A security breach. Headlines scream, investors panic, and fingers get pointed. But what if you could anticipate an attack with the help of CTEM before it happens?
For years, organizations invested heavily in firewalls, intrusion detection, and other perimeter defenses. Then, compliance concerns pushed them to deploy vulnerability scanners and even take a more aggressive approach with red teaming and assumed breach practices.
This piecemeal strategy addressed specific needs, but lacked a unified view. Yet, despite these efforts, breaches still occur, often with catastrophic consequences. This is why companies are moving away from a vendor-by-vendor approach and seeking data consolidation, where a single platform offers a comprehensive security solution.
In fact, a Gartner survey reveals that 75% of organizations are actively pursuing security vendor consolidation. This shift towards consolidation paves the way for a powerful new approach: Continuous Threat Exposure Management
But what’s it?
If this is your first time hearing about continuous threat exposure management, rest assured it won’t be the last. Coined by Gartner, this cybersecurity buzzword is making waves—but unlike fleeting trends, it delivers real value. By the end of this read, you’ll see exactly why.
What is CTEM?
CTEM is a proactive security methodology that employs ongoing monitoring, evaluation, and mitigation strategies to address vulnerabilities across an organization’s expanding attack surface.
Many organizations rely on defensive security tools like AVs, MDRs, XDRs, and SIEMs to protect themselves from cyberattacks. These tools are crucial, but they take a reactive stance. They only spring into action when an attack is already underway.
For a more proactive approach, consider pentesting, attack surface management, and CTEM programs. These focus on the offensive side of security. Instead of waiting for an attack, they identify potential entry points within your organization and take steps to harden them.
Companies often invest heavily in defensive tools, but many run in passive mode with default configurations. This creates a false sense of security. Organizations might believe they’re well-protected until they conduct an offensive security test like a continuous threat exposure management program. When they assess their controls through simulated attacks, they often discover vulnerabilities that defensive tools could bypass. See beyond compliance.
A CTEM program actively hunts for weaknesses. It involves scoping your environment, discovering vulnerabilities, prioritizing them based on risk, validating potential attack paths, and then mobilizing teams to patch those vulnerabilities. This proactive approach significantly strengthens your overall security posture.
Why do Organizations Need CTEM? | What Problem is it Solving?
There is relentless pressure to secure your organization’s crown jewels—its data and critical infrastructure. Legacy security measures like firewalls were once enough, but today’s threat actors are more sophisticated and persistent.
Here’s the challenge: you can’t effectively defend what you don’t fully see. Traditional vulnerability management offers a snapshot in time, leaving blind spots that attackers can exploit.
This is where Continuous Threat Exposure Management comes in. It addresses a critical security gap by providing a comprehensive and ongoing view of your organization’s attack surface.
Let’s break down the specific problems CTEM solves:
- Unidentified and Unpatched Vulnerabilities: New vulnerabilities are discovered all the time. It goes beyond point-in-time scans, offering continuous identification of these weaknesses. This allows you to prioritize patching efforts and address the most critical risks before they’re weaponized.
- Shadow IT and Unmanaged Devices: The expanding attack surface extends beyond traditional IT assets. It actively discovers and profiles all connected devices, including those deployed outside of IT’s purview (shadow IT). This empowers you to assess their risk posture and implement appropriate controls.
- Misconfigurations and Security Gaps: Even with the most robust policies, misconfigurations can occur. It continuously monitors your systems and configurations, allowing you to proactively identify and rectify security gaps before attackers can leverage them.
- Evolving Threats and Techniques: The cyber threats are constantly growing. It incorporates threat intelligence to understand the latest attacker methods. This allows you to stay ahead of the curve and anticipate potential attacks, not just react to them.
- Limited Visibility and Incomplete Inventory: Traditional security tools often provide fragmented views of your attack surface. It offers a unified view of your entire IT ecosystem, giving you a clear picture of your vulnerabilities and exposures. This empowers you to make informed decisions about resource allocation and risk mitigation.
CTEM is not just a passing trend; it’s a fundamental shift in how CISOs manage cyber risk.
