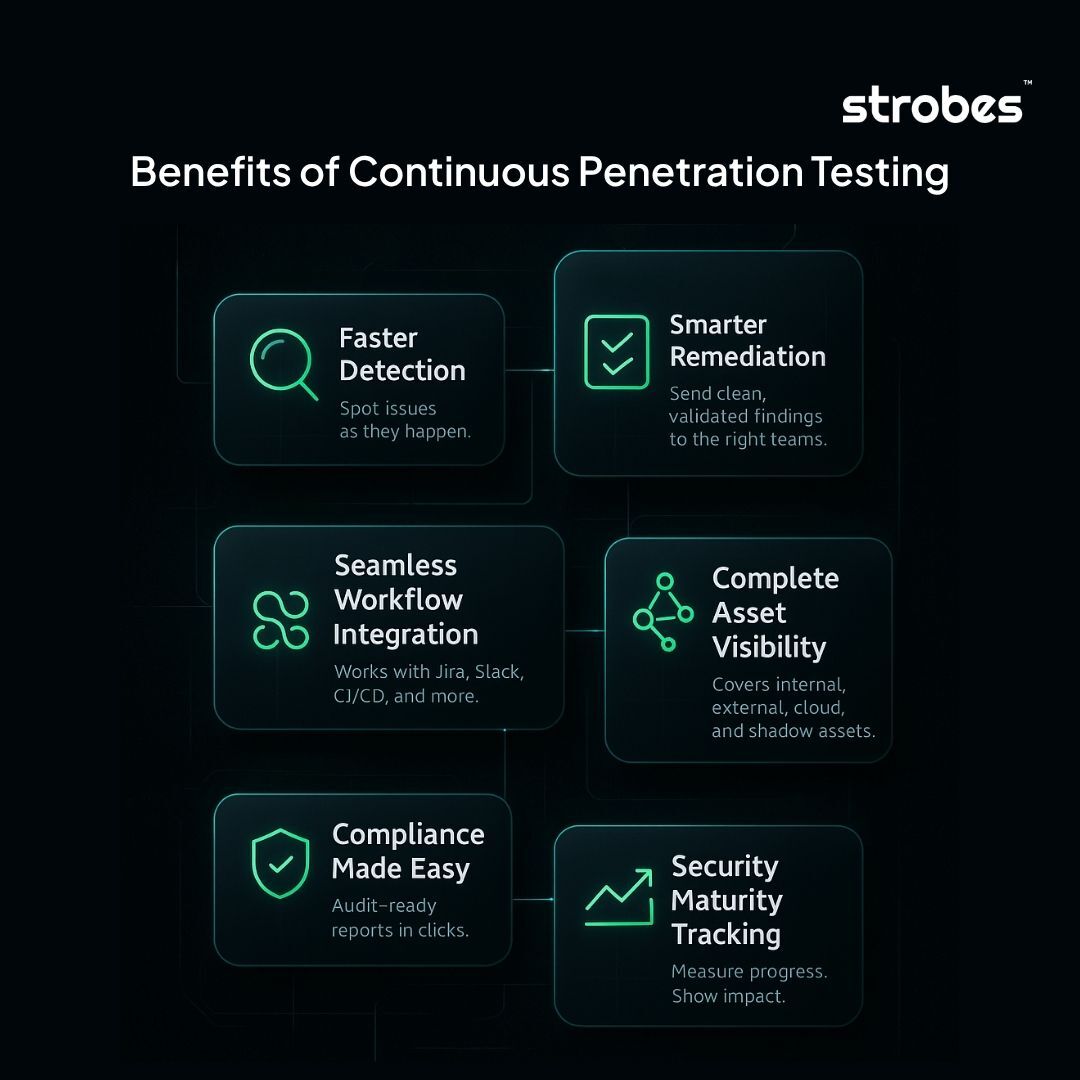
What are the Benefits of Continuous Penetration Testing?
Continuous penetration testing offers practical, measurable advantages for organizations that need timely vulnerability detection, streamlined remediation, and full visibility into their security posture. Its real value lies in how it integrates with day-to-day operations while providing depth, accuracy, and consistency.
Timely Detection of Vulnerabilities
Continuous penetration testing reduces the time between the introduction of a vulnerability and its discovery. Whether triggered by a code deployment or configuration change, it ensures:
- Immediate testing of new assets or updates
- Faster identification of critical issues
- Reduced window of exposure to attackers
Efficient and Targeted Remediation
Instead of waiting for post-engagement reports, continuous penetration testing provides actionable findings in real time:
- Validated vulnerabilities are sent directly to relevant teams
- Integration with ticketing systems accelerates response
- Less time spent reviewing false positives or incomplete data
Alignment With Agile and DevOps Workflows
Modern development cycles demand speed. Continuous penetration testing keeps pace by:
- Embedding testing into CI/CD pipelines
- Running checks automatically during code pushes or infrastructure changes
- Providing feedback without disrupting release schedules
Comprehensive Asset and Risk Visibility
continuous penetration testing constantly updates its scope to reflect real-world changes. This ensures:
- Discovery of new services, APIs, and endpoints as they appear
- Ongoing coverage of internal and external systems
- A real-time view of security status across environments
Audit Readiness and Compliance Support
With continuous penetration testing, organizations are better prepared for audits and regulatory reviews:
- All testing activity is logged and reportable
- Evidence of timely remediation supports compliance frameworks
- Demonstrates a repeatable, auditable security process
Optimized Use of Security Resources
By automating routine checks and focusing human expertise where it’s needed, continuous penetration testing helps:
- Reduce manual testing workloads
- Prioritize high-impact risks
- Improve operational efficiency across security and development teams
Continuous Improvement Through Measurable Insights
continuous penetration testing generates data that can be used to strengthen security posture over time:
- Trends in vulnerability types and resolution speed
- Metrics that inform team performance and training needs
- Visibility into recurring issues or systemic weaknesses
When Should an Organization Use Continuous Penetration Testing?
Not every organization needs continuous penetration testing immediately, but for many, it becomes essential once infrastructure, deployment speed, or compliance requirements reach a certain threshold. The decision to implement continuous penetration testing should be based on practical needs, not trends.
Here are the situations where continuous penetration testing offers clear, tangible value.
Frequent Code Deployments and Infrastructure Changes
Organizations that release updates regularly, especially in agile or DevOps environments, benefit significantly from continuous penetration testing. It ensures:
- Every release is tested for vulnerabilities
- Changes to infrastructure trigger immediate assessment
- New risks are detected in step with development speed
If changes happen faster than manual reviews can keep up, continuous penetration testing fills the gap.
Cloud-Native or Dynamic Environments
Infrastructures that rely on containers, serverless functions, or auto-scaling environments are in constant flux. Continuous penetration testing helps:
- Discover new assets as they are spun up or reconfigured
- Test systems that might exist briefly or change frequently
- Keep pace with dynamic cloud workloads
Traditional testing struggles to track these changes, while continuous penetration testing adapts automatically.
Organizations Pursuing DevSecOps
For teams aiming to integrate security into their development pipelines, continuous penetration testing is a natural fit. It supports:
- Automated security checks during builds or deployments
- Immediate feedback on security risks in new code
- Alignment between development, operations, and security
Continuous penetration testing reinforces a shift-left strategy without slowing down releases.
Environments With a Broad or Growing Attack Surface
As organizations expand their digital footprint, through new applications, third-party integrations, or external APIs, the risk of unnoticed exposures increases. Continuous penetration testing ensures:
- Coverage across known and newly discovered assets
- Centralized testing across distributed environments
- Continuous monitoring of both internal and external systems
It scales as the organization grows, maintaining consistent visibility.
Compliance-Driven Industries
Industries that face regular audits or must adhere to strict security frameworks benefit from continuous penetration testing’s built-in documentation and audit readiness. It helps:
- Maintain continuous evidence of security control effectiveness
- Demonstrate testing frequency and remediation history
- Reduce the effort required during audit cycles
This is especially relevant in finance, healthcare, SaaS, and regulated tech sectors.
Organizations Seeking Faster Risk Resolution
If security teams are often reacting late or struggling to keep up with remediation, continuous penetration testing helps by:
- Delivering validated, prioritized findings in real time
- Integrating with existing ticketing and remediation tools
- Supporting retesting to confirm fixes
It enables a more responsive, measurable security process.
How Continuous Testing Supports Compliance?
Many compliance frameworks now expect security testing to be continuous, not periodic. Point-in-time assessments are no longer sufficient to demonstrate consistent control effectiveness or risk management. Continuous penetration testing helps organizations meet these evolving requirements.
Meets Ongoing Control Expectations
Regulatory frameworks such as SOC 2, ISO 27001, PCI DSS, HIPAA, and GDPR increasingly emphasize the need for continuous monitoring. CPT provides:
- Real-time evidence of ongoing vulnerability testing
- Logs of remediation actions with timestamps
- Documented validation of high-risk findings
This makes it easier to demonstrate that security controls are not just present, but active and effective.
Simplifies Audit Preparation
Traditional penetration test reports often age quickly and require manual collection before an audit. With CPT:
- Historical data is automatically captured and stored
- Dashboards provide live views of testing activity and closure rates
- Reports can be filtered by compliance control or business unit
This reduces audit prep time and increases confidence in the outcome.
Aligns With Risk-Based Compliance Models
CPT helps shift compliance from checkbox exercises to meaningful risk reduction. By continuously testing critical assets and providing context-aware findings, organizations can:
- Map vulnerabilities to business impact
- Show how risks are managed proactively, not reactively
- Satisfy auditors with quantifiable, real-time security data
How to Implement Continuous Penetration Testing Effectively?
Successfully adopting continuous penetration testing requires more than selecting a tool or service. It involves aligning people, processes, and platforms to ensure continuous penetration testing delivers consistent, actionable results. When implemented thoughtfully, continuous penetration testing becomes a scalable and sustainable part of an organization’s security operations.
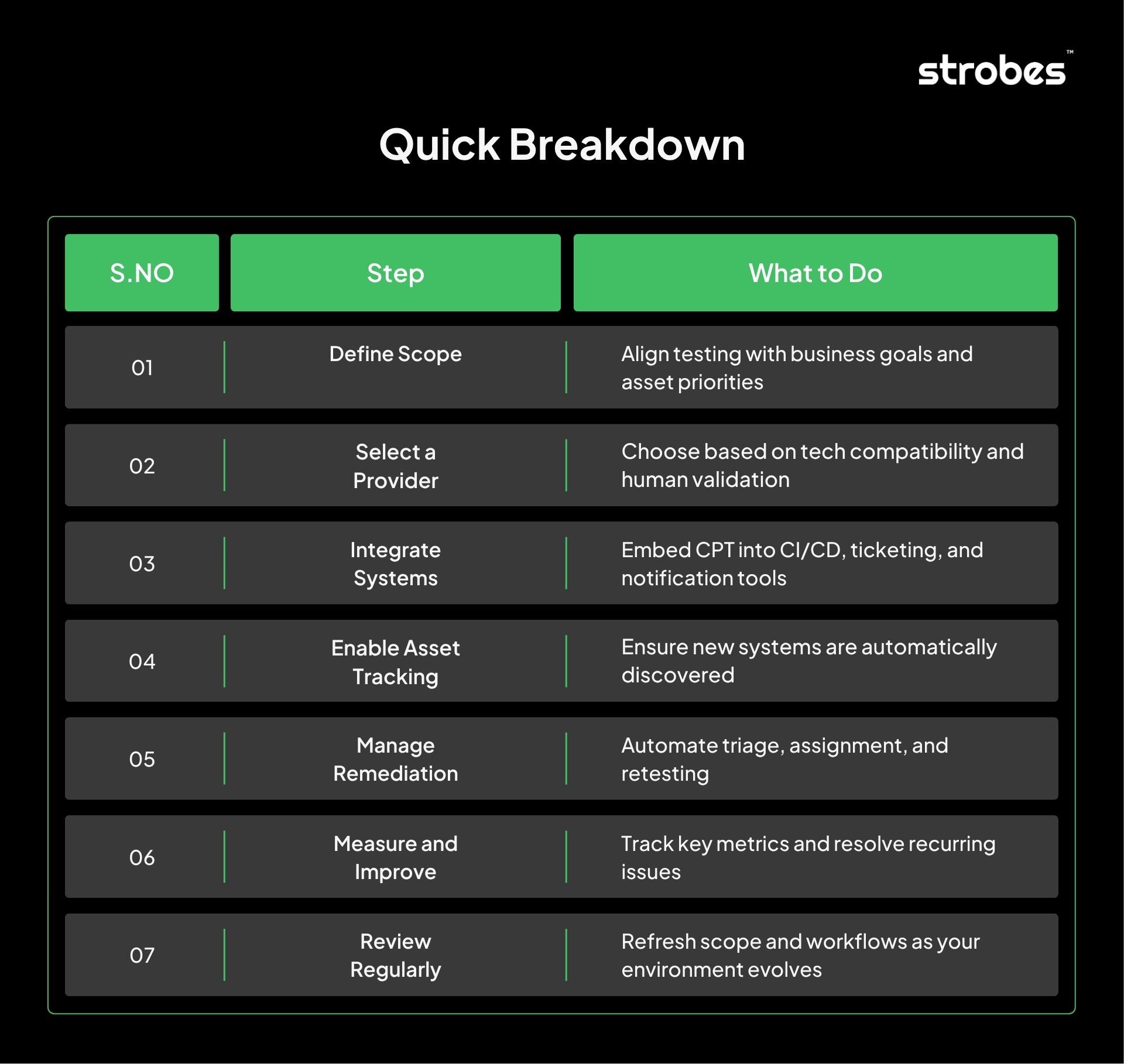
Start With a Clear Scope and Objectives
Before onboarding a continuous penetration testing platform or provider, define what you aim to achieve:
- Which systems, applications, or environments should be tested
- How frequently testing should occur (scheduled or triggered)
- What success looks like (faster remediation, improved visibility, etc.)
A focused scope prevents alert overload and ensures relevance.
Choose the Right Platform or Service Model
Evaluate continuous penetration testing providers based on your technical environment, integration needs, and internal capacity. Consider:
- Support for hybrid environments (cloud, on-premises, APIs)
- Integration with CI/CD pipelines and ticketing systems
- Whether testing includes human validation or is fully automated
The right fit depends on your operational model and risk profile.
Integrate With Development and IT Workflows
continuous penetration testing must operate within your existing systems, not outside of them. This includes:
- Pushing validated vulnerabilities to tools like Jira, ServiceNow, or Slack
- Triggering scans automatically after deployments or infrastructure changes
- Providing developers with actionable, context-rich findings
The goal is to streamline remediation, not add overhead.
Enable Ongoing Asset Discovery
To remain effective, continuous penetration testing must account for continuous changes in the environment. Ensure that:
- New assets are automatically added to the testing scope
- Dynamic infrastructure changes (e.g., containers, subdomains) are captured
- Shadow IT or forgotten systems don’t go untested
A living attack surface demands a flexible testing scope.
Establish a Remediation and Retesting Process
Finding vulnerabilities is only useful if they are resolved. Set up workflows for:
- Prioritizing findings based on severity and business impact
- Assigning responsibility to the correct teams
- Retesting automatically once issues are marked as fixed
Track remediation times and closure rates to measure performance.
Monitor Metrics and Trends
Use continuous penetration testing data to improve your program over time. Focus on metrics such as:
- Mean time to remediate (MTTR)
- Number and type of vulnerabilities found
- Recurring issues by team, system, or deployment
This data provides feedback for improving both security practices and development processes.
Conduct Periodic Reviews and Adjustments
Environments change. So should your continuous penetration testing program. Regularly review:
- Scope and asset coverage
- Integration health and workflow alignment
- Testing frequency and validation quality
Adjust as needed to ensure continuous penetration testing remains relevant and effective.
How Strobes PTaaS Brings Continuous Penetration Testing to Life?
Implementing continuous penetration testing isn’t just about changing your testing schedule, it’s about using the right platform to make it operational, scalable, and truly embedded into your organization. This is where Strobes PTaaS stands out.
Strobes isn’t just another scanner or reporting tool. It’s the engine that transforms continuous testing from theory into execution.
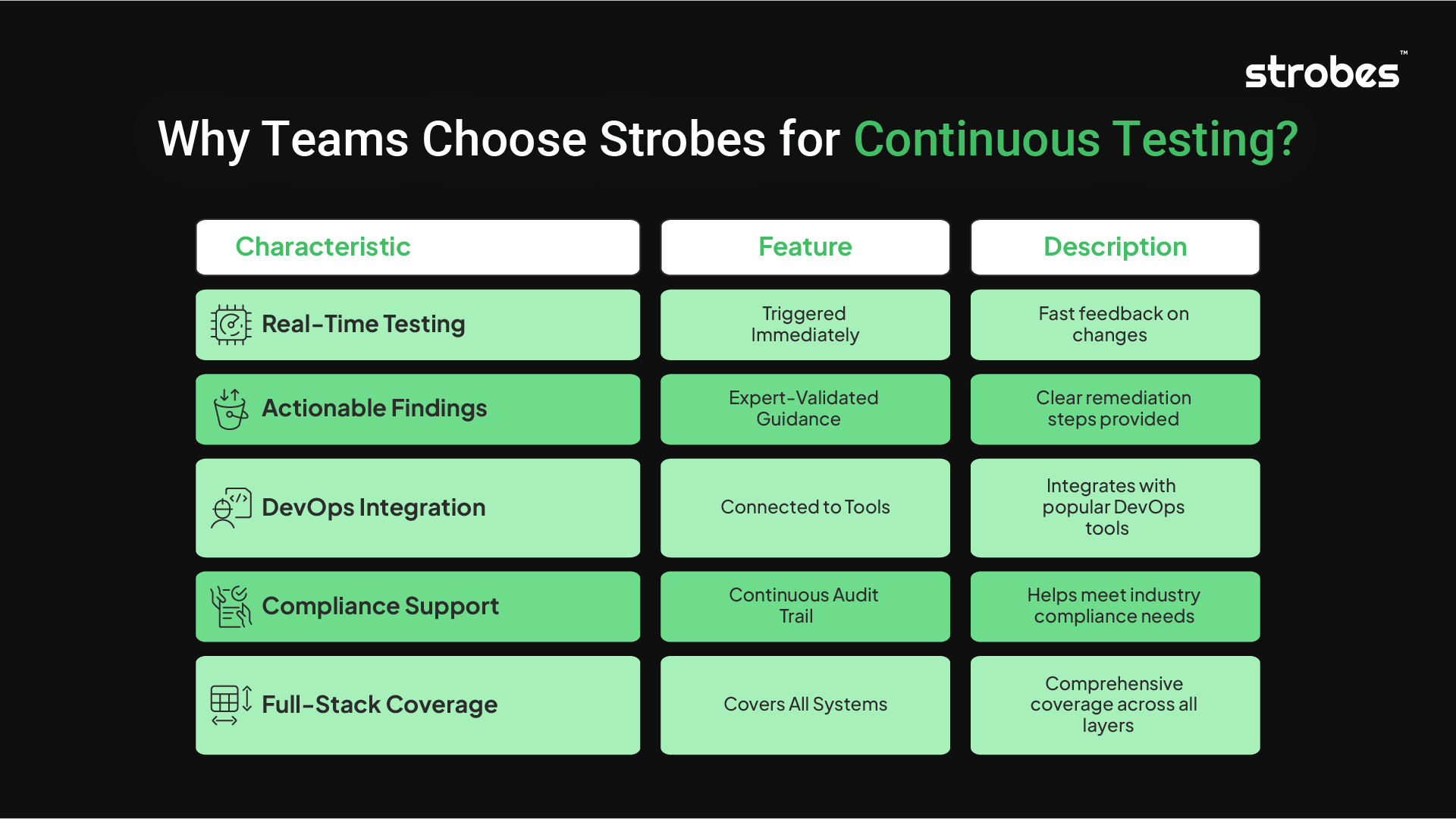
A Platform Designed for Security at DevOps Speed
Modern environments move fast, Strobes move with them. Whether your team pushes daily updates or manages dozens of cloud assets, the platform responds in real time.
- Trigger tests automatically based on code pushes or infra changes
- Keep pace with dynamic environments through live asset tracking
- Ensure nothing falls outside your security scope, not even for a day
Smart Testing Backed by Human Expertise
Automated scanners are great for speed. But context, depth, and risk understanding require people. Strobes combine both seamlessly.
- Automated testing to catch routine issues quickly
- Expert-led validation to confirm impact and filter noise
- Real-world exploit simulation to separate minor alerts from major threats
With Strobes, you don’t just find issues, you understand which ones matter.
Built-In Collaboration for Rapid Fixes
What’s the point of finding vulnerabilities if they just sit in a PDF? Strobes turns insights into action.
- Integrates with Jira, GitHub, ServiceNow, and Slack
- Sends issues directly to the teams that can fix them
- Provides remediation guidance with context, so developers don’t waste time deciphering vague alerts
Security becomes part of the workflow, not a blocker to it.
Visibility That Goes Beyond Metrics
Most platforms give you a dashboard. Strobes give you a decision layer.
- Track how fast vulnerabilities are being resolved
- Visualize where recurring issues keep appearing
- Show security progress to leadership in language they understand
This isn’t just reporting, it’s proof that your security program is moving forward.
From Continuous Testing Strategy to Reality
If you’re serious about continuous penetration testing, you need a platform that understands more than just vulnerabilities. You need one that understands how your teams work, how your systems evolve, and how decisions get made. And that’s Strobes.
What Are the Common Challenges of Continuous Penetration Testing and How to Overcome Them?
Implementing continuous penetration testing brings operational advantages, but also introduces challenges related to scale, accuracy, and coordination. Recognizing these challenges early allows organizations to plan effectively and get the most value from their investment.
Managing False Positives and Alert Noise
One of the most frequent issues is the volume of findings generated by automated scans. Without context or validation, many alerts may be irrelevant, leading to alert fatigue and delayed responses.
To address this, choose continuous penetration testing solutions that include manual verification or advanced filtering capabilities. Limit scope to high-value assets and prioritize alerts by severity, exploitability, and impact. Integrate alerts into tools your teams already use to reduce friction and improve response times.
Maintaining Updated Asset Coverage
Dynamic infrastructures often create gaps in asset visibility. Systems that are spun up temporarily or modified frequently may fall outside the test scope, leaving blind spots.
This challenge can be reduced by enabling continuous asset discovery and integrating continuous penetration testing with cloud APIs, infrastructure-as-code, and asset management tools. Regular audits of asset inventory ensure nothing critical is missed.
Integrating With Development and Operations
If continuous penetration testing operates in isolation, testing results may not reach the teams responsible for remediation. Without integration, vulnerabilities may sit unresolved or be deprioritized.
Effective programs push findings into ticketing and workflow tools like Jira, GitLab, or ServiceNow, and include clear remediation guidance. Embedding security into CI/CD and involving security champions across teams can help ensure continuous penetration testing findings are actioned.
Keeping Testing in Sync With Deployment Velocity
When development cycles move quickly, testing schedules must keep pace. Relying on fixed intervals or manual triggers may result in outdated or incomplete assessments.
continuous penetration testing should be configured to run in response to deployments, code changes, or infrastructure updates. Automating triggers based on activity ensures continuous coverage without requiring manual scheduling.
Making Sense of continuous penetration testing Metrics
Continuous penetration testing platforms produce a wealth of data, but not all teams have the time or expertise to interpret it effectively. Without proper analysis, opportunities for improvement can be missed.
Focus on metrics that reflect impact, such as time to remediate, issue recurrence, and coverage over time. Tailor dashboards to specific roles and use findings in retrospectives to drive ongoing improvements.
Demonstrating Value Across the Organization
Leadership may question whether continuous penetration testing justifies its cost, especially compared to traditional assessments. Demonstrating ROI can be difficult if results are only measured in technical terms.
Translate continuous penetration testing outcomes into business-relevant metrics, reduced risk exposure, improved compliance posture, fewer emergency patches. Compare before-and-after stats to show measurable improvements in operational efficiency.
What Is the Future of Continuous Penetration Testing?
As organizations increasingly adopt cloud-native architectures, rapid development cycles, and automated workflows, continuous penetration testing is positioned to become a foundational layer in enterprise security programs. The model is already shifting from reactive assessments to proactive, integrated security operations, and this trend will continue to accelerate.
Here’s what the future of continuous penetration testing is likely to include:
Wider Adoption of Continuous Testing Models
Continuous penetration testing is currently more common among high-growth tech firms and regulated industries, but adoption is spreading across mid-sized organizations and traditional enterprises. As tooling matures and integration becomes simpler, more security teams will:
- Replace or augment periodic testing with continuous approaches
- Normalize continuous penetration testing as part of standard security programs
- Justify adoption through faster detection and measurable outcomes
Stronger Integration With Security and IT Ecosystems
continuous penetration testing tools will evolve to connect more deeply with other components of the security stack, including:
- Security Information and Event Management (SIEM)
- Extended Detection and Response (XDR)
- Vulnerability management platforms
- DevOps monitoring and observability tools
This will create unified views of risk and help organizations correlate vulnerability data with threat activity, asset importance, and incident response.
Increased Use of Artificial Intelligence and Automation
AI and machine learning will continue to enhance continuous penetration testing capabilities. These improvements will help:
- Predict and simulate attacker behavior more realistically
- Prioritize vulnerabilities with greater accuracy based on context and intent
- Automate complex attack paths for validation without full human effort
However, human oversight will remain essential for interpreting edge cases, logic flaws, and strategic exploitation.
Tighter Alignment With Regulatory and Risk Frameworks
As regulators increasingly focus on continuous security assurance, continuous penetration testing will play a larger role in:
- Demonstrating control effectiveness across frameworks (e.g., NIST, ISO, SOC 2)
- Supporting continuous compliance audits and evidence gathering
- Mapping testing activity to specific risk areas and business functions
Security teams will use continuous penetration testing data not just for operations, but to improve governance reporting and board-level communication.
Expansion Into Internal and Non-Traditional Attack Surfaces
Continuous penetration testing will expand its reach beyond perimeter testing and external apps to include:
- Internal applications and services
- Third-party integrations and SaaS platforms
- Employee endpoints and access layers
- Supply chain and vendor-exposed systems
As digital ecosystems become more interconnected, testing scope will need to cover more than what’s visible from the outside.
Integration With Continuous Threat Exposure Management (CTEM)
Continuous penetration testing will likely become a core component of broader Continuous Threat Exposure Management strategies. This means:
- Combining attack surface management, risk-based vulnerability management, and application security posture management
- Providing a holistic view of risk, exposure, and exploitability
- Enabling organizations to prioritize and mitigate threats in context, not isolation
CTEM adoption will push continuous penetration testing from a tactical tool to a strategic framework for managing cyber risk continuously.
Stop relying on scanners alone.
👉 See how Strobes combines automation and expert validation. Book a demo with us.
Frequently Asked Questions
- Is continuous testing compatible with containers and serverless functions?
Absolutely, as long as the platform supports ephemeral assets and can scan based on deployment triggers in environments like Kubernetes or Lambda.
- What kind of audit evidence does continuous penetration testing generate?
You get logs, timestamps, remediation records, and retest results, perfect for demonstrating control effectiveness during audits or reviews.
- Can this model detect sensitive data exposure risks?
Yes. Properly scoped tests can include checks for exposed storage (e.g., S3 buckets), secrets in code, and misconfigured databases.
- How does continuous penetration testing fit into our secure development lifecycle?
Continuous penetration testing becomes part of CI/CD pipelines, scanning during build or deployment stages, supporting shift-left security without slowing releases.
- How does continuous testing differ from vulnerability scanning?
Vulnerability scans are automated checks. Continuous penetration testing adds human validation, exploit chaining, and context-aware assessments.