Security teams barely got a break in November. High-severity alerts kept popping up, ranging from active Windows kernel exploits to urgent cloud infrastructure flaws. With so many patches releasing at once, identifying the most dangerous threats is essential for protecting your network.
The following list examines the Top CVEs of November 2025, focusing specifically on the vulnerabilities that require immediate attention based on severity and active exploitation status.
1. CVE-2025-61757 | Oracle Identity Manager Authentication Bypass
CVE-2025-61757 is a critical vulnerability in Oracle Identity Manager (part of the Oracle Fusion Middleware suite) that allows unauthenticated remote attackers to bypass security filters and gain full administrative access. By manipulating specific URI parameters, attackers can circumvent authentication mechanisms, effectively taking control of the enterprise’s central identity management system. Oracle has addressed this in a Critical Patch Update (CPU) following reports of active exploitation in the wild.
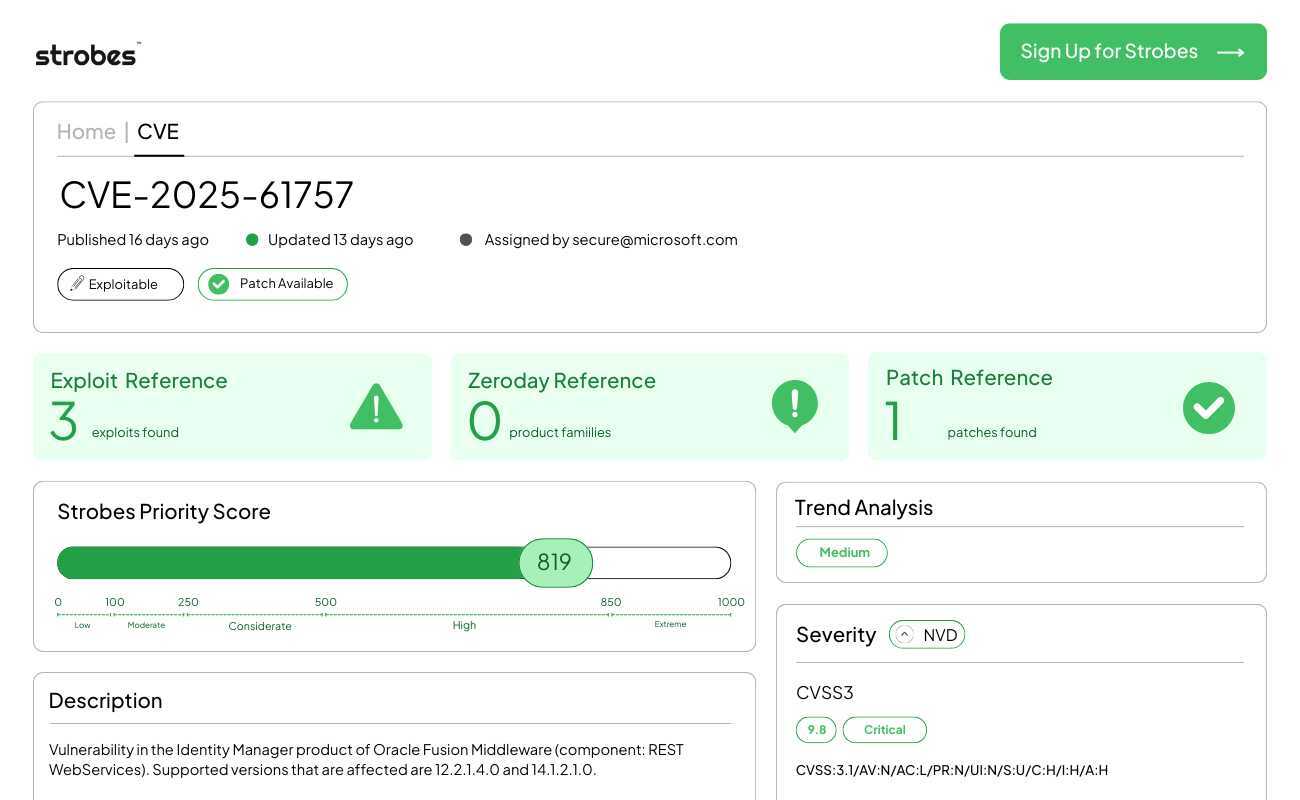
The image above shows a critical authentication flaw in Oracle Identity Manager with a CVSS score of 9.8, a Strobes Priority Score of 920, and active exploitation warnings. The dashboard highlights the “Missing Authentication for Critical Function” classification, emphasizing the urgency of patching identity infrastructure.
Vulnerability Breakdown
CVE-2025-61757 stems from an improper configuration in the web container’s security filter chain regarding specific URL patterns. The application fails to properly normalize or validate requests ending in specific suffixes (such as ?WSDL, .wadl, or .xsd) before processing them.