Akhil Reni, CTO Strobes
What’s the Hype About Continuous Threat Exposure Management?
Is it just a repackaged vulnerability management solution? Not quite. While vulnerability management is a part of CTEM, it takes a holistic approach that considers:
- Threat Intelligence: It integrates threat intelligence feeds to understand attacker methods and targets threats relevant to your organization.
- Attack Path Analysis: It goes beyond identifying vulnerabilities to understand how attackers might exploit them, prioritizing based on potential impact.
- Remediation Workflow: It facilitates streamlining the process of fixing vulnerabilities and implementing security controls.
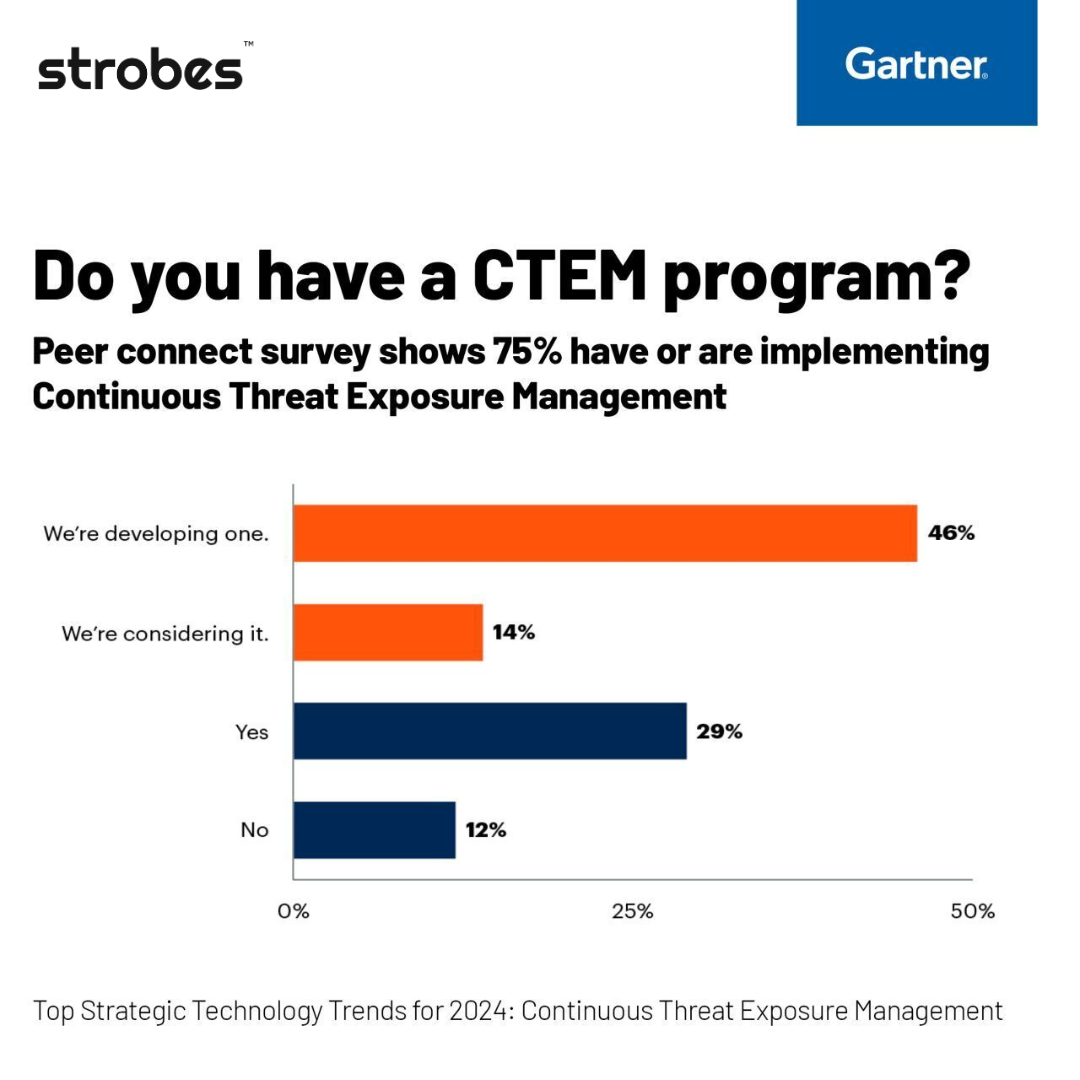
Source: Gartner
A recent Gartner® report shows a surge in CTEM adoption, with 71% of organizations recognizing its value. So, 7 out of 10 companies see CTEM as a key to proactive cyber risk management. The report further reveals that 60% of respondents are actively implementing these programs or seriously considering them.
