Even one unknown asset can become your weakest link
Asset Discovery
Stop flying blind. Strobes continuously maps every asset across cloud, on-prem, and third-party systems, giving you a real-time inventory without the manual work. No blind spots. Just full visibility you can trust.
You Can’t Protect What You Can’t See
Unseen Assets are Real Threats
Scanners Miss the Unknown
Wasted Effort, Misplaced Focus
Blind Spots Weaken Posture
Incomplete asset coverage distorts risk scoring and leaves critical gaps in your security framework.
Visibility is Vital for Compliance
Without full asset visibility, audit trails fail, putting compliance and trust at risk.
How Strobes Maps Every Asset and Closes Visibility Gaps?
Strobes doesn’t just build a list. It adds context. Using multiple discovery methods and real-time intelligence, it gives your team complete, actionable visibility across your digital footprint.
Continuous Discovery
Precise Asset Fingerprinting
Catches Shadow IT and Third-Party
Centralized Inventory with Built-In Intelligence
Assets are automatically organized by function, source, and exposure level. You can filter, tag, assign, or take action without sorting through clutter.
See the Full Asset Story with Strobes
Click into any asset, and you get a full picture in seconds. Strobes brings deep asset context right to your screen:
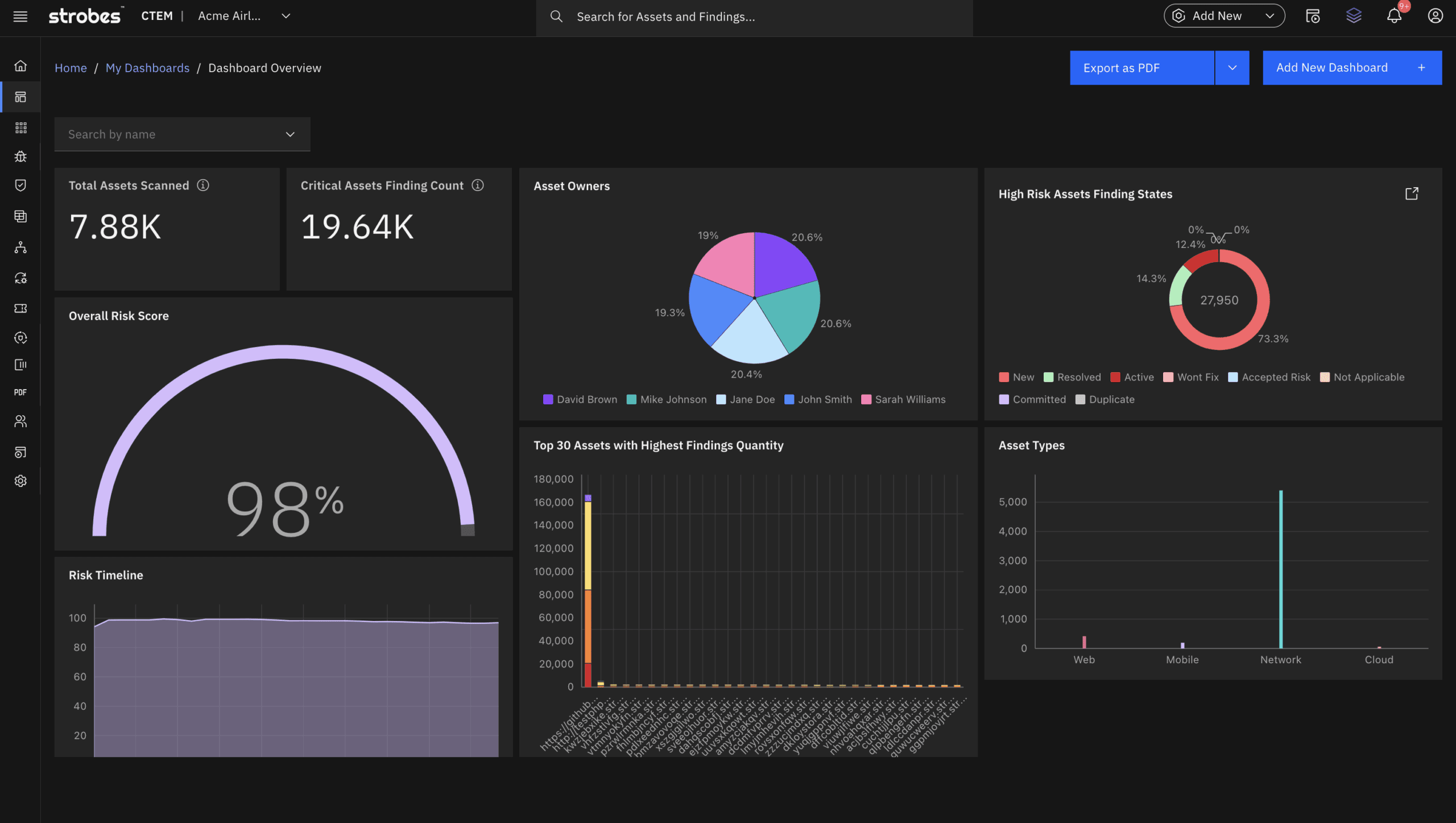
Risk Score
Calculated based on exposure, business sensitivity, and linked vulnerabilities.
Asset Snapshot
See details like IP, domain, OS, open ports, geolocation, and cloud provider.
Linked Vulnerabilities
Instantly view all associated vulnerabilities, their severity, status, and exploitability
Asset Tags and Ownership
Tag assets by department, owner, environment, or business unit for faster triage and clearer accountability.
Attack Surface Visibility
Track certificates, subdomains, associated users, exposed services, and misconfigurations, all tied back to this one asset.
How Strobes Turns Asset Discovery Into Action?
Strobes is where asset discovery begins and everything else follows. From correlation to remediation, it’s all handled in one connected platform.