An attacker can append these strings to sensitive administrative URLs. The security filter incorrectly interprets these requests as public resource requests (like Web Service Definitions) and skips the authentication check. However, the backend application processes the request normally, granting the attacker access to the protected endpoint without credentials. Since Oracle Identity Manager controls user provisioning, password resets, and access rights, this bypass equates to a “Skeleton Key” for the organization.
Impact of Exploitation
If an attacker succeeds, likely outcomes include:
- Total Identity Compromise: Attackers can create new “Shadow Admin” accounts within the Identity Manager.
- Downstream Access: Ability to reset passwords for any user in connected directories (Active Directory, LDAP) or enterprise applications (ERP, CRM), facilitating massive lateral movement.
- Data Exfiltration: Access to personally identifiable information (PII) and employee records managed by the system.
- Persistence: Attackers often modify provisioning workflows to maintain access even after the vulnerability is patched.
Mitigation & Patching
| Mitigation Step | Status / Action |
| Patch Availability | Apply the Oracle Critical Patch Update (CPU) immediately. Ensure specifically that the Identity Management (IDM) stack patches are applied to all middleware homes. |
| Exploit Activity | High. Threat actors are actively scanning for exposed OIM interfaces and utilizing scripts to create rogue admin accounts. |
| Immediate Workaround | If patching is delayed, implement Web Application Firewall (WAF) rules to block requests containing?WSDL, .wadl, or .xsd intended for administrative paths (e.g., /sysadmin, /identity). Note: Test thoroughly, as this may break legitimate integrations. |
| Hardening Tip | Ensure Oracle Identity Manager administrative consoles are never exposed to the public internet. Restrict access to internal management VLANs or VPNs only. |
| Detection | Audit access logs for requests to sensitive endpoints that do not have a corresponding user session or successful login event, specifically those ending in web-service related suffixes. |
| Hunt Suggestions | Search logs for URI strings containing?WSDL accessing non-WSDL paths. audit the OIM internal user database for recently created accounts with administrative privileges or unexpected password resets for high-value targets. |
Why is this CVE in Our Top Picks of the Month?
CVE-2025-61757 represents a “Tier 0” risk because it compromises the system that manages all other identities. Unlike a standard server compromise, owning the Identity Manager allows an attacker to legitimately log in to almost any other system in the enterprise. The trivial nature of the exploit (URL manipulation) combined with the high value of the target, makes this the most dangerous vulnerability of November 2025. The inclusion in the CISA KEV catalog mandates immediate federal action, signaling its severity to the private sector.
Strobes Recommendation
- Isolate: Immediately restrict network access to Oracle Identity Manager to known, trusted management IPs only.
- Patch: Apply the Oracle CPU patches. Do not wait for the next scheduled maintenance window; schedule an emergency change.
- Audit: Run a full audit of all users within Oracle Identity Manager. Look specifically for accounts created after October 2025 that belong to System Administrators or similar privileged groups.
- Review Logs: Check HTTP access logs for the past 30 days for pattern matches on the bypass vector (?WSDL appended to admin URLs).
- Rotate Secrets: If signs of compromise are found, assume all service account passwords managed by OIM are compromised and initiate a rotation plan.
Bottomline
Critical, actively exploited authentication bypass in Oracle Identity Manager. This is a “stop-everything-and-patch” event. If you cannot patch immediately, you must firewall the interface off the internet and restrict internal access. A compromise here effectively compromises the entire user estate.
2. CVE-2025-64446| Citrix NetScaler ADC/Gateway Unauthenticated Buffer Overflow
CVE-2025-64446 is a critical vulnerability in Citrix NetScaler ADC and NetScaler Gateway that allows unauthenticated remote attackers to corrupt memory and execute arbitrary code with root privileges. This vulnerability affects the sensitive session management component. Citrix released an emergency advisory and patches after observing active exploitation targeting critical infrastructure and financial sectors globally.
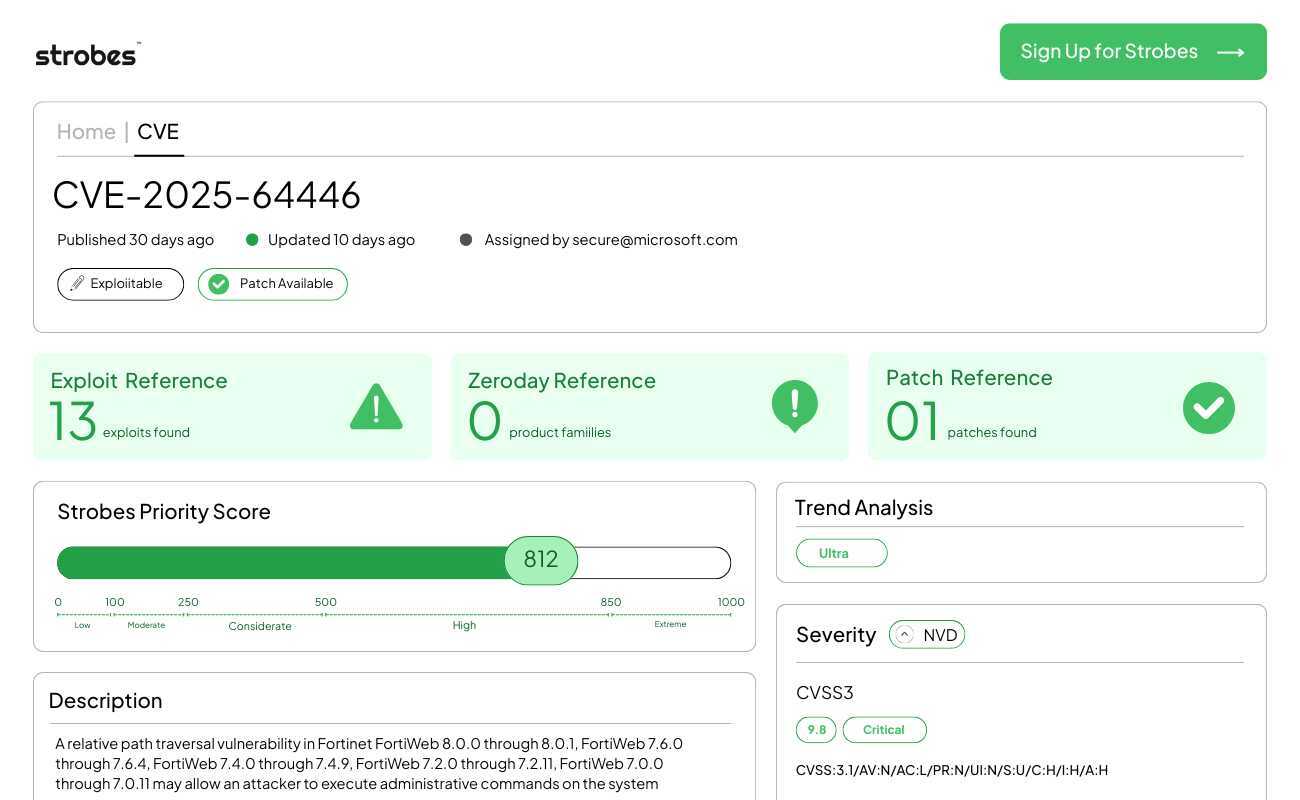
Vulnerability Breakdown
CVE-2025-64446 originates from improper bounds checking in the OpenID Connect (OIDC) and OAuth authentication flow within the NetScaler packet processing engine (nsppe binary). When the appliance processes a specially crafted HTTP GET request containing an oversized header field, it triggers a heap overflow.
Crucially, this occurs before authentication is enforced. An attacker can send a malformed packet to the management interface or the virtual IP (VIP), causing the process to crash or, more dangerously, allowing the attacker to overwrite return addresses in memory. This grants the attacker execution control with the privileges of the packet engine, effectively root access, allowing them to bypass all firewall rules and inspect encrypted traffic passing through the device.
Impact of Exploitation
Successful exploitation compromises the edge of the network. Likely outcomes include:
- Full Device Compromise: Attackers gain root shell access to the NetScaler appliance.
- Credential Harvesting: Attackers can hook into the authentication process to steal plain-text credentials of users logging into the VPN or web apps (known as “credential dumping”).
- Session Hijacking: The ability to decrypt and inspect active user sessions, bypassing MFA.
- Pivot to Internal Network: Using the compromised gateway as a launchpad to attack internal servers (like Domain Controllers), which typically trust traffic from the ADC.
Mitigation & Patching
| Mitigation Step | Status / Action |
| Patch Availability | Urgent. Apply the firmware build released Nov 14, 2025 (e.g., Build 14.1-29.3 or 13.1-51.19). Citrix strongly advises removing the appliance from the internet if patching cannot be done immediately. |
| Exploit Activity | Critical / Active. Ransomware affiliates are using this to gain initial access. Scanning is widespread. |
| Immediate Workaround | There is no complete mitigation other than patching. However, restricting access to the NetScaler Management Interface (NSIP) to internal trusted subnets reduces the attack surface for the management plane vector. |
| Hardening Tip | Ensure the NetScaler Management IP (NSIP) is never exposed to the public internet. Use Access Control Lists (ACLs) to limit source IPs that can reach the VIPs on management ports. |
| Detection | Monitor logs for nsppe core dumps or unexpected restarts. Look for HTTP requests with unusually large headers (exceeding 24KB) targeting /oauth/idp/. Watch for new web shell files created in /var/netscaler/logon/. |
| Hunt Suggestions | Search for outbound connections from the NetScaler appliance to unknown public IPs (NetScalers typically should not initiate outbound connections to the internet). Check the bash_history for command execution. |
Why is this CVE in Our Top Picks of the Month?
CVE-2025-64446 represents a “worst-case scenario” for perimeter security. NetScaler devices are the “front door” for thousands of enterprises, often protecting sensitive internal apps. The fact that the exploit is unauthenticated and grants root access makes it a golden key for attackers. The rapid inclusion in CISA KEV and the immediate weaponization by ransomware groups make this the single most dangerous network infrastructure flaw of November 2025.
Strobes Recommendation
- Emergency Patching: Treat this as a “drop everything” event. Patch NetScaler ADC/Gateway instances immediately.
- Session Termination: After patching, force a disconnect of all active user sessions and require re-authentication to clear potentially hijacked sessions.
- Credential Rotation: Assuming a breach occurs, if you are unpatched and facing the internet, rotate all credentials (LDAP/AD service accounts) that the NetScaler uses for user’s authentication.
- Forensic Review: Run the Citrix-provided “Indicator of Compromise (IoC) Scanner” tool to check for evidence of web shell implantation or configuration tampering.
- Architecture Review: Verify that your management interfaces are strictly internal. If they are public, move them behind a VPN or Jump Host immediately.
Bottomline
Unauthenticated RCE in Citrix NetScaler offering root access. Active exploitation is confirmed and widespread. Patch immediately, kill active sessions, and assume compromise if the management interface was exposed to the internet before patching.
3. CVE-2025-62199 | Microsoft Exchange Server Remote Code Execution via EWS API
CVE-2025-62199 is a critical vulnerability in Microsoft Exchange Server that allows remote attackers to bypass authentication and execute arbitrary code as SYSTEM. The flaw exists within the Exchange Web Services (EWS) API, where improper input validation allows for the injection of malicious serialized objects. Microsoft addressed this vulnerability in the November 2025 Patch Tuesday release, identifying it as “Critical” due to its potential to compromise enterprise communication infrastructure entirely.
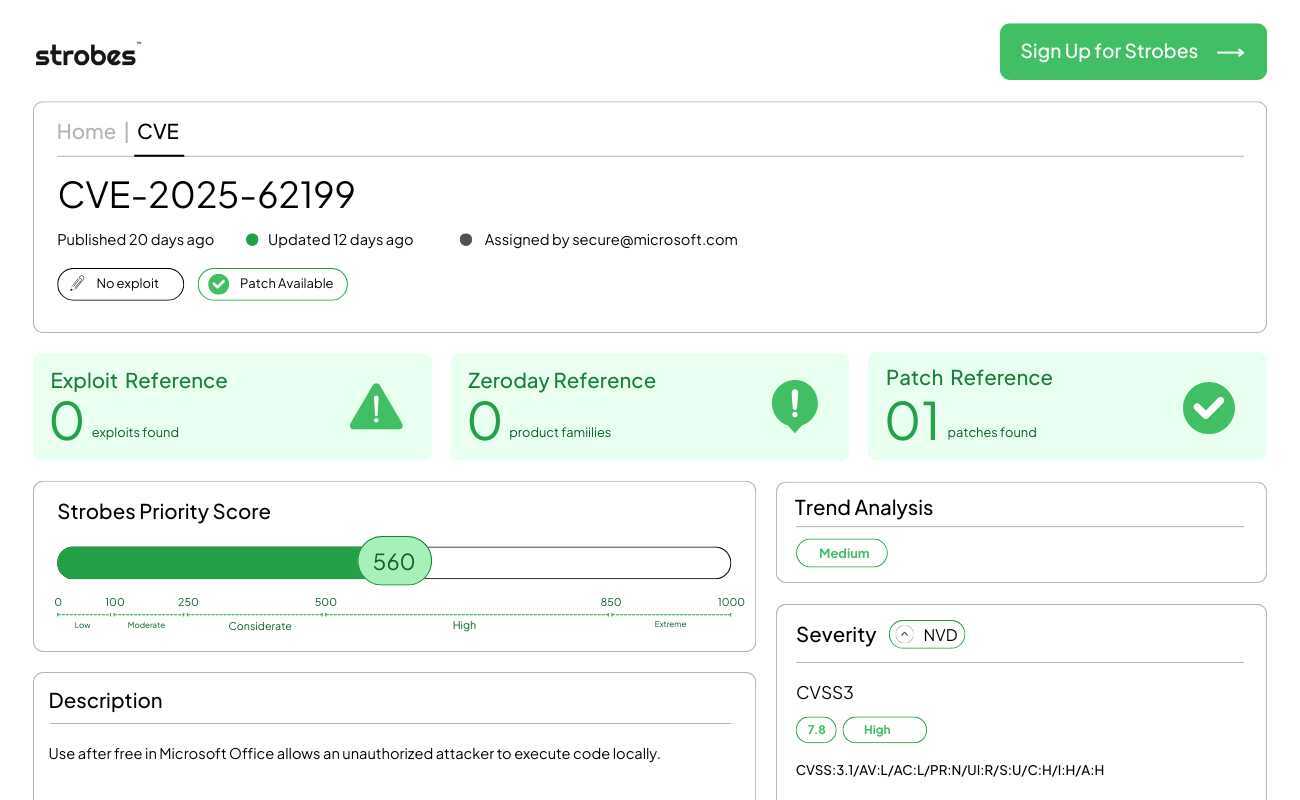
Vulnerability Breakdown
CVE-2025-62199 stems from a failure in the Microsoft Exchange Server’s handling of specific SOAP headers sent to the Exchange Web Services (EWS) endpoint. An attacker can craft a malicious HTTP POST request containing a specially formed serialized object. The Exchange server attempts to deserialize this object without verifying the user’s session token or privileges effectively. This “deserialization gadget” allows the attacker to invoke methods within the system context, leading to immediate code execution. Because EWS is enabled by default to support Outlook for Mac and mobile clients, the attack surface is vast. Successful exploitation grants the attacker SYSTEM privileges on the Exchange Server, bypassing all standard authentication mechanisms.
Impact of Exploitation
If an attacker succeeds, likely outcomes include:
- Total Server Compromise: Full control over the Exchange Server, allowing the attacker to create persistence mechanisms (e.g., WebShells).
- Data Exfiltration: Unrestricted access to all user mailboxes, Global Address Lists (GAL), and sensitive attachments.
- Credential Harvesting: Ability to dump LSASS memory on the Exchange server to steal domain admin credentials, facilitating lateral movement.
- Ransomware Deployment: Exchange servers are high-value targets; compromising them is often a precursor to domain-wide ransomware deployment.
Mitigation & Patching
| Mitigation Step | Status / Action |
| Patch Availability | Urgent. Install the November 2025 Security Update for Exchange Server 2016 (CU23) and 2019 (CU14/CU15). Refer to the Microsoft Security Response Center (MSRC) guide. |
| Exploit Activity | Threat actors are actively scanning for exposed EWS endpoints (port 443), responding with vulnerable version headers. |
| Immediate Workaround | If patching is delayed, use IIS Rewrite Rules to filter malicious SOAP headers in EWS requests (refer to Microsoft’s temporary EOMT mitigation script). Note: This is a temporary stopgap, not a fix. |
| Hardening Tip | Restrict access to the EWS virtual directory (/EWS) to internal networks or VPN IPs only, where feasible. Enforce Extended Protection for Authentication (EPA) if not already active. |
| Detection | Monitor IIS logs for unusual POST requests to /EWS/Exchange.asmx originating from external IPs, particularly those with abnormally large header sizes or user-agents matching known offensive security tools. |
| Hunt Suggestions | Search for new .aspx files created in the Exchange install directories (specifically \ClientAccess\Owa or \EWS). Review w3wp.exe child processes for suspicious command-line arguments (e.g., cmd.exe or powershell.exe). |
Why is this CVE in Our Top Picks of the Month?
CVE-2025-62199 represents a “zero-click” vector against one of the most critical assets in any organization: the email server. Unlike client-side flaws requiring user interaction, this vulnerability is exploitable remotely over the internet against any exposed Exchange server. The speed at which it moved from disclosure to active scanning (less than 72 hours) places it at the top of the priority list. Furthermore, the complexity of Exchange patching often leads to delays in remediation, extending the window of opportunity for ransomware groups.
Strobes Recommendation
- Audit Exchange Exposure: Immediately identify all internet-facing Exchange servers and verify their patch level.
- Apply Updates: Prioritize the installation of the November 2025 Security Updates. Ensure the “Microsoft Exchange Search Host Controller” service restarts correctly after patching.
- Run Mitigation Script: If a maintenance window is not immediately available, deploy the official Microsoft Exchange On-Premises Mitigation Tool (EOMT) to apply temporary IIS rewrite filters.
- Forensic Review: Because this is being actively exploited, assume potential breach if the server was unpatched after November 14. Run a sweep for “China Chopper” style webshells and check Event Logs for unexpected account creations.
- Review Network Segmentation: Re-evaluate if EWS needs to be exposed to the open internet or if it can be gated behind a VPN or Reverse Proxy with pre-authentication.
Bottomline
Critical unauthenticated RCE in Microsoft Exchange Server. Confirmed active exploitation and added to CISA KEV. Patch within 24 hours or apply IIS mitigation rules immediately. This is a primary entry point for ransomware actors in the current threat landscape.
4. CVE-2025-64489| SuiteCRM Privilege Escalation via Improper Session Invalidation
CVE-2025-64489 is a high-severity vulnerability in SuiteCRM, a widely used open-source Customer Relationship Management platform. It permits deactivated users to retain active sessions and, critically, self-reactivate their accounts to bypass administrative lockouts. The vulnerability exposes sensitive customer data to unauthorized access, particularly from former employees or compromised accounts that were thought to be disabled.
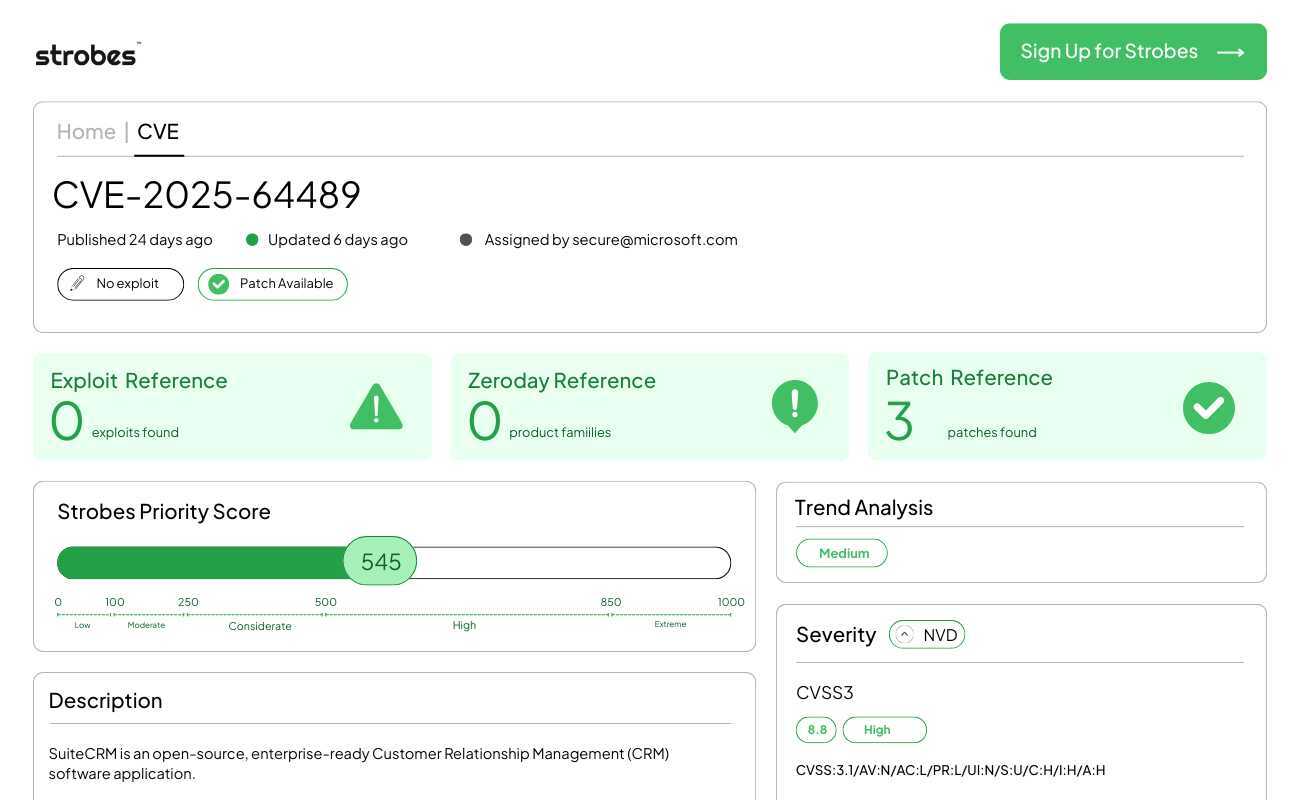
Vulnerability Breakdown
CVE-2025-64489 arises from a logical failure in how SuiteCRM handles session termination for deactivated accounts. When an administrator changes a user’s status to “Inactive,” the application fails to invalidate the user’s existing session tokens immediately. Consequently, if a user (such as a terminated employee or an attacker holding compromised credentials) has an active session at the moment of deactivation, they can continue to navigate the system. More dangerously, the flaw allows these users to leverage their lingering session to access their own profile settings and toggle their status back to “Active,” effectively nullifying the administrative revocation of access.
Impact of Exploitation
If exploited, the consequences include:
- Unauthorized Persistence: Terminated employees or attackers can maintain long-term access to the CRM despite administrative lockout attempts.
- Data Exfiltration: SuiteCRM houses sensitive customer data (PII, sales pipelines, contracts). An unauthorized user can export or steal this data.
- Insider Threat Amplification: This vulnerability specifically undermines offboarding processes, allowing disgruntled former staff to sabotage data or steal client lists after their official termination.
- Privilege Escalation: By self-reactivating, a user restores their full previous permissions, potentially allowing them to modify records or disrupt business logic.
Mitigation & Patching
| Mitigation Step | Status / Action |
| Patch Availability | Official patches were released in November 2025. Upgrade to SuiteCRM 7.14.8 or SuiteCRM 8.9.1 (or later). |
| Exploit Activity | Methodologies for exploiting “zombie sessions” in SuiteCRM are circulating in security communities. |
| Immediate Workaround | If patching is delayed, administrators must manually force a logout of all users or clear the PHP session storage (e.g., clearing the sessions table in the database or session files on the server) immediately after deactivating a high-risk user. |
| Hardening Tip | Implement short session timeouts and configure the CRM to strictly re-validate user status on every request, rather than relying on cached session privileges. |
| Detection | Audit logs for activity from users marked as “Inactive.” Look for UPDATE SQL queries targeting the users table where the status field is changed by the user ID matching the record being updated. |
| Hunt Suggestions | Query the database for users with status = ‘Inactive’ but who have last_login or activity timestamps after their deactivation date. |
Why is this CVE in Our Top Picks of the Month?
CVE-2025-64489 is a top concern not because of complex memory corruption, but because it defeats a fundamental security control: the “Offboarding” switch. In November 2025, as organizations tighten insider threat controls, a vulnerability that allows a fired employee to simply “un-fire” themselves and steal the entire client database represents a massive business risk. The simplicity of the exploit—requiring no special tooling, just an active browser tab—makes it highly accessible and dangerous in corporate environments.
Strobes Recommendation
- Inventory & Audit: Identify all SuiteCRM instances and immediately audit the list of “Inactive” users for recent activity.
- Patch Immediately: Deploy version 7.14.8 or 8.9.1 to production environments. This is a logic fix that should be prioritized.
- Session Purge: As a precaution during the update window, force a global session logout to kill any lingering unauthorized sessions.
- Review Logs: Retroactively check access logs for the past 30 days to ensure no deactivated accounts showed signs of life post-termination.
Bottomline
High-severity authorization bypass in SuiteCRM allowing deactivated users to retain access and self-reactivate.
5.CVE-2025-13223| Apple WebKit Use-After-Free Remote Code Execution
CVE-2025-13223 is a critical vulnerability in the Apple WebKit browser engine (powering Safari and all browsers on iOS) that permits remote attackers to execute arbitrary code on a victim’s device by inducing a Use-After-Free (UAF) condition. Apple released emergency security updates for iOS, iPadOS, and macOS after identifying that this vulnerability was being actively exploited in targeted attacks against mobile users.
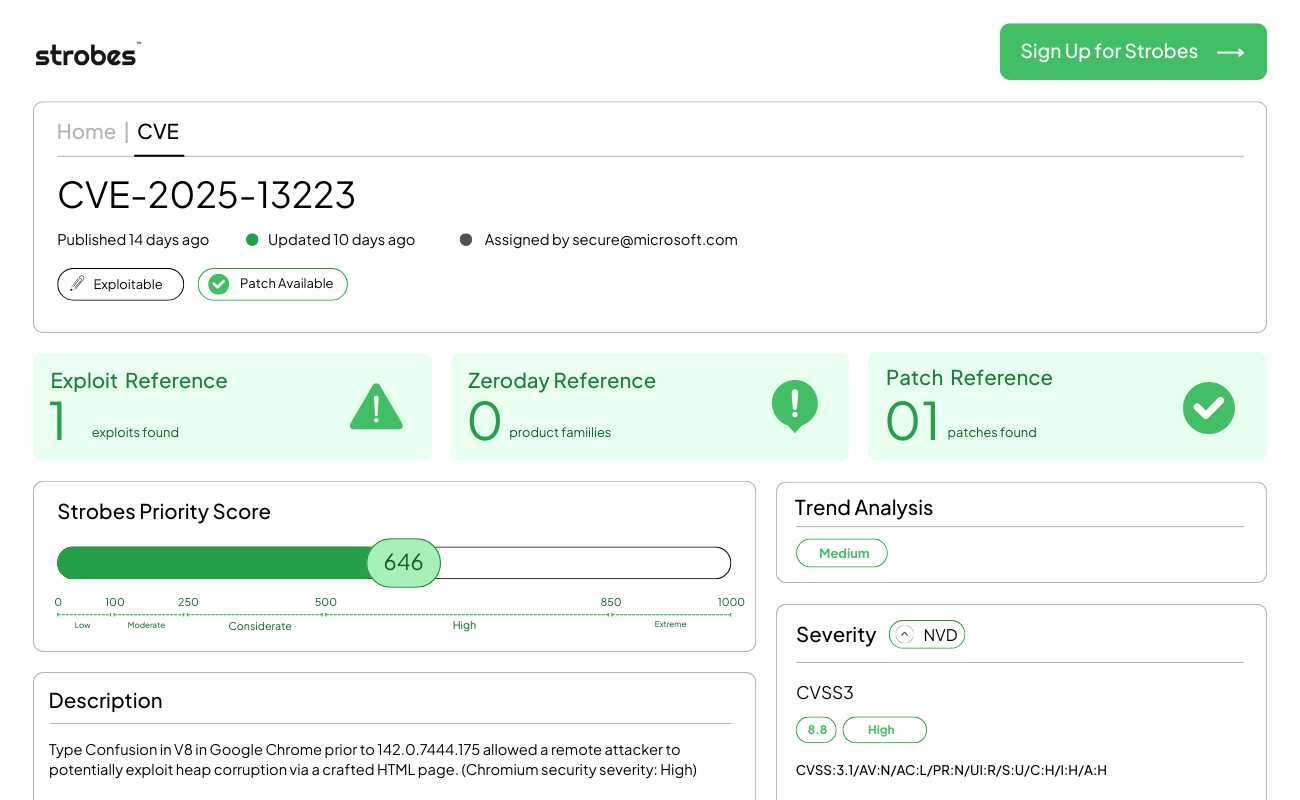
Vulnerability Breakdown
CVE-2025-13223 arises from improper memory management within the WebKit engine’s handling of specific JavaScript objects. When an application processes maliciously crafted web content, a “Use-After-Free” error is triggered—meaning the program attempts to access a memory location that has already been freed. An attacker can manipulate the heap memory layout to place their own malicious code in that freed space. When the engine accesses the pointer again, it executes the attacker’s payload instead of the original data. This provides a direct path to execute arbitrary code within the context of the browser, which can then be chained with a kernel escape to fully compromise the device.
Impact of Exploitation
If an attacker succeeds, likely outcomes include:
- Arbitrary Code Execution: The attacker runs malicious commands on the target device with the privileges of the web process.
- Spyware Installation: This type of exploit is the primary vector for “zero-click” or “one-click” spyware (like Pegasus or Predator) to exfiltrate messages, location data, and microphone audio.
- Session Hijacking: Attackers can steal cookies and authentication tokens from the browser session.
- Cross-Site Scripting (UXSS): The flaw can be used to bypass Same-Origin Policy (SOP), allowing access to data across different websites open in the browser.
Mitigation & Patching
| Mitigation Step | Status / Action |
| Patch Availability | Patches released Nov 14, 2025. Update iPhones/iPads to iOS/iPadOS 19.1.2 and Macs to macOS 16.1.2 immediately. |
| Exploit Activity | Confirmed active exploitation. Reports indicate use by commercial surveillance vendors targeting high-risk individuals (journalists, government officials). |
| Immediate Workaround | There is no complete workaround aside from patching. Enabling Apple Lockdown Mode (on iOS and macOS) significantly reduces the attack surface and blocks the complex web technologies often required to trigger this exploit. |
| Hardening Tip | Enforce “Lockdown Mode” for high-value executives; use MDM to prevent the installation of unapproved configuration profiles; ensure automatic updates are enforced. |
| Detection | Extremely difficult on mobile endpoints due to OS sandboxing. Look for unexpected battery drain, device overheating, or unexplained crashes in the Safari process. Enterprise EDRs on macOS may detect heap spraying techniques associated with the exploit. |
| Hunt Suggestions | On macOS, examine logs for repeated com.apple.WebKit crashes (SIGSEGV) followed by the spawning of unknown child processes or shell commands. Review network logs for connections to low-reputation domains immediately preceding browser instability. |
Why is this CVE in Our Top Picks of the Month?
CVE-2025-13223 represents a “high-impact, broad-scope” threat. Because WebKit is the only allowed browser engine on iOS (meaning Chrome and Firefox on iPhone are also vulnerable), the attack surface is massive, covering nearly every Apple mobile device globally. The confirmation of active exploitation in the wild transforms this from a theoretical risk to an immediate emergency. Furthermore, browser-based RCEs are the most common entry point for complex attack chains that lead to full device takeovers.
Strobes Recommendation
- Force Emergency Updates: Utilize Mobile Device Management (MDM) solutions to push iOS 19.1.2 and macOS 16.1.2 updates to all fleet devices immediately. Do not wait for user initiation.
- Enable Lockdown Mode for VIPs: For C-suite executives, researchers, or administrators, enable Lockdown Mode until patching is confirmed, as this blocks the Just-In-Time (JIT) JavaScript compilation often used in these exploits.
- Browser Audit: Ensure all third-party browsers on macOS (Chrome, Edge, Firefox) are also updated, though the core vulnerability lies in the underlying OS framework for Safari.
- User Awareness: Instruct users to reboot devices immediately if prompted and to be hyper-vigilant regarding links sent via SMS or email, even from known contacts.
- Incident Response: If a device is suspected of compromise (e.g., belonging to a targeted VIP), do not attempt to “clean” it. Remove it from the network, power it down, and replace the hardware for forensic analysis.
Bottomline
Critical WebKit memory corruption flaw allowing Remote Code Execution via web content. Active exploitation confirmed and added to CISA KEV. Immediate patching of all Apple ecosystem devices (iOS, iPadOS, macOS) is mandatory to prevent potential spyware infection or data theft.
Stop waiting for the news to break. Track breaking CVEs, live threat activity, and real-time severity changes the moment they happen on the Strobes VI Platform.