Gartner Predicts a CTEM-Driven Future
The future of cybersecurity is all about continuous vigilance. Here’s a glimpse into what Gartner® predicts in its – Implement a Continuous Threat Exposure Management Program, July 2022 report:
- By 2026, Organizations prioritizing CTEM will be 3x less likely to suffer a breach.
- Traditional, automated remediation alone won’t be enough. It will play a crucial role in managing unpatchable attack surfaces.
- By 2025, security leaders who leverage CTEM across teams will see a 50% improvement in security optimization.
- By 2027, failing to manage remote access continuously will significantly increase the risk of breaches.
The 5 Stages of Continuous Threat Exposure Management
It is designed to continuously reduce your organization’s exposure to security threats. It’s not a single product, but a strategic approach supported by the right product(s). Here’s a breakdown of the five key stages involved in a successful implementation of Continuous Threat Exposure Management:
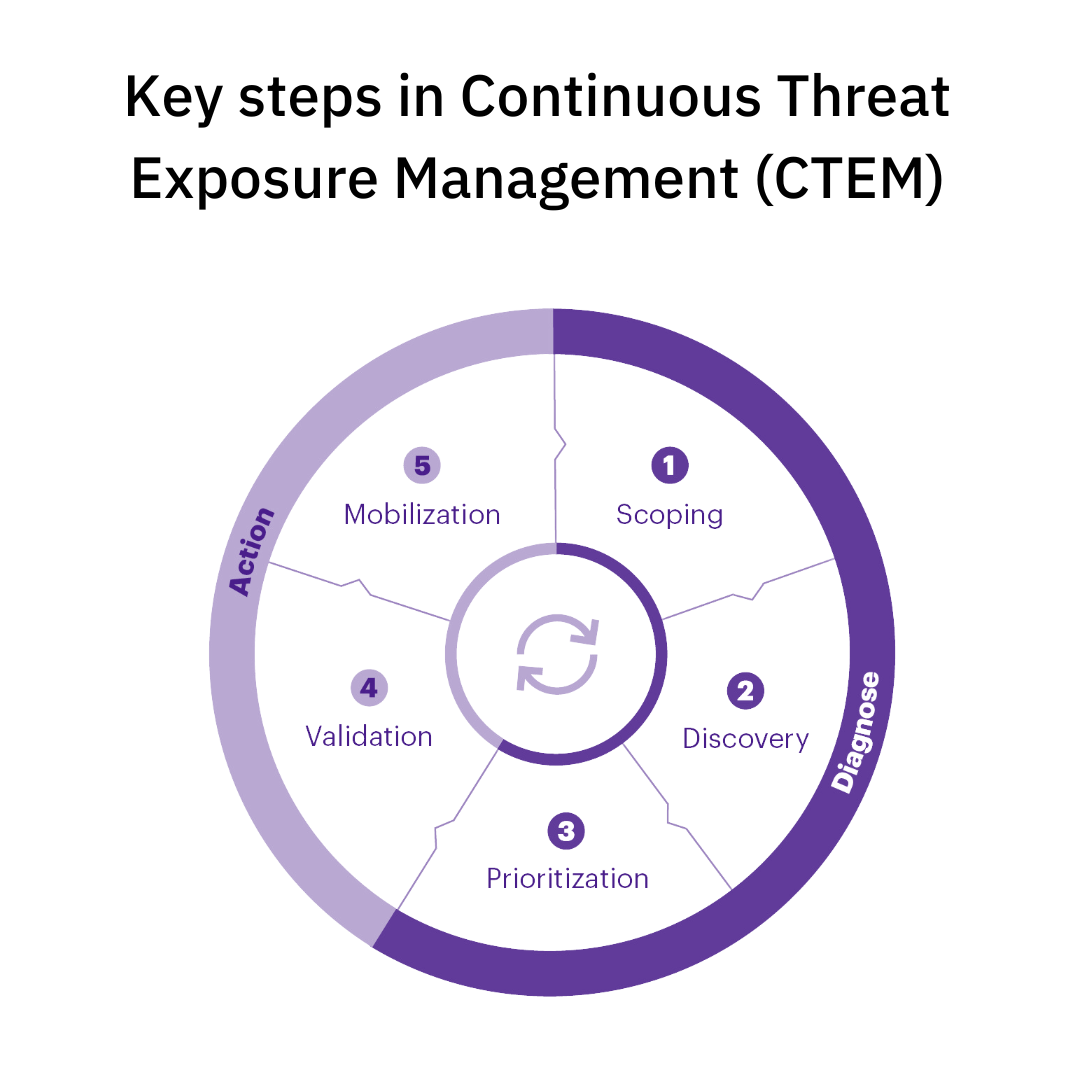
Stage 1: Scoping – Defining Your Critical Assets
- Identifying Key Attack Surfaces: This stage lays the groundwork by mapping your entire attack surface. This includes IT infrastructure, applications, data stores, and any other assets that could be exploited by attackers.
- Prioritizing Business Criticality: Not all assets are created equal. Here, you’ll collaborate with stakeholders across various departments (IT, Legal, Compliance, Development etc.) to determine the criticality of each asset to your business operations. This helps prioritize efforts and ensures you’re focusing on the most valuable targets for attackers.
- Adapting to Change: As your business grows and adapts, so do your security needs. A proactive approach is key. This initial scoping needs to be a continuous process. Regularly revisiting your attack surface and business priorities ensures your CTEM program remains relevant and effective.
Stage 2: Discovery – Uncovering Your Exposures
- Comprehensive Assessment: Move beyond just identifying individual vulnerabilities. This stage involves a deep dive into each asset to uncover all potential exposures. This includes misconfigurations, identity access controls within Active Directory, and other weaknesses that attackers could exploit.
- Understanding Attack Paths: Exposures rarely exist in isolation. Here, the focus is on analyzing how different exposures can be chained together. By understanding these potential attack paths, you can identify which assets are most at risk from a combined exploit attempt.
- Prioritization for Remediation: The sheer volume of potential exposures can be overwhelming. This stage helps prioritize discovery efforts by focusing on assets with the highest business criticality and the most concerning exposure combinations.
Stage 3: Prioritization – Focusing Your Efforts
- Risk-Based Approach: Large organizations have more exposures than they can realistically fix at once. This stage utilizes a risk-based approach, considering the severity of known threats targeting these exposures and the criticality of the impacted assets. This ensures you’re addressing the issues that pose the greatest overall risk.
- Beyond Vulnerabilities: Traditional prioritization often focused solely on vulnerabilities. It takes a more holistic approach, factoring in misconfigurations, identity risks, and how they contribute to the overall risk landscape.
- Attack Path Optimization: Prioritization goes beyond individual exposures. It considers how exposures can be chained together to form attack paths. By understanding these paths and the critical assets targeted, you can prioritize remediations that have the greatest impact on reducing overall risk.
Stage 4: Validation – Confirming the Threat
- Leveraging Tools: This stage employs various tools to validate the potential impact of identified exposures. These tools can help assess the likelihood of a successful exploit based on real-world threat intelligence.
- Prioritization Refinement: In some cases, the validation process can inform further prioritization in Stage 3. By confirming the exploitability of an exposure, you can refine your remediation focus on the most critical threats.
- Security Control Testing: Validation can also be used to test the effectiveness of existing security controls. This helps ensure your controls are actually mitigating the identified risks. It can also be used to automate periodic penetration testing, providing a continuous assessment of your security posture.
Stage 5: Mobilization – Taking Action
- Alignment and Ownership: This final stage ensures everyone involved understands their role and responsibilities within the CTEM program. Clear communication and collaboration between security teams and IT teams responsible for remediation are essential for success.
- Risk Reduction Value: Both security and IT teams benefit from a clear understanding of the risk reduction value associated with each remediation effort. This fosters collaboration and prioritizes efforts that deliver the most significant security improvements.
- Continuous Improvement: Mobilization involves establishing reporting mechanisms to track the overall effectiveness of the this program. These reports demonstrate the improvements made to your security posture over time, allowing you to continuously optimize your approach.
By following these five stages, you can establish a robust Continuous Threat Exposure Management program that continuously identifies, prioritizes, and addresses your organization’s security exposures. This proactive approach minimizes your attack surface and reduces the overall risk of a successful cyberattack.
How to Implement CTEM? – The Strobes Way
Implementing a Continuous Threat Exposure Management program can feel like a complicated task. But it doesn’t have to be with Strobes. Here’s a breakdown of the 5 phases of CTEM and how Strobes products – ASM, PTaaS, and RBVM can help you at each phase:
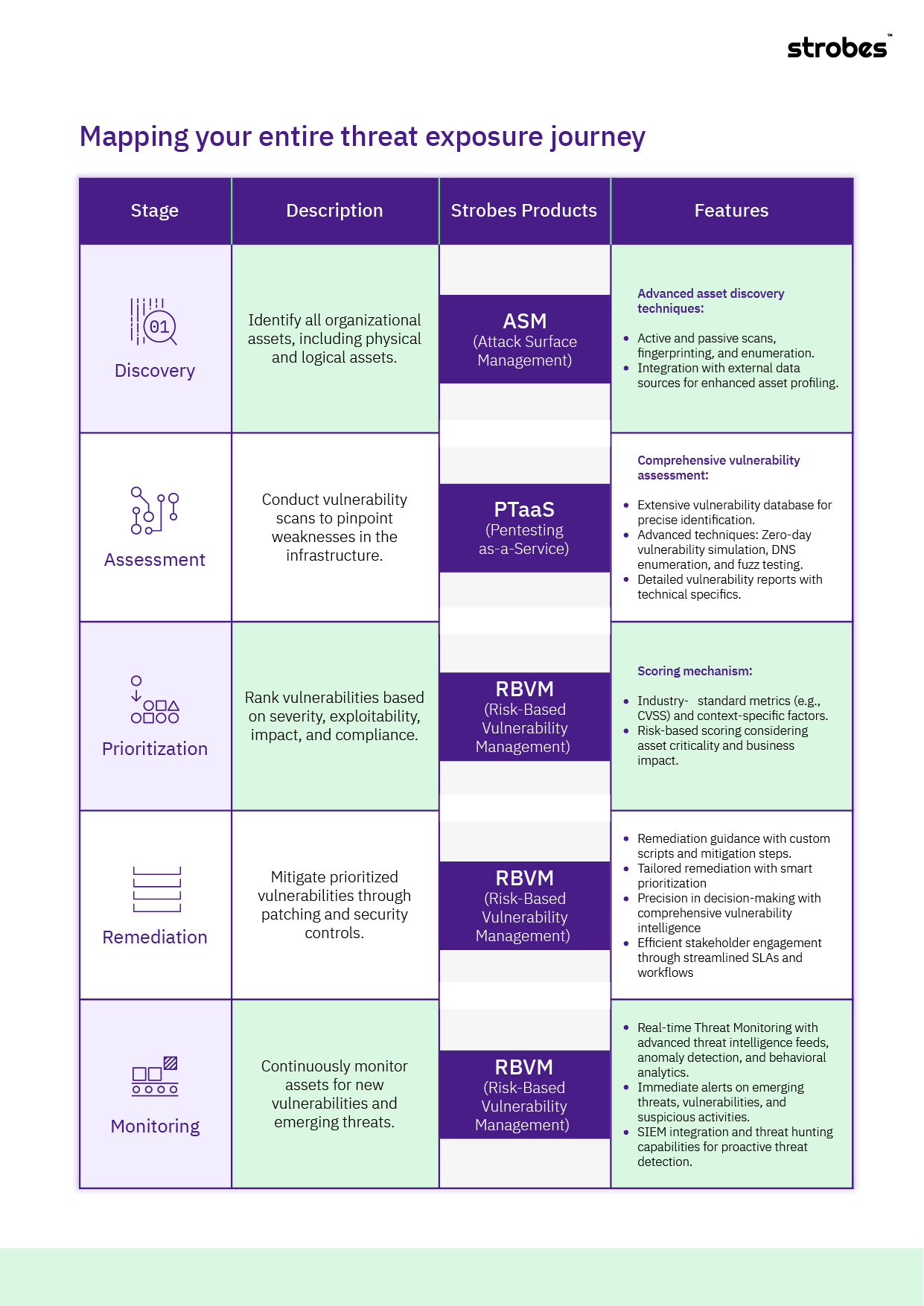
Discovery
- Strobes Product: ASM (Attack Surface Management)
- What it Does: Discovers all of your organization’s assets, including physical locations and computer systems. This is important because you can’t secure what you don’t know you have.
- How it Helps: ASM uses a combination of techniques to find all of your assets. This includes active and passive scans, where it sends signals out to see what responds and collects information about the devices, and integration with external data sources.
Assessment
- Strobes Product: PTaaS (Penetration Testing as a Service)
- What it Does: PTaaS performs a simulated cyberattack to identify weaknesses in your defenses.
- How it Helps: PTaaS goes beyond basic vulnerability scans to use advanced techniques to find zero-day vulnerabilities, those that the software vendors aren’t even aware of yet. This gives you a more complete picture of your security risks.
Prioritization
- Strobes Product: RBVM (Risk-Based Vulnerability Management)
- What it Does: Takes the data from the scans and assigns a severity score to each vulnerability. This score reflects how serious the vulnerability is, how easily it can be exploited and the impact it could have on your business.
- How it Helps: Vulnerability management helps you focus on the vulnerabilities that matter most. It analyzes how important the affected system is and the potential damage caused by an exploit. This lets you address the most critical issues first.
Remediation
- Strobes Product: RBVM (Risk-Based Vulnerability Management)
- What it Does: Provides guidance on how to fix the vulnerabilities that have been identified.
- How it Helps: RBVM offers specific recommendations on how to patch vulnerabilities and implement other security controls. It also provides custom scripts and mitigation steps to make the remediation process easier.
Monitoring
- Strobes Product: RBVM (Risk-Based Vulnerability Management)
- What it Does: Continuously monitors your assets for new vulnerabilities and emerging threats.
- How it Helps: RBVM keeps an eye on your systems so you don’t have to. It provides real-time alerts on new threats and suspicious activities so you can take action quickly.

Organizations with CTEM Vs Organizations Without CTEM
| When Organizations Implement CTEM | When Organizations Do Not Implement CTEM |
| Gain continuous visibility into their attack surface | Operate with a limited understanding of vulnerabilities |
| Prioritize remediation efforts based on real-world risk | Address vulnerabilities on a first-come, first-served basis |
| Proactively mitigate threats before they can be exploited | React to breaches and incidents after they occur |
| Optimize security posture for maximum effectiveness | Allocate resources inefficiently, potentially leaving gaps |
| Maintain a comprehensive understanding of external threats | Struggle to keep pace with the evolving threat landscape |
| Empower security teams with data-driven decision making | Rely on intuition and guesswork for threat mitigation |

How is CTEM different from other Threat Exposure Management Programs?
| Aspect | CTEM (Continuous Threat Exposure Management) | Traditional TEMs (Threat Exposure Management) |
| Methodology | Ongoing and continuous threat monitoring and assessment. | Periodic and scheduled threat assessments. |
| Scope | Comprehensive coverage of all assets, both physical and digital. | Often focuses primarily on digital assets. |
| Frequency | Continuous, real-time monitoring and assessment. | Periodic scans and assessments (e.g., quarterly). |
| Real-time Alerts | Provides real-time alerts for emerging threats and vulnerabilities. | May offer alerts but typically not in real-time. |
| Adaptation to Threats | Allows organizations to adapt to evolving threats quickly. | May not adapt as quickly between scheduled assessments. |
How to Choose the Right CTEM Vendor?
So, you’re ready to take your cybersecurity to the next level with Continuous Threat Exposure Management. Smart move! But with so many vendors out there, how do you find the one that’s the perfect fit for your company? Let’s break down some key questions to ask yourself when evaluating the vendors:
1. Can It Bend and Flex with Your Business? (Adapts to Your Environment)
Every company is unique, with its own IT infrastructure and security needs. A one-size-fits-all CTEM solution just won’t cut it. You need a vendor that can adapt to your specific environment, whether you’re a small startup or a sprawling enterprise. Ask yourself:
- Does the vendor offer customizable dashboards and reporting that align with my priorities?
- Can the solution integrate with my existing security tools? (We’ll get to that one in a sec!)
2. Does It See the Big Picture and the Tiny Details? (Broad Threat Coverage)
Imagine a thief trying to break into your house. They wouldn’t just check the front door, right? They’d look for weaknesses everywhere – windows, the back gate, even the dog door (if you have one!). A good continuous threat exposure management solution works the same way. It needs to go beyond basic vulnerabilities and identify a broad range of threats, including:
- Misconfigurations in your systems
- Identity and access management issues
- External threats lurking on the web
3. Can It Play Well with Others?( Integration)
No security tool exists in a silo. A strong CTEM solution should integrate well with other security products you use. This allows for a more holistic view of your security posture and avoids creating information gaps. Consider these questions:
- Will this solution integrate smoothly with my existing security tools?
- Does the vendor offer clear documentation and support to ensure a smooth integration process?
4. Does It Give You Actionable Intel? (Actionable Insights)
There’s nothing worse than a security tool that just throws a bunch of alerts your way without any clear direction. A good CTEM solution should provide actionable insights that help you prioritize and remediate threats quickly. Here’s what to ask yourself:
- Does this solution offer clear and concise information about each identified threat?
- Does it prioritize risks based on severity and potential impact, helping me focus on the most critical issues first?
5. Is it always on the job, or does it take long coffee breaks? (Continuous Monitoring)
Cybersecurity threats don’t take breaks, and neither should your CTEM solution. Look for a vendor that offers continuous monitoring, meaning it’s constantly scanning your environment for vulnerabilities and suspicious activity. Ask yourself:
- Does this solution provide 24/7 monitoring, ensuring I’m always aware of potential threats?
- Does it offer real-time alerts so I can take immediate action when needed?
6. Can I Count on Them? (Customer Support)
Let’s be honest, even the best continuous threat exposure management platform needs a helping hand sometimes. When you have a question or run into a snag, you need a reliable support team that can get you back on track quickly. So, ask yourself:
- Does the vendor offer multiple support channels (phone, email, live chat)?
- How quickly do they typically respond to inquiries?
- Do they have different support tiers for different needs (basic vs. premium)?
A strong support team is an essential part of any CTEM solution. After all, you want to feel confident that you have the backup you need when you need it most.
7. Can I Understand What’s Going On? (Clear Reporting)
A continuous threat exposure management platform is all about giving you clear visibility into your security posture. But what good is that visibility if the reports you get are confusing or cluttered? Here’s what you need to consider:
- Does the platform offer customizable reports that you can tailor to your specific needs?
- Are the reports easy to understand, even for non-technical users?
- Can you drill down into specific details for further investigation?
Clear and concise reporting is key to making informed decisions about your security strategy. You shouldn’t have to become a data analyst just to understand what your CTEM platform is telling you.
8. Is This Easy to Use? (User-Friendly Platform)
A complex and clunky CTEM platform can quickly become a burden on your IT team. The ideal solution should be intuitive and user-friendly, allowing your team to get up and running quickly with minimal training. Here are some questions to ask:
- Does the platform offer a clean and easy-to-navigate interface?
- Can users with varying technical skill sets comfortably use the platform?
- Does the vendor offer training resources to help your team get the most out of the platform?
A user-friendly platform will save you time and resources in the long run. Your team should be focusing on shoring up your defenses, not wrestling with a complicated interface.
9. Can It Grow With Us? (Scalability)
Your business needs are constantly evolving, and your continuous threat exposure management solution should be able to keep pace. Look for a platform that can scale to accommodate your growing security needs. Consider these factors:
- Can the platform handle an increasing number of devices and users?
- Does it offer the flexibility to integrate with other security tools you might use?
- Can the vendor accommodate your future security requirements?
A scalable continuous threat exposure management solution will ensure that you have the protection you need today and well into the future.
10. Proven Results Speak Volumes (Track Record)
When it comes to cybersecurity, experience matters. Look for a vendor with a proven track record of success. Here are some things to consider:
- Does the vendor have a good reputation within the cybersecurity industry?
- Do they have experience working with companies in your industry?
- Can they provide case studies or testimonials from satisfied customers?

Taking Action: The First Step to a More Secure Future
Now, you might be wondering where to begin. The good news is, continuous threat exposure management is a scalable solution. You can start small, focusing on specific areas like external attack surface management or prioritizing vulnerabilities. As you gain confidence and expertise, you can expand your CTEM program to encompass a wider range of security needs.
The most important thing is to take action. By implementing a continuous threat exposure management strategy, you’re taking a proactive approach to securing your organization’s data and critical assets. It’s an investment in your future, a commitment to building a stronger, more resilient security posture.
Related Reads
- CTEM for SaaS Security Leaders: A Practical Guide
- How CTEM Enhances Threat Prioritization in Complex Networks
- How CTEM Impacts Cyber Security Insurance Premiums?
- Key CTEM Metrics: Measuring the Effectiveness of Your Continuous Threat Exposure Management Program
- The Evolving Landscape of Security: From Vulnerability Management to CTEM
- Solution- One Platform For All The Offensive Security Needs
Frequently Asked Questions
1. What is the primary goal of CTEM?
The primary goal of CTEM is to give you a clear and up-to-date picture of your organization’s security vulnerabilities. It goes beyond just identifying weaknesses; it continuously monitors for threats that could exploit those vulnerabilities. This allows you to prioritize your security efforts and take action before attackers do.
2. What does CTEM focus on?
CTEM focuses on providing real-time insights into your attack surface. This includes your internal systems, external assets, and even third-party vendors. By having a comprehensive view, you can identify potential weaknesses that attackers might target. Additionally, CTEM incorporates threat intelligence to understand the latest tactics and techniques used by cybercriminals. This allows you to proactively address threats before they become a problem.
3. What are the benefits of implementing CTEM?
There are several benefits to implementing CTEM. It can help you:
- Reduce your risk of a cyberattack: By proactively addressing vulnerabilities, you make it harder for attackers to gain a foothold in your systems.
- Improve your security posture: It provides a comprehensive view of your security landscape, allowing you to identify and address weaknesses.
- Optimize your security resources: By prioritizing threats based on real-time data, you can allocate your security resources more efficiently.
- Meet compliance requirements: Many regulations require organizations to have a comprehensive understanding of their security risks. It can help you meet these requirements.
4. How can I get started with CTEM?
Implementing CTEM can be a straightforward process. Here are a few steps to get started:
- Assess your current security posture: This will help you identify areas where CTEM can provide the most benefit.
- Choose a CTEM solution: There are a variety of CTEM solutions available. Choose one that meets the specific needs of your organization.
- Integrate CTEM with your existing security tools: This will allow you to get the most out of your investment.
While these steps seem straightforward, effectively implementing them often requires specialized skills and ongoing management.
Certified ethical hackers play a crucial role in penetration testing and threat modeling, which are valuable aspects of CTEM.
To ensure a successful CTEM implementation and maximize its effectiveness, partnering with a qualified continuous threat exposure management provider is highly recommended.
5. Should I Consider a CTEM Partner?
Yes. Partnering with a CTEM provider offers several advantages:
- Expertise and Experience: Leading CTEM providers have extensive experience in implementing and managing CTEM solutions. They can bridge any skill gaps within your security team.
- Scalability and Cost-Effectiveness: Partnering can be more cost-effective than building in-house expertise. Providers offer ongoing support and updates, ensuring your continuous threat exposure management solution remains efficient